Introduction
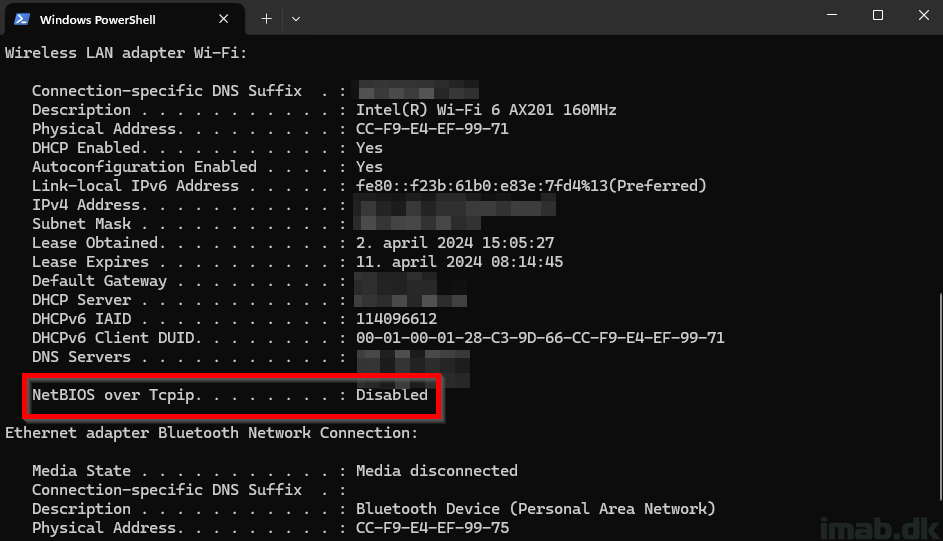
If you are working with device management and IT security in general, you have probably heard about the recommendation to disable the legacy protocol NetBIOS in Windows.
If this is news to you, there’s some interesting reading for you in this article: Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay, Sub-technique T1557.001 – Enterprise | MITRE ATT&CK
NOTE: Before disabling anything, make sure you do your due diligence and monitor your environment for NetBIOS traffic, so you don’t accidently break stuff! Wireshark can help you with this.
PowerShell
My solution consists of 2 PowerShell scrips, both to be used with Microsoft Intune. The scripts are located on my GitHub repository.
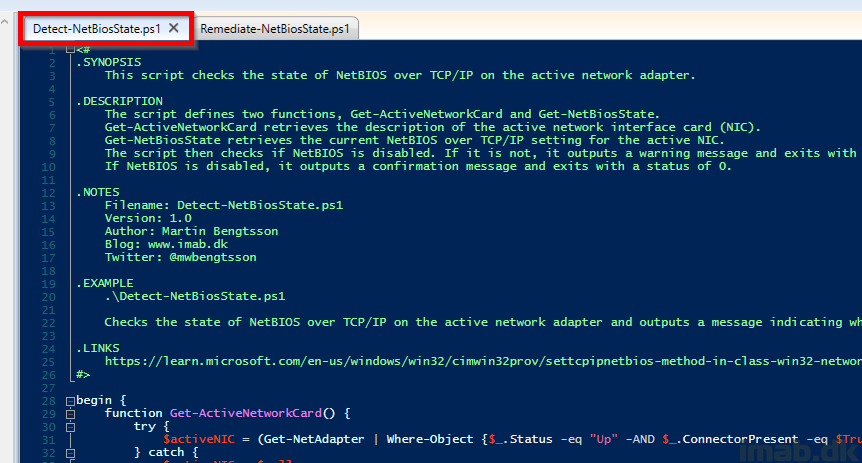
Detect-NetBiosState.ps1: Proactive-Remediations/Detect-NetBiosState.ps1 at main · imabdk/Proactive-Remediations (github.com)
