Introduction
While brewing on a much more detailed post on how I moved my devices from Intune Hybrid with ConfigMgr to Intune standalone, I thought I’d share how you can offer webmail for your users, while requiring MFA (Multifactor Authentication) if not coming from a company device, using Conditional Access.
In this post I will only cover the actual steps in Intune, but for this to work, you will have to have your Windows devices registered with Azure AD. There will be some requirement for your on-prem AD and for your ADFS, if that’s how you federate with Azure/O365. These requirements are explained in details in this Microsoft article: https://docs.microsoft.com/da-dk/azure/active-directory/device-management-hybrid-azuread-joined-devices-setup
Configuration
- Intune is now fully accessible through the Azure portal on https://portal.azure.com/ – head over there and sign in
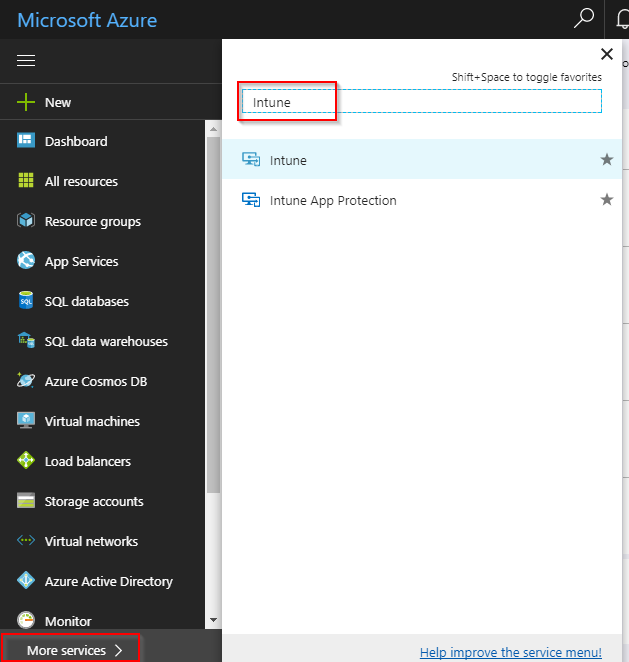
- When signed in, look for More services in the menu and search for Intune
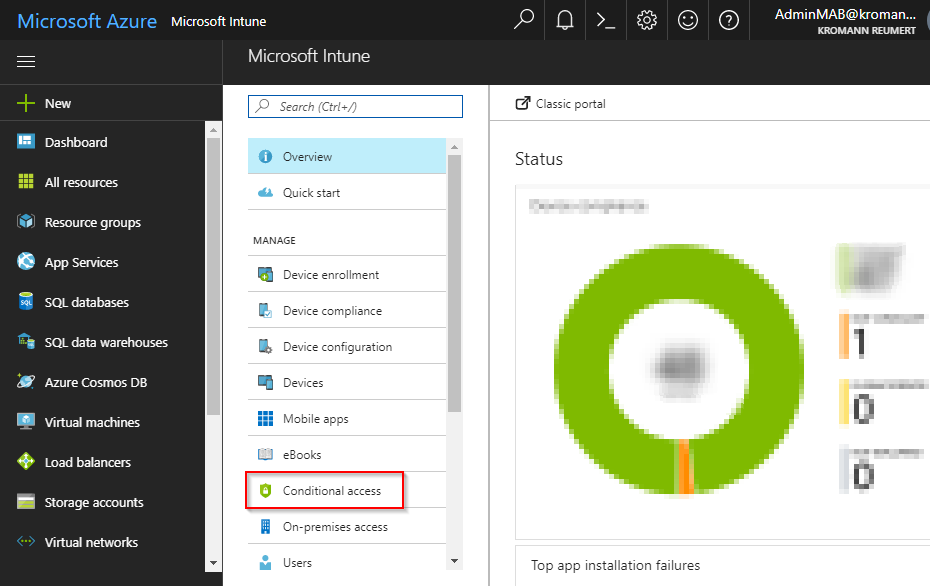
- In the Intune section of the Azure portal, click on the Conditional Access menu button
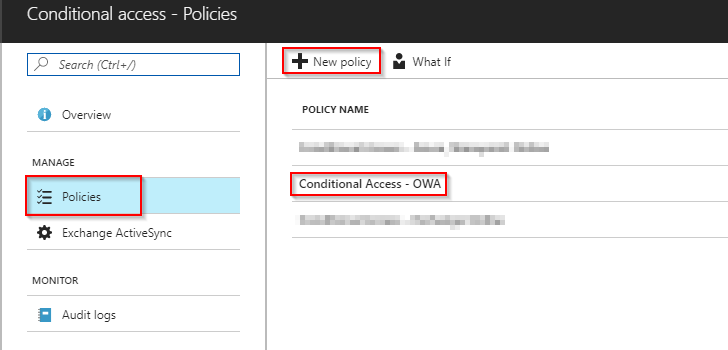
- Create a new Conditional Access policy on New policy and give it a name f.i. Conditional Access – OWA
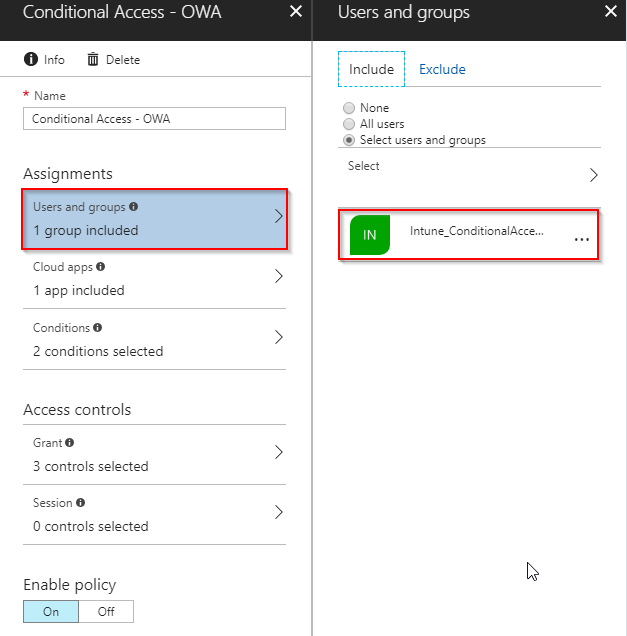
- Assign the new CA policy to a group consisting of users. For your inspiration, I’m syncing an on-premise security group consisting of users already assigned an EMS license, as Conditional Access in Intune requires an EMS license. This will probably vary depending on your needs, setup and design goals, but I recommend that there is some synergy between whom is assigned EMS licenses, and whom you are targeting with policies in Intune (for the sake of doing proper IT 🙂
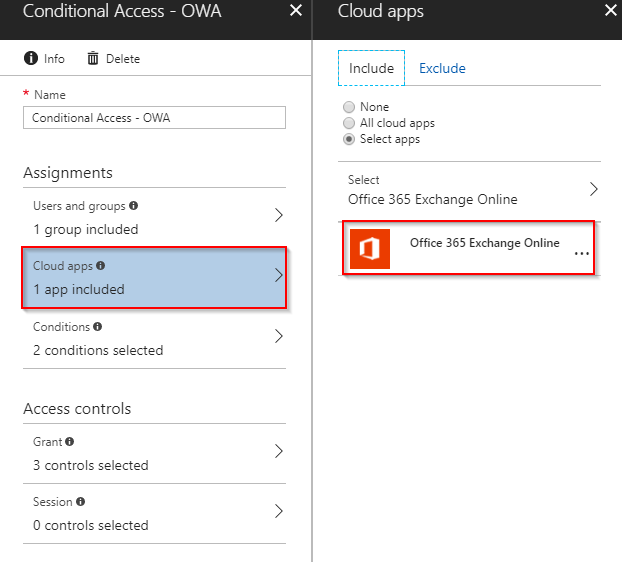
- Select Exchange Online in Cloud apps
