Introduction
I’ve been encrypting my Windows 11 devices using an Endpoint security disk encryption policy for a while now and haven’t had any issues. That’s until today.
Turns out there’s a known issue around this, which I haven’t encountered until now.
If the device in question doesn’t support Modern Standby, you will have to combine the ‘old’ Endpoint protection policies with the new Endpoint security policies. My findings down below.
If the device is HSTI-compliant but doesn’t support Modern Standby, an endpoint protection policy has to be configured to enforce silent BitLocker drive encryption
Preliminary details
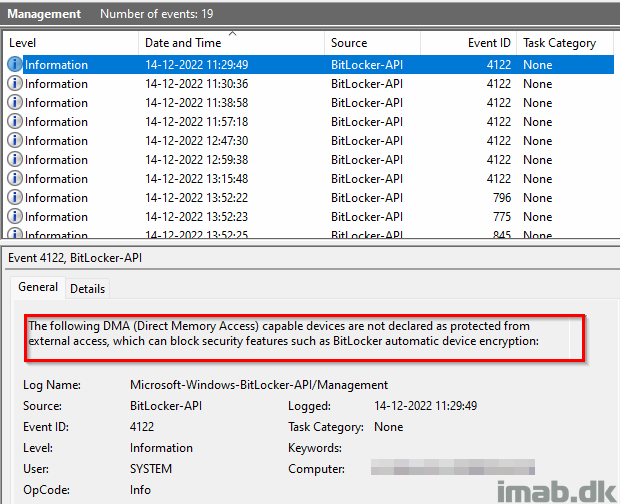
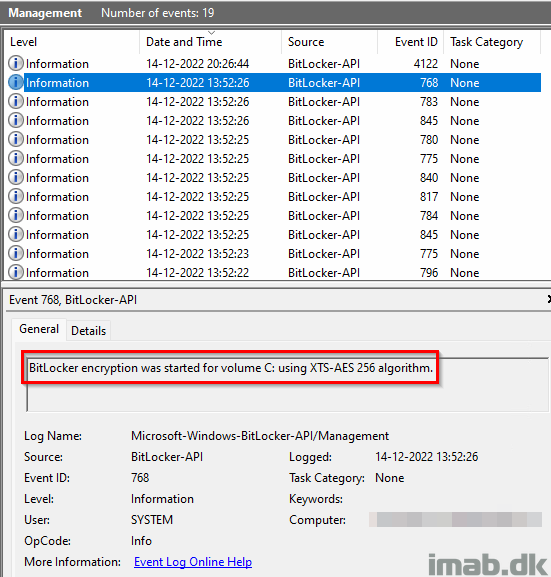
The device that wasn’t automatically having BitLocker enabled, had following informational entries in the BitLocker event log:
“The following DMA (Direct Memory Access) capable devices are not declared as protected from external access, which can block security features such as BitLocker automatic device encryption”
At one time, on the same device, I was also seeing:
“BitLocker cannot use Secure Boot for integrity because the UEFI variable ‘SecureBoot’ could not be read
Error Message: A required privilege is not held by the client”
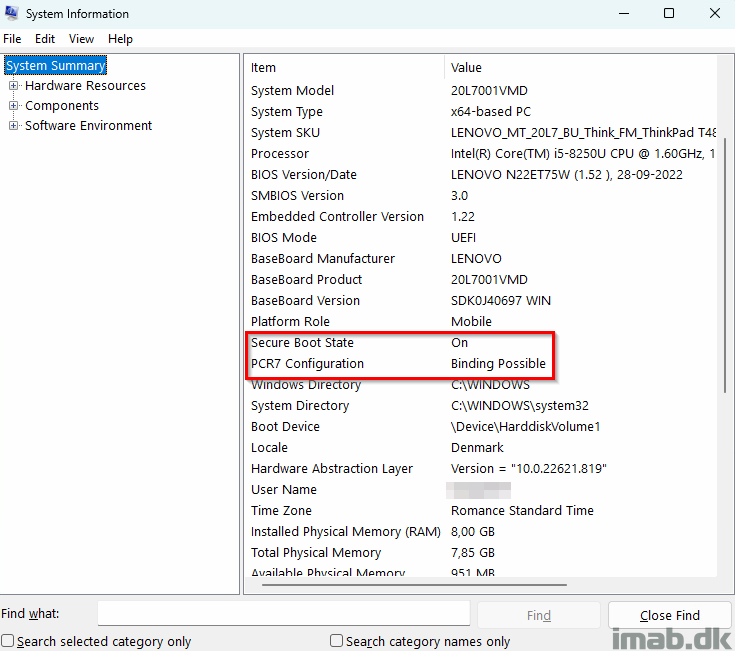
Troubleshooting sent me in various directions, but most articles on the subject suggested to verify if Secure Boot is enabled. It is indeed:
Endpoint Protection Policy
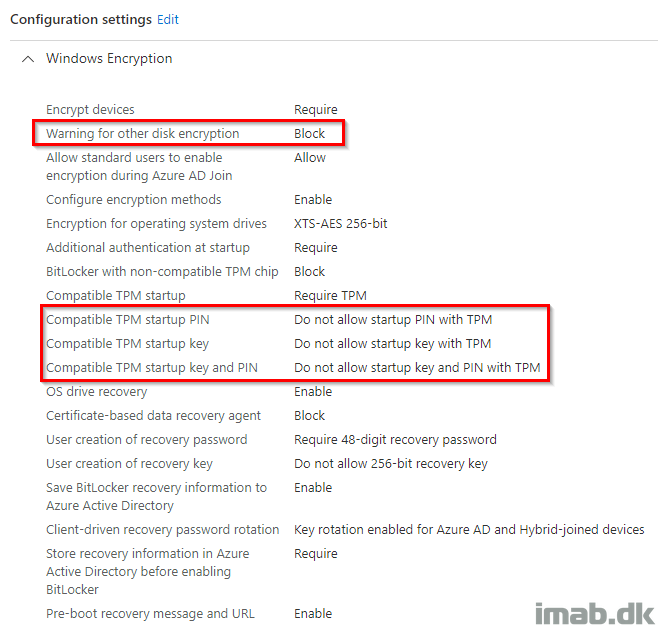
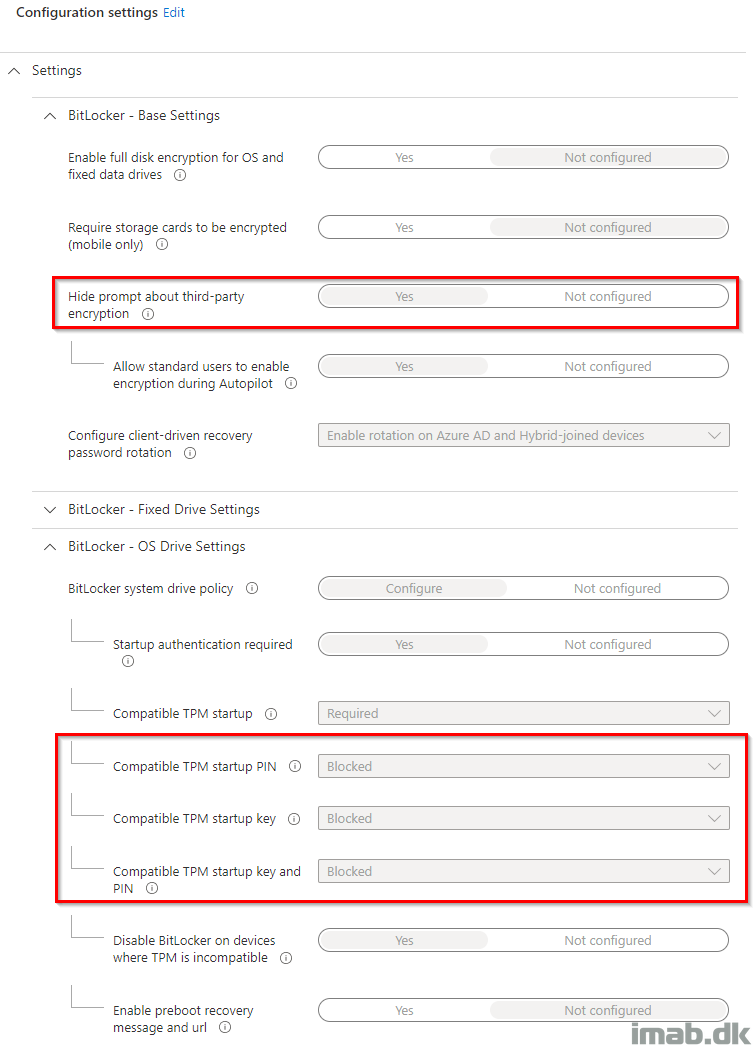
For the sake of it, I tried to (re)create my BitLocker policy using the ‘old’ Endpoint protection policies, and that worked immediately.
- The most important settings here, in order to have BitLocker work silently, are the ones highlighted below.
Endpoint Security Policy
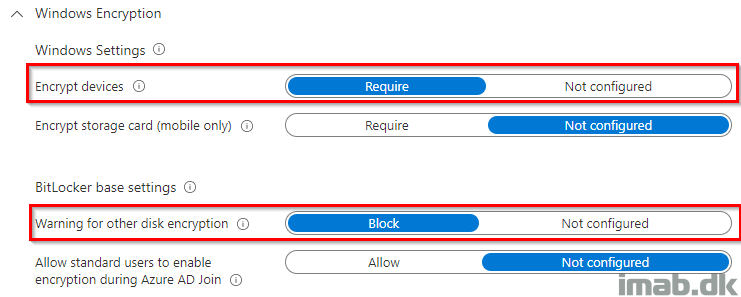
The same settings are reflected in my ‘new’ Endpoint security policy:
Modern Standby
Turns out that if a device is HSTI-compliant (most new devices are), but doesn’t support Modern Standby, you will have to combine Endpoint protection and Endpoint security policies (or for simplicity, just use Endpoint protection policies).
