Introduction
More relevant than ever. Denmark is well into their second COVID-lockdown, and working from home and remote is yet again mandatory for many.
Speaking of remote work, moving workloads off of your on-premises Active Directory, and therefore being less dependent on your VPN, should be something to prioritize.
- Obviously assuming on-premises AD as well as VPN requirement in this scenario, as this is still the reality for many
Managing your Windows Defender Firewall settings from the cloud is not only convenient, but I’d argue also something that will increase your security posture. I’ll try to elaborate along the lines.
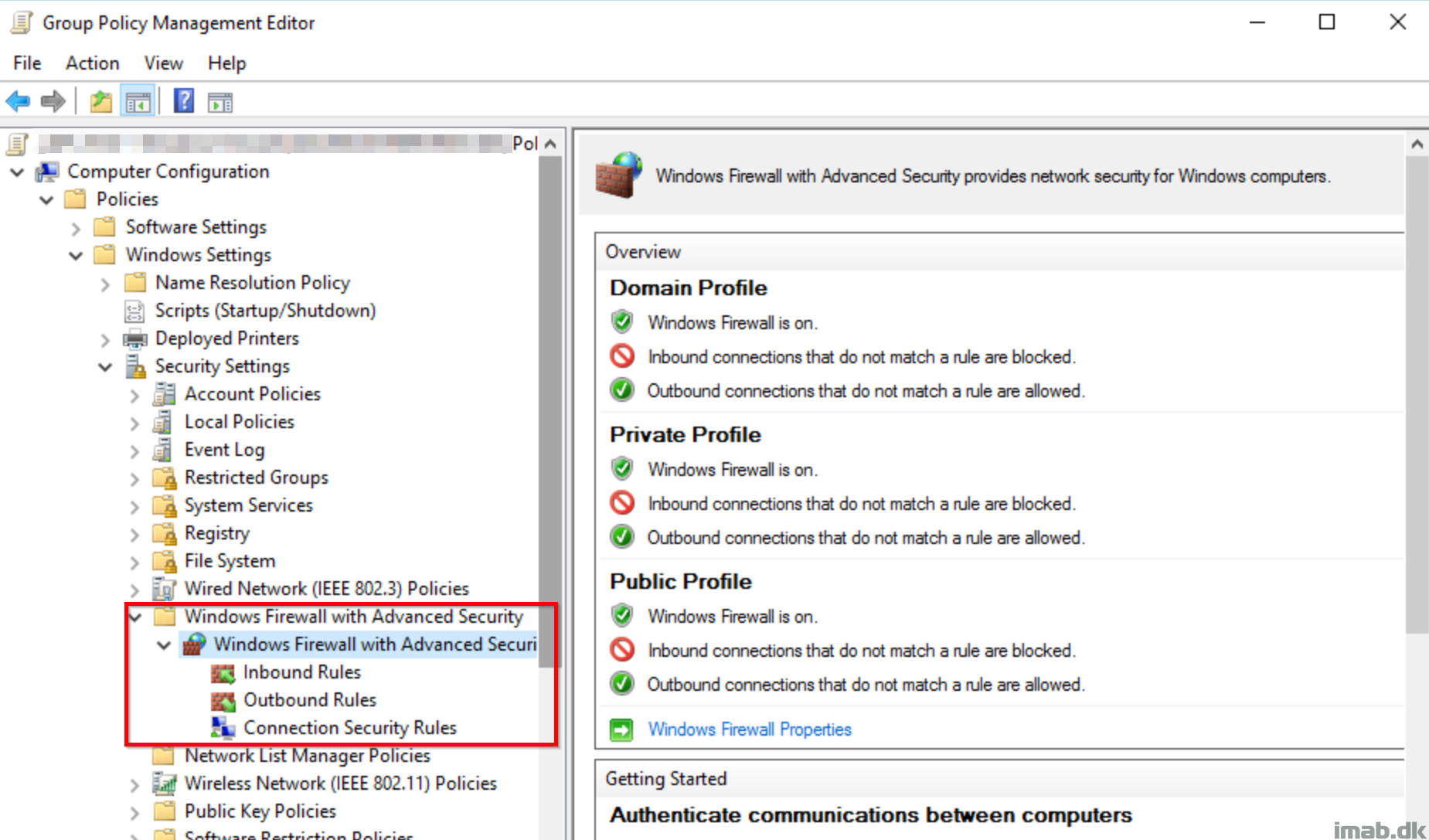
Group Policy
Managing Windows Firewall via GPO, is something we have done in almost decades. Moving the management to the cloud might seem intimidating, but have no fear.
- This might also serve as a good opportunity to clean up old rules and tighten your security where possible
Review your current settings
Start off by familiarizing yourself with all the current settings of your Windows Firewall. I’d prioritize this to a degree, where you’re pretty confident in what’s being managed and what’s not. This will prove useful once everything is migrated/created over in Intune.