- This script detects whether NetBIOS is currently disabled or not on the active network adapter
- If NetBIOS is NOT disabled, the script will exit with error 1 instructing Microsoft Intune to run the remediation script
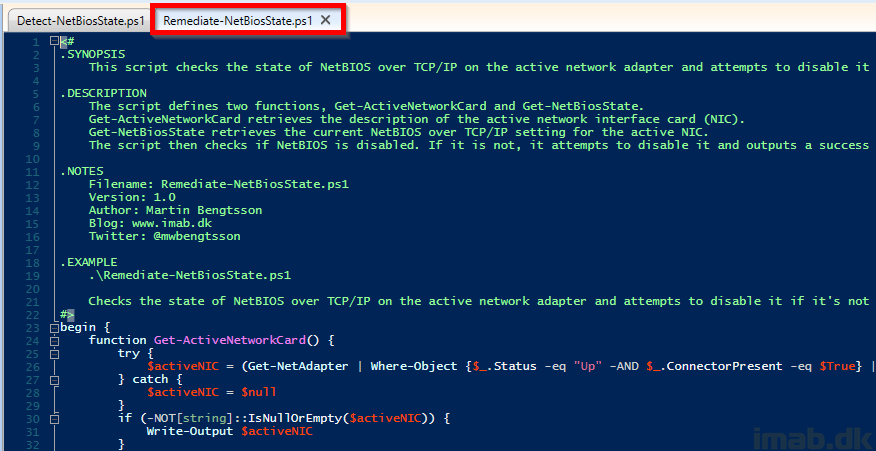
Remediate-NetBiosState.ps1: Proactive-Remediations/Remediate-NetBiosState.ps1 at main · imabdk/Proactive-Remediations (github.com)
- This script detects whether NetBIOS is currently disabled or not on the active network adapter
- If NetBIOS is NOT disabled, the script will attempt to disable it
Microsoft Intune
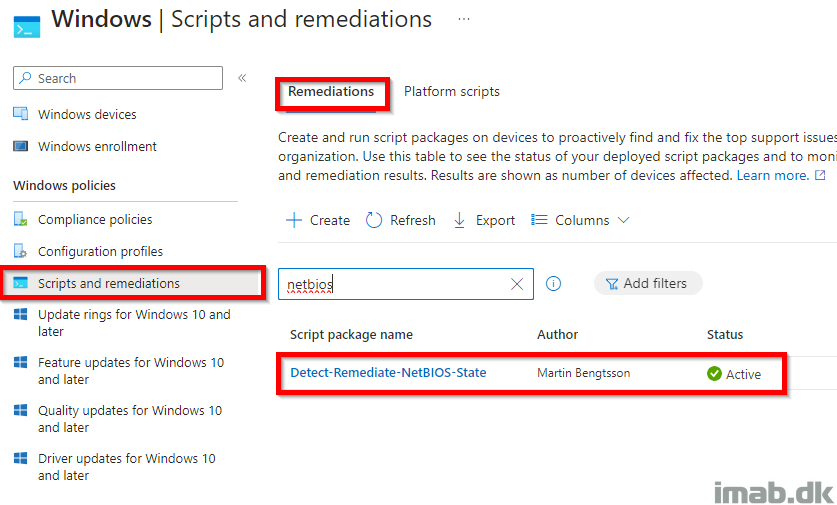
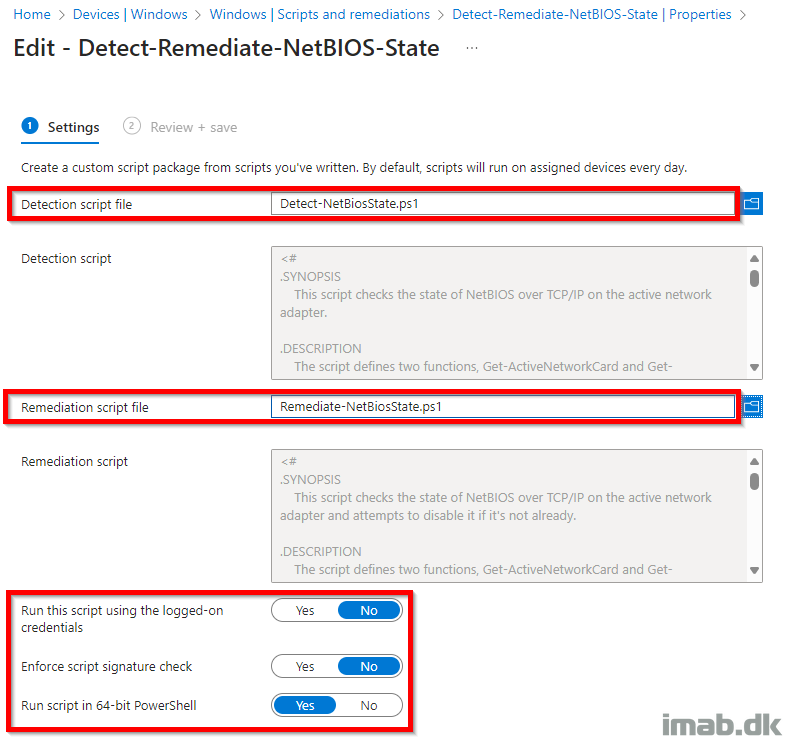
Put the 2 scripts to use in Microsoft Intune with the Remediations options (formerly known as Proactive Remediations) as shown below:
Logging
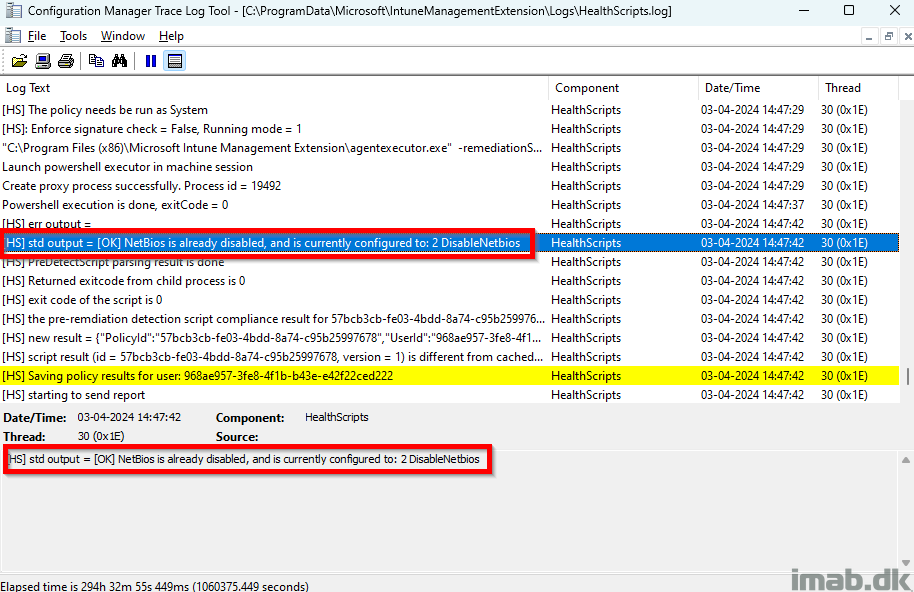
The scripts are logging their actions into C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\HealthScripts.log
ENJOY