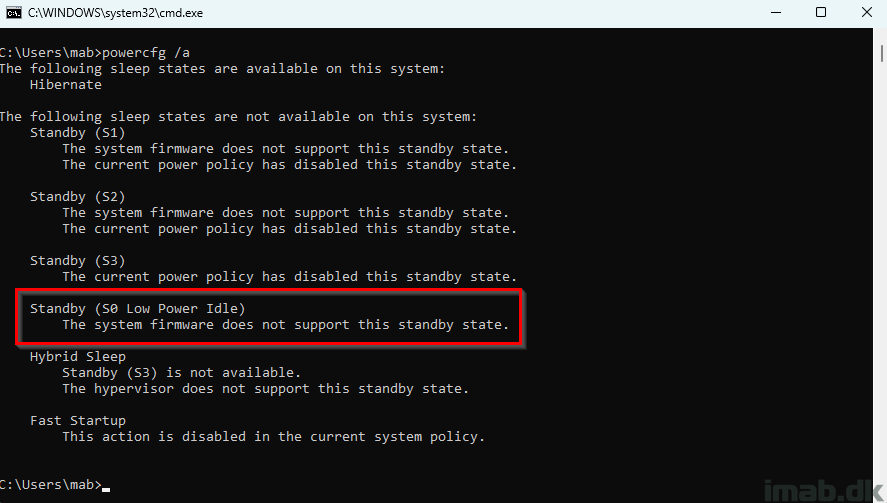
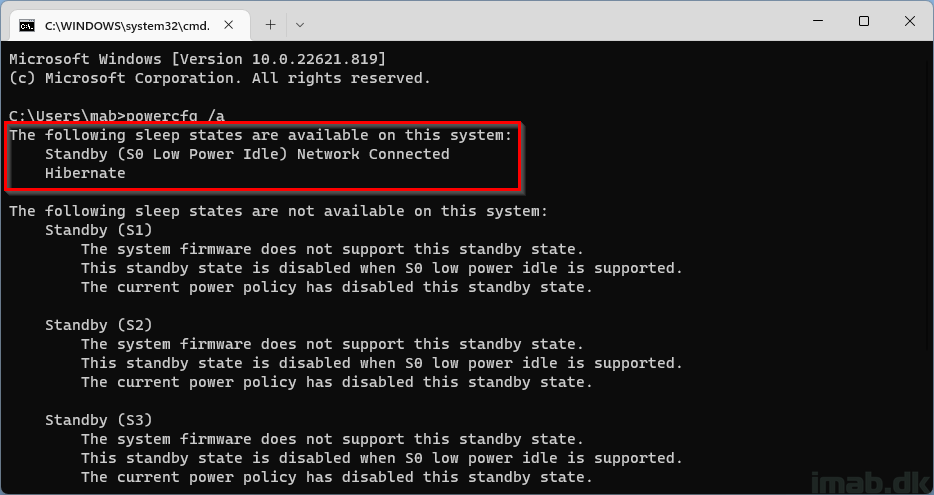
You can test if a device supports Modern Standby, by running powercfg /a on the device in question.
If Modern Standby is not supported, you will find Standby (S0 Low Power Idle) as not available:
If Modern Standby in return is supported, you will find Standby (S0 Low Power Idle) Network Connected as available:
Finally
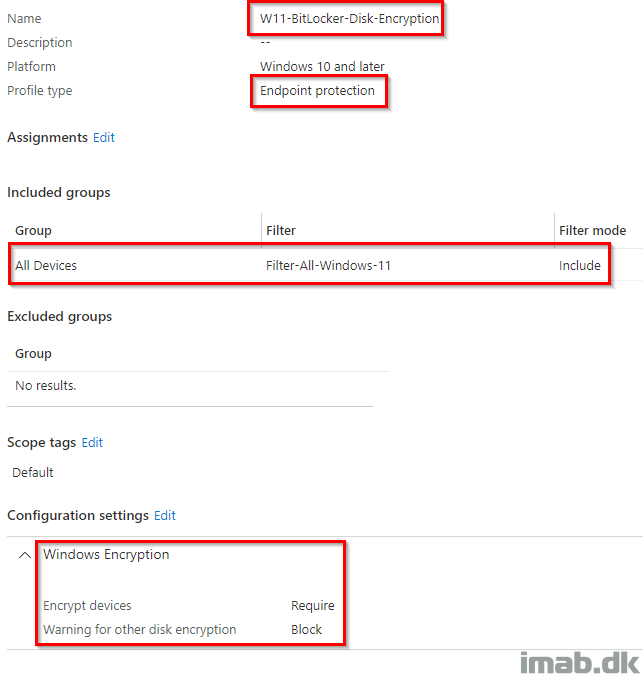
I created a new Endpoint protection policy containing just the below settings and combined them with my Endpoint security policy:
- Encrypt devices: Require
- Warning for other disk encryption: Block
And immediately thereafter my device began the silent and automatic BitLocker encryption:
ENJOY

Perfect – this issue just appeared at my org, and I randomly checked out your blog. Perfect timing.
Any new 2023 blog posts upcoming?