Introduction
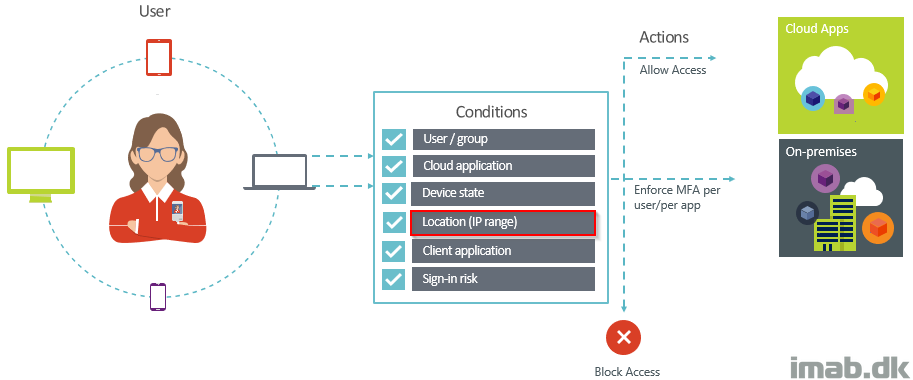
I have previously given a few examples on use cases for Conditional Access, and I admit, for the Conditional Access newbie, the options available can seem daunting. So how about a very simple scenario, where access to company resources are blocked, if not coming from a trusted IP?
Imagine service accounts running some Powershell scripts for automation in your Azure/O365 tenant or other accounts who are never meant to be used outside of your organization. Simply block those from authenticating in Azure/O365 if not coming from your headquarter public IP. This is how you can do just that, using Conditional Access.
Configuration
- First things first. Log into the Azure portal at portal.azure.com and locate or search for the Microsoft Intune blade and Conditional Access.
- Once located, create a new Conditional Access policy on + New Policy
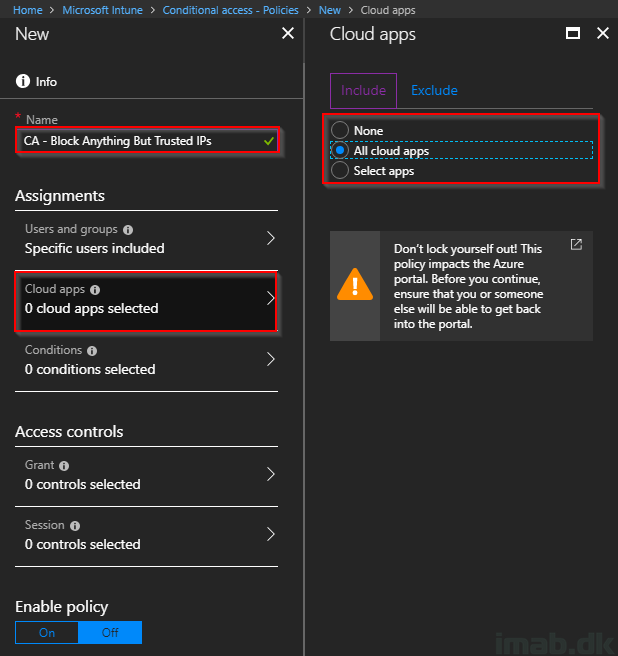
- Name: Give it a suitable name. For your inspiration, mine is called: CA – Block Anything But Trusted IPs
- Users and groups: Assign the policy to the desired user(s)