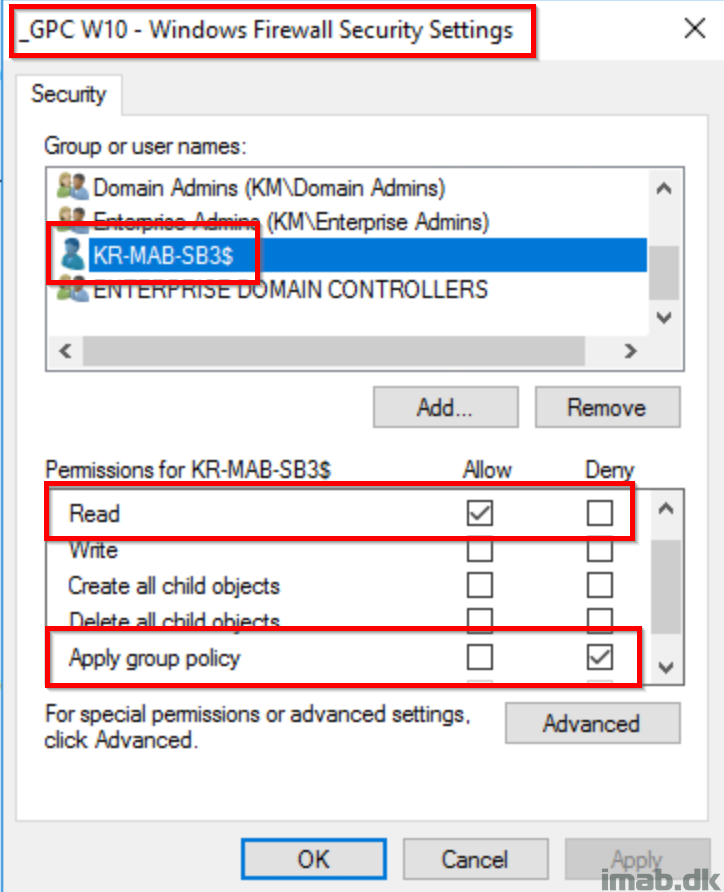
Exclude from GPO
I recommend that the devices, moving the management of Windows Firewall to Intune, are being excluded from the GPO(s) in question. You know what suits your environment best here, but having two separate authorities delivering settings to the same area, is never a good idea.
Initially when testing this, I did following to exclude my own device from my Windows Firewall GPO.
