Windows 10 Credential Guard is currently another hot topic considering cyber security. Credential Guard is a new feature in Windows 10 (Enterprise and Education edition) that helps to protect your credentials on a machine from threats such as pass the hash.
To be able to enable Credential Guard in Windows, you need to have virtualization enabled on the CPU in the BIOS. Virtualization is rarely enabled by default, and as such you will need to enable it manually (F1, enter BIOS, modify the setting) or better yet, find a solution to do so remotely and automatically.
I have created following script in Powershell, that initially enables virtualization in the BIOS (Note: We only use Lenovo laptops, hence this is made for Lenovo laptops only) and then apply the registry-keys to enable Credential Guard. All steps are logged into c:\Windows\EnableCredentialGuard.log
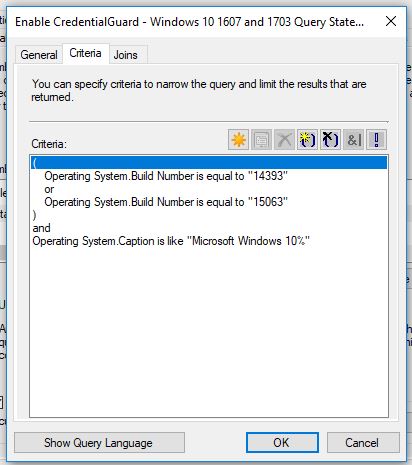
The script can be targeted to the proper Windows 10 versions through SCCM collections (I this example I only target W10 1607 and 1703, as these Windows 10 versions no longer require the Isolated User Mode feature when enabling Credential Guard, as it’s now embedded into the Hypervisor)
When deploying powershell script from SCCM, remember to create the program with a command line like this: powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\CredentialGuard\Enable-VirtualizationCredentialGuard.ps1
<#
.SYNOPSIS
Enable virtualization in Lenovo Bios and enable Credential Guard in Windows 10
.DESCRIPTION
This script will only run on Lenovo computers. If run on Lenovo computer, the script will check if virtualization is enabled in BIOS.
If not, virtualization will be enabled in the process of enabling CredentialGuard.
Also appends actions to logfile: EnableCredentialGuard.log
.NOTES
FileName: Enable-VirtualizationCredentialGuard.ps1
Author: Martin Bengtsson
Created: 19-07-2017
#>
$Logfile = "C:\Windows\EnableCredentialGuard.log"
#Create LogWrite function
Function LogWrite
{
Param ([string]$Logstring)
Add-Content $Logfile -Value $Logstring
}
#Get computermanufacturer
$Lenovo = Get-WmiObject Win32_ComputerSystemProduct | Select-Object Vendor
#If not a Lenovo laptop, write to log and exit script
If ($Lenovo.Vendor -ne "Lenovo"){
LogWrite "Not a Lenovo laptop - exiting script"
Write-Warning -Message "Not a Lenovo laptop - exiting script" ; exit 1
}
Else {
Write-Host -ForegroundColor Yellow "Collecting Lenovo_BiosSetting information" ; LogWrite "Collecting Lenovo_BiosSetting information"
$VirtEnabled = Get-WmiObject -Class Lenovo_BiosSetting -Namespace root\WMI | Where-Object {$_.CurrentSetting -match "Virtualization*"} | Select-Object CurrentSetting
If ($VirtEnabled.CurrentSetting -eq "VirtualizationTechnology,Disable"){
Write-Host -ForegroundColor Cyan "Virtualization disabled - trying to enable virtualization" ; LogWrite "Virtualization disabled - trying to enable virtualization"
Try {
(Get-WmiObject -Class Lenovo_SetBiosSetting -Namespace root\wmi).SetBiosSetting("VirtualizationTechnology,Enable")
(Get-WmiObject -Class Lenovo_SaveBiosSettings -Namespace root\wmi).SaveBiosSettings()
}
Catch {
Write-Host -ForegroundColor Cyan "An error occured when enabling virtualization in the BIOS" ; LogWrite "An error occured when enabling virtualization in the BIOS" ; exit 1
}
cls
Write-Host -ForegroundColor Cyan "Virtualization Successfully enabled" ; LogWrite "Virtualization Successfully enabled"
}
#Add required registry key for Credential Guard
$RegistryKeyPath = "HKLM:\SYSTEM\CurrentControlSet\Control\DeviceGuard"
If (-not(Test-Path -Path $RegistryKeyPath)) {
Write-Host -ForegroundColor Yellow "Creating HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard registry key" ; LogWrite "Creating HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard registry key"
New-Item -Path $RegistryKeyPath -ItemType Directory -Force
}
#Add registry key: RequirePlatformSecurityFeatures - 1 for Secure Boot only, 3 for Secure Boot and DMA Protection
New-ItemProperty -Path $RegistryKeyPath -Name RequirePlatformSecurityFeatures -PropertyType DWORD -Value 1
Write-Host -ForegroundColor Yellow "Successfully added RequirePlatformSecurityFeatures regkey" ; LogWrite "Successfully added RequirePlatformSecurityFeatures regkey"
#Add registry key: EnableVirtualizationBasedSecurity - 1 for Enabled, 0 for Disabled
New-ItemProperty -Path $RegistryKeyPath -Name EnableVirtualizationBasedSecurity -PropertyType DWORD -Value 1
Write-Host -ForegroundColor Yellow "Successfully added EnableVirtualizationBasedSecurity regkey" ; LogWrite "Successfully added EnableVirtualizationBasedSecurity regkey"
#Add registry key: LsaCfgFlags - 1 enables Credential Guard with UEFI lock, 2 enables Credential Guard without lock, 0 for Disabled
New-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\Lsa -Name LsaCfgFlags -PropertyType DWORD -Value 2
Write-Host -ForegroundColor Yellow "Successfully added LsaCfgFlags regkey" ; LogWrite "Successfully added LsaCfgFlags regkey"
Write-Host -ForegroundColor Yellow "Successfully enabled Credential Guard - please reboot the computer" ; LogWrite "Successfully enabled Credential Guard - please reboot the computer"
}
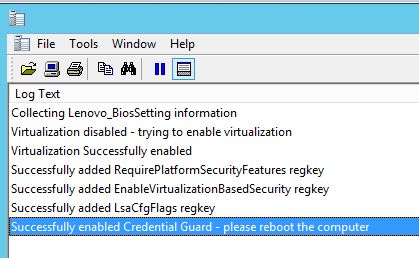
Snip of the logfile when everything succeeds:
Dude, this is awesome. Thanks for sharing
Thank you! Much appreciated 🙂
i want to ask a question , is it needed to access your power shell as administrator
and also how can i be sure if the critirea you talked about is right or not?
Hey, yes, administrative rights is required. I’m not sure what criteria you are referring to? 🙂
Fantastic, you save my time.
So great! Enabled virtualization on a client’s Lenovo remotely. I’m a fan.
Thank you for the snippet on enabling virtualization in the BIOS remotely! Does that piece look differently if there is a password set on the BIOS? TIA
It would look different yes, as the password for the BIOS needs to be passed on with the command to enable virtualization 🙂