- Cloud apps: Select All cloud apps
- Test, test and test this again. Don’t lock yourself out. In this scenario, it’s not too dangerous as we only target a few users
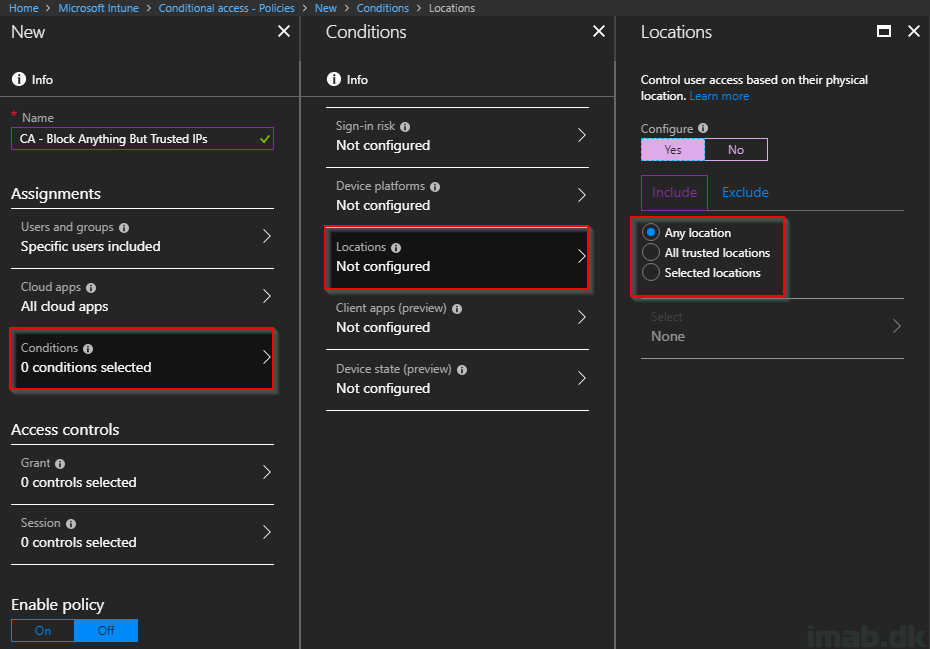
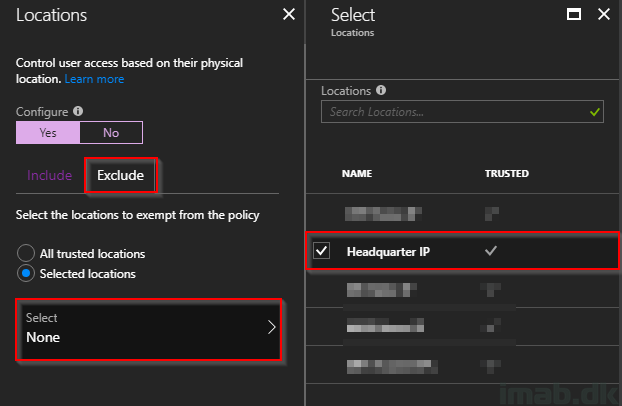
- Conditions: Select Locations and Yes to Configure. Include Any location and move on to the Exclude section
- Select to Exclude your Headquarter IP
- The trusted location is created in Azure Active Directory -> Conditional Access -> Named location
- The combination in this rule essentially means that all locations will be blocked for the specific user(s) EXCEPT the trusted location
- Access controls: Select to Block the access
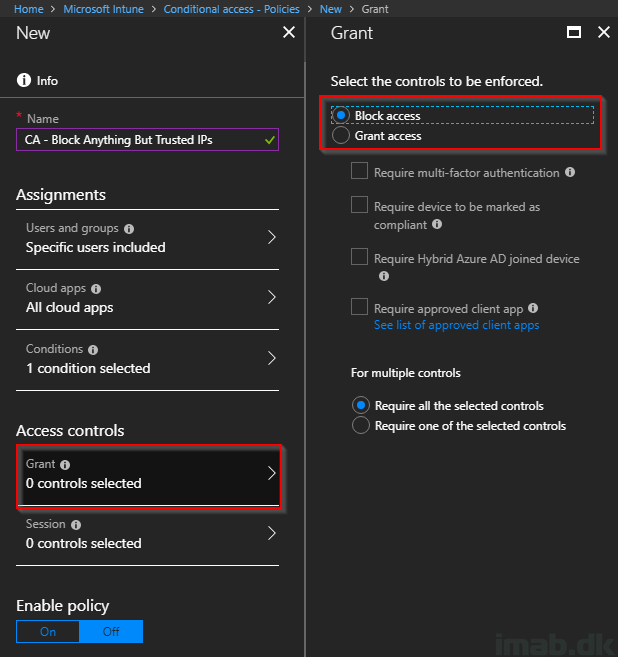
Finally, remember to Enable the policy for effect.
End-user experience
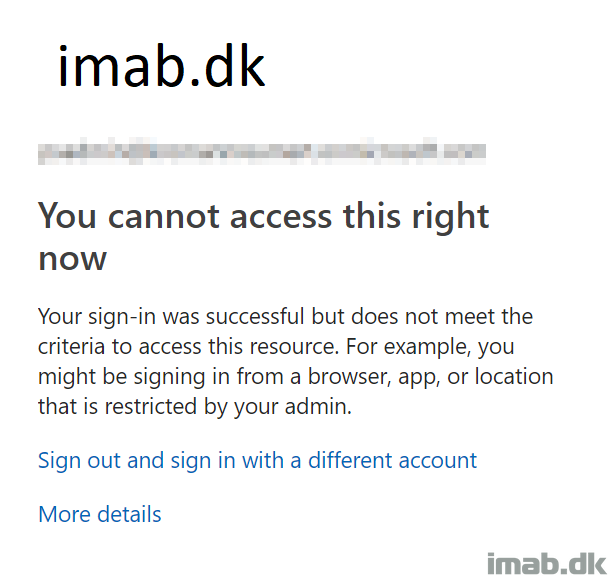
From an end-users perspective, trying to log in with one of the targeted users from outside the trusted IP range, will yield the following prompt and access will be blocked.
Please let me know if you have any questions, and I’ll be happy to assist in the comment section below.
Enjoy 🙂