- Do what serves your environment the most. Whether that be a direct exclusions on the GP object, re-arrangement of OU’s or WMI filters
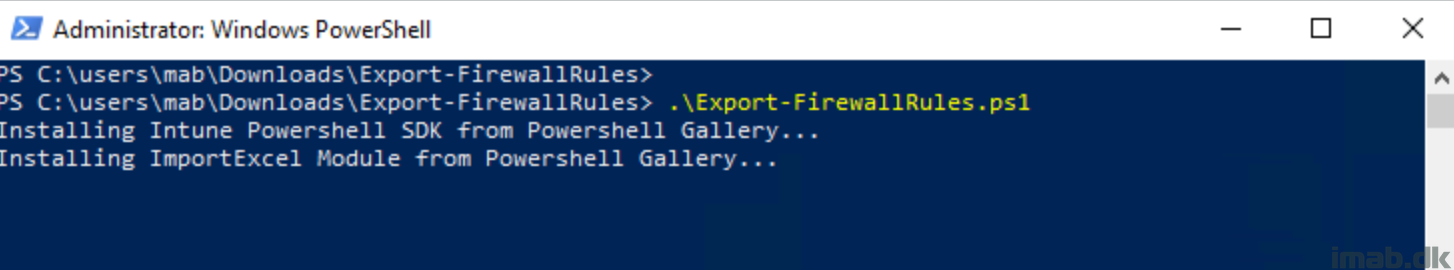
Migrate Firewall Rules
You can migrate your current firewall rules, by using the migration tool: Endpoint security firewall rule migration tool for Microsoft Intune | Microsoft Docs
This is a safe and easy way of getting your current rules over into Intune. The process is like this:
- Download the script from the URL above
- Run the script
- The script downloads and installs the required modules
- The script prompts for credentials
- The scripts needs either Endpoint Security Manager, Intune Service Admin or Global Admin permissions
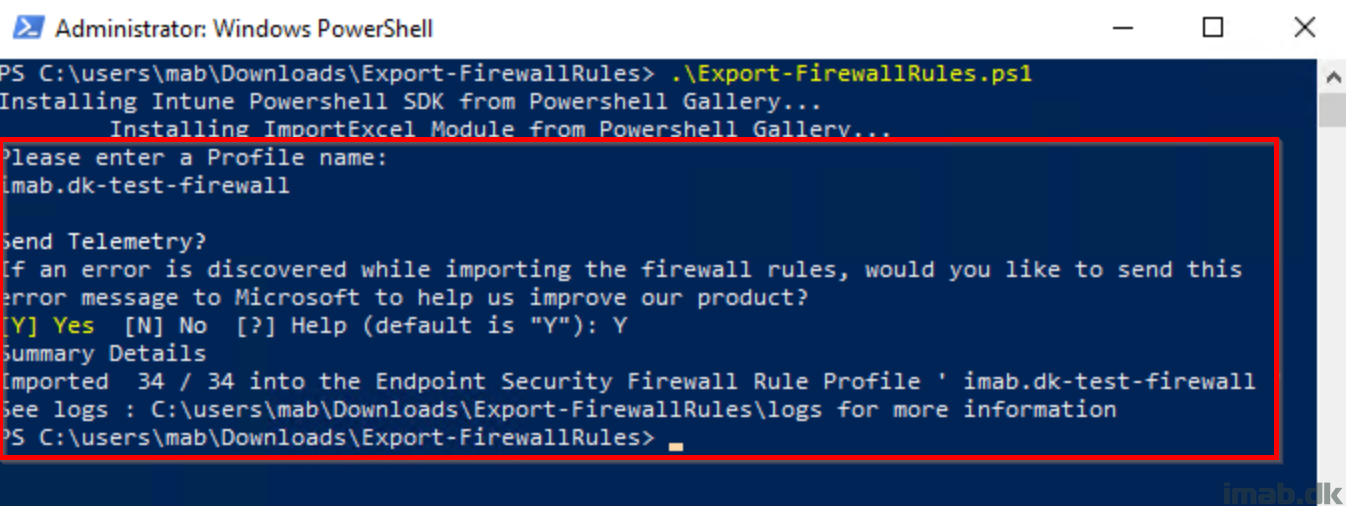
- Prompts for profile name to be created in Endpoint security in Intune
Below is a few snippets of the process:
- Running the script and installing required modules
- Prompt for credentials with required permissions
(Apologies for the Danish nonsense)
- Prompt for profile name and import of firewall rules into Intune
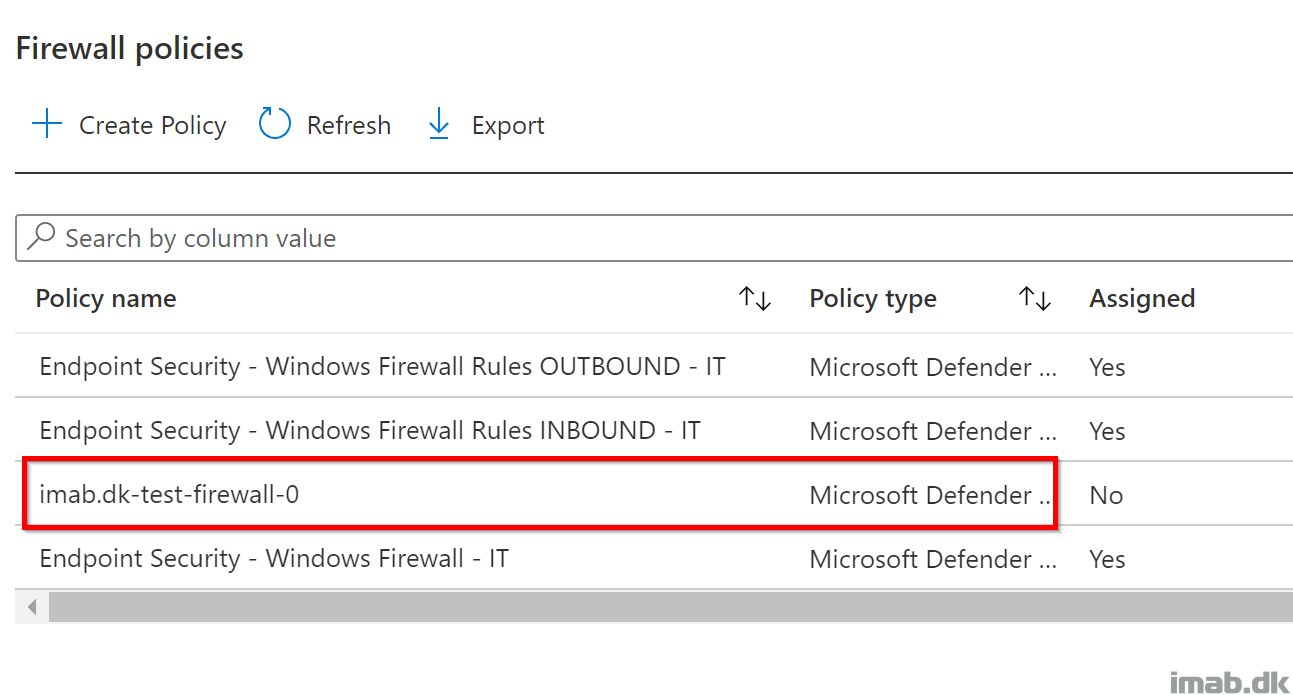
- Final Endpoint security profile in Intune
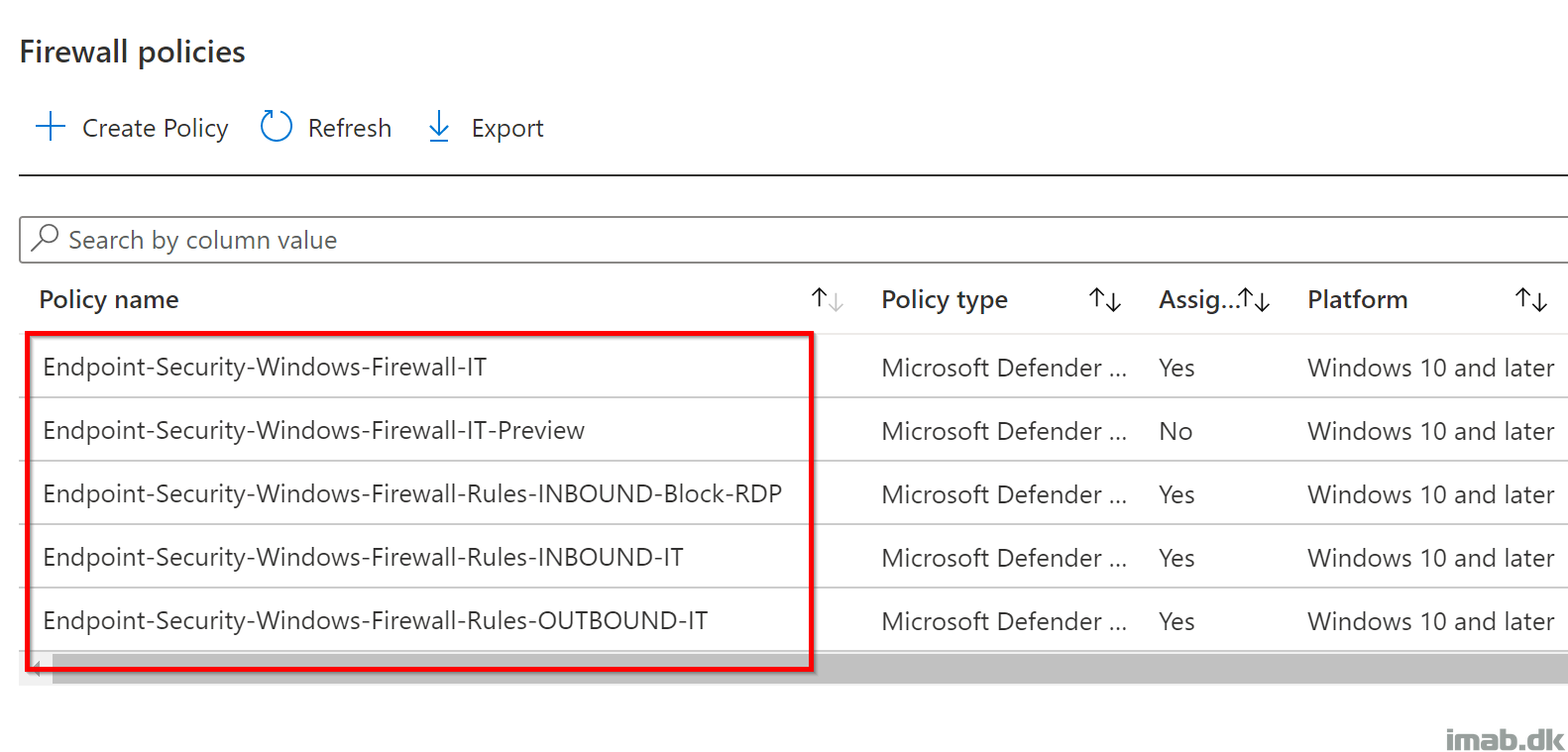
Endpoint Manager
Per usual, the further configuring of Windows Firewall takes place in the Microsoft Endpoint Manager admin center: https://endpoint.microsoft.com
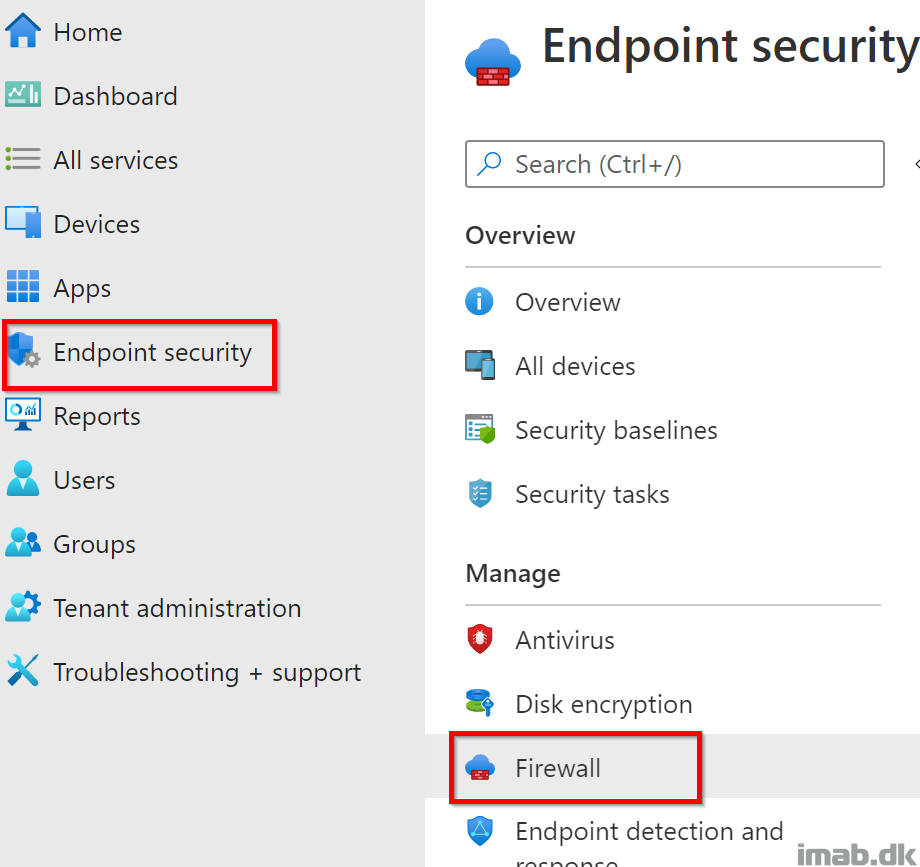
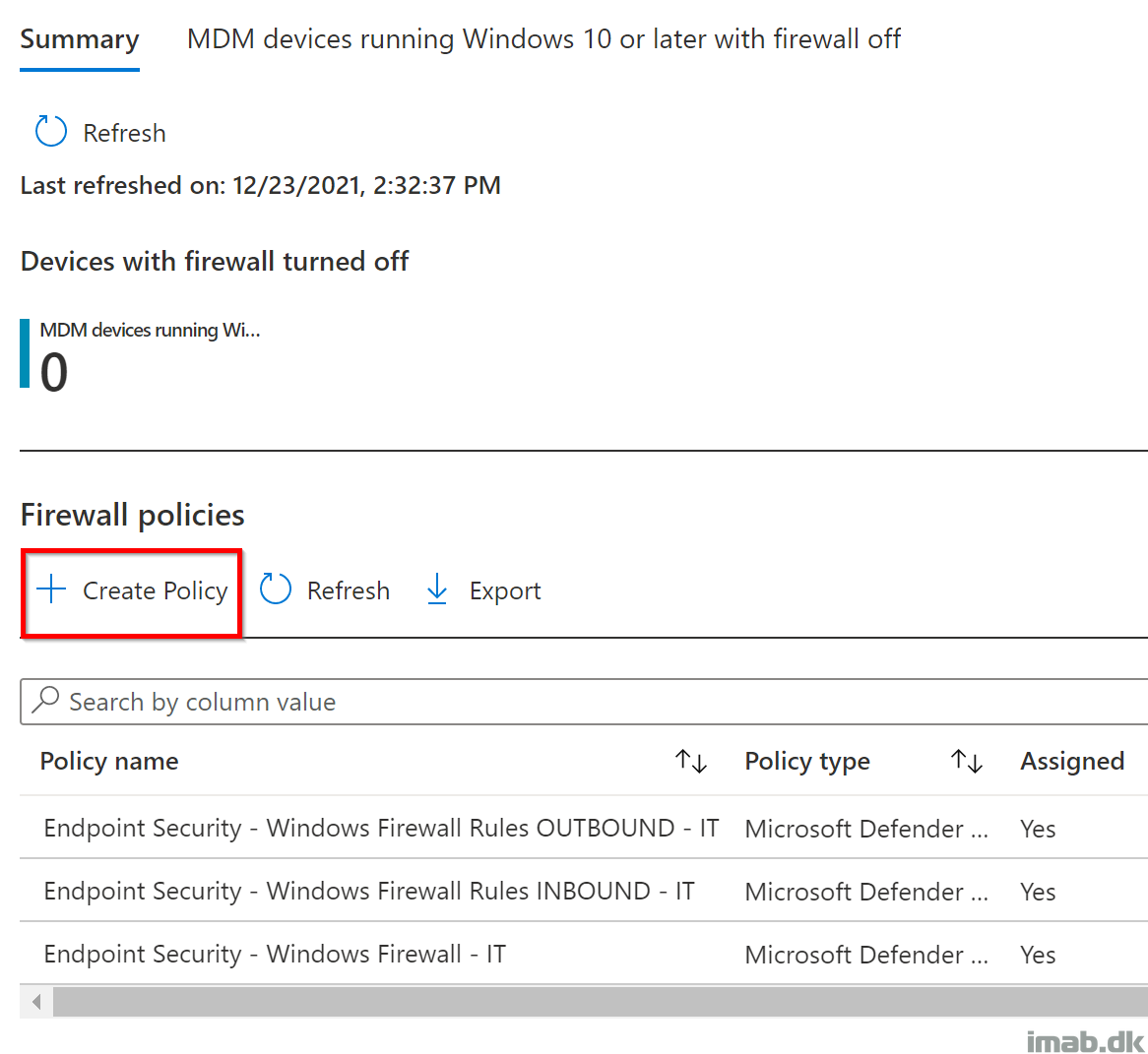
- Head into Endpoint security -> Firewall as illustrated below:
- Click on Create Policy:
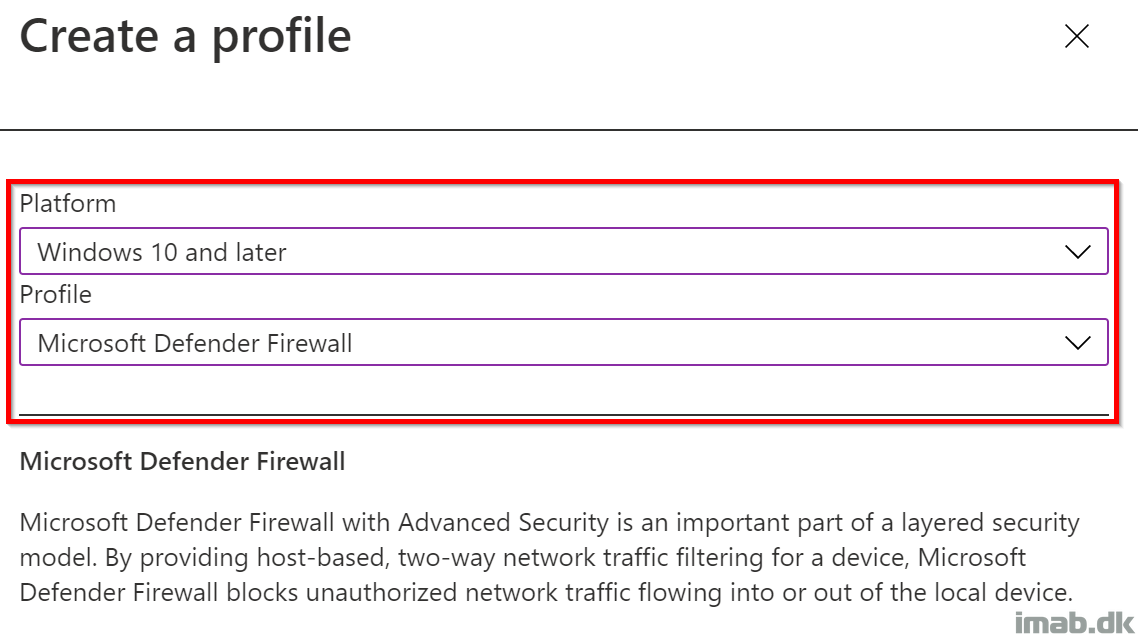
- Select following in the dropdown menus:
- Platform: Windows 10 and later
- Profile: Microsoft Defender Firewall
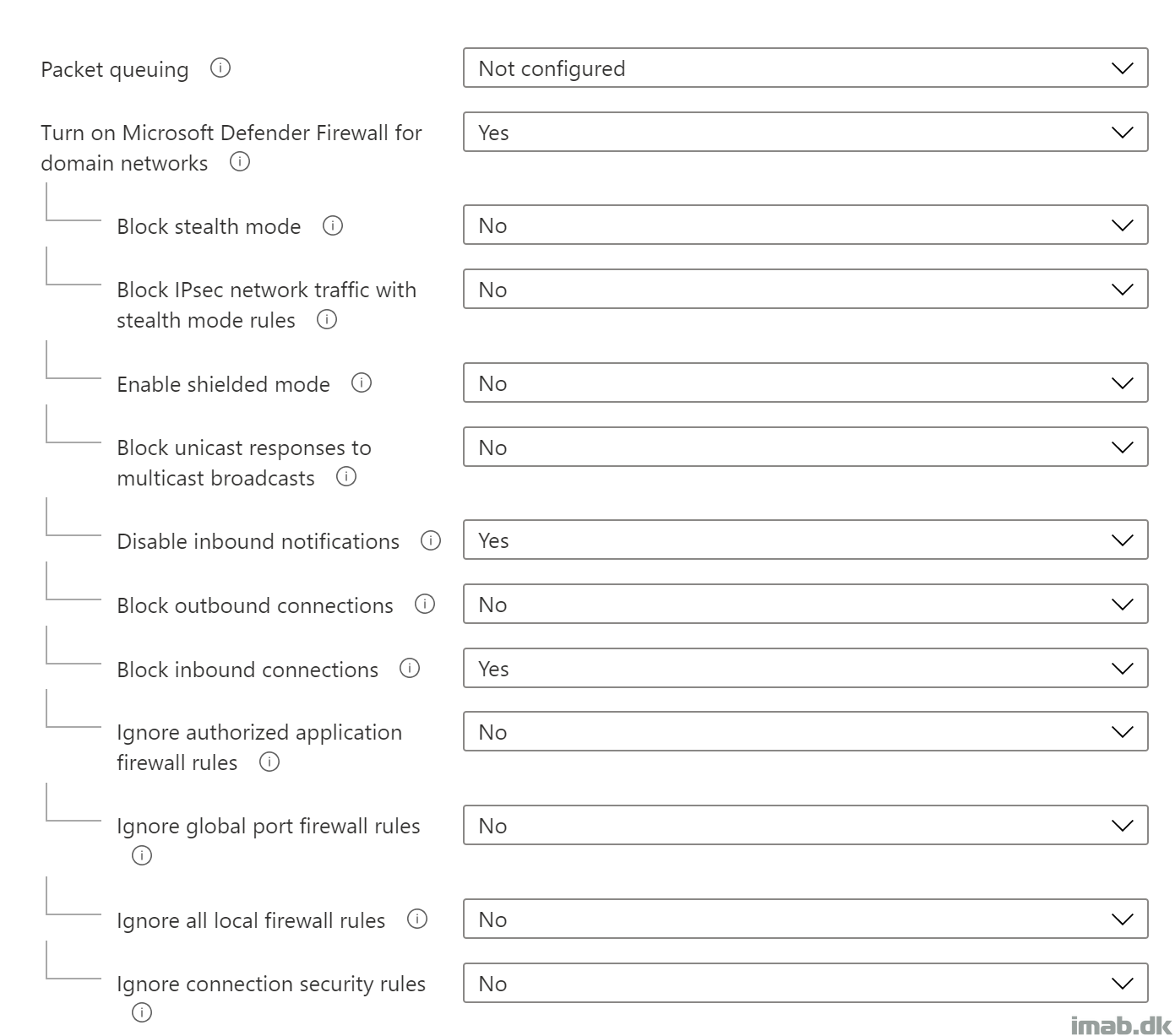
- Configuration of the actual settings for the Windows Firewall, is not something I want to dictate for you. This is highly individual
- I’m more or less sticking to the default and recommended values
- If looking for docs on the recommended settings, look no further: Best practices for configuring Windows Defender Firewall – Windows security | Microsoft Docs
What Else?
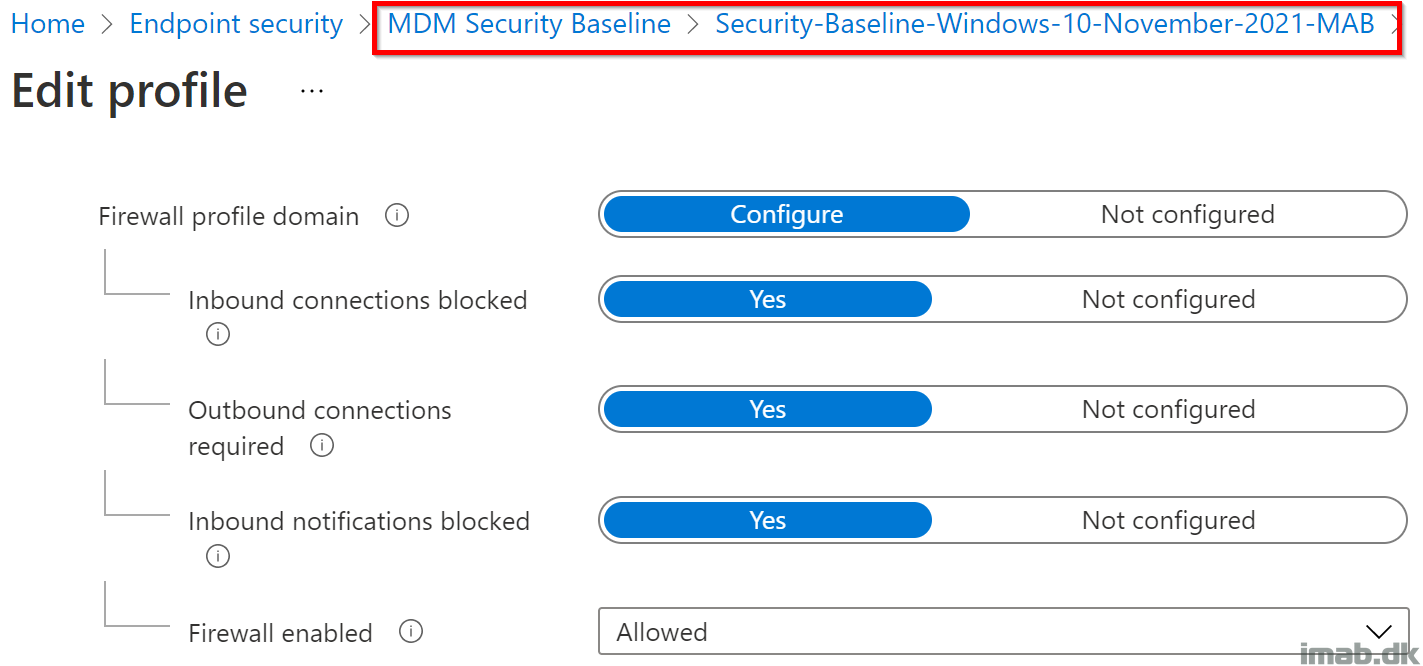
Security Baseline
Make sure that your settings are aligned with the ones in the Security Baselines (if such is assigned to your devices as well).
If your settings are not aligned, conflicts will occur.
- NOTE: When a conflict exists between two policies, that manage the same setting with different values, the setting is NOT sent to the device
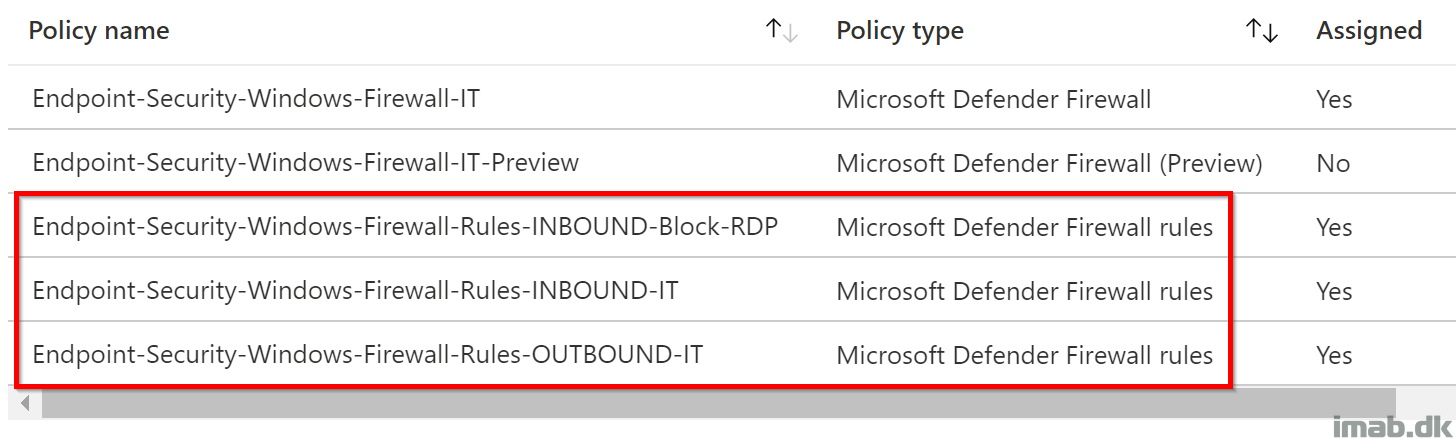
Multiple Rules Profiles
I deliberately chose to go with multiple Rules Profiles.
I did this, because I had a sense of feeling lost in the UI, when browsing each and every rule within the same profile. I also wanted to be able to micro-manage the assignments. Every device doesn’t necessarily need the same set of rules as the others.
- NOTE: Conflicts within Rules Profiles acts differently than other profiles in Intune!
- Conflicts between two Rules Profiles managing the same setting, are both sent to the device. This will much likely cause unexpected behavior on the device
- Remember that Blocked rules takes precedence over Allowed rules
Security posture what?
Considering remote work, and being dependent on an active VPN connection in order to receive group policy updates, is not the most fortunate combination in regards to managing security features on your devices.
Consider following factors, just to name a few:
- VPN connections tends to disconnect once in a while
- If shit hits the fan, and you need to do a critical change to your firewall configuration (or any security related configuration) across the board, you will appreciate not being dependent on the VPN
- When that critical change has been made, you will also appreciate some very easy reporting
ENJOY 🙂
Thank for this cool post!!
Is there a way to configure “block any” rule for outbound but not harm the connection to intune abd Azure AD?
I experienced to set any value to either ‚yes‘ or ‚no‘ in the firewall profile and never use ‚not configured‘ believing in mentioned default behavior described in the info bubble.
It disabled e.g. RDP inbound even I had rules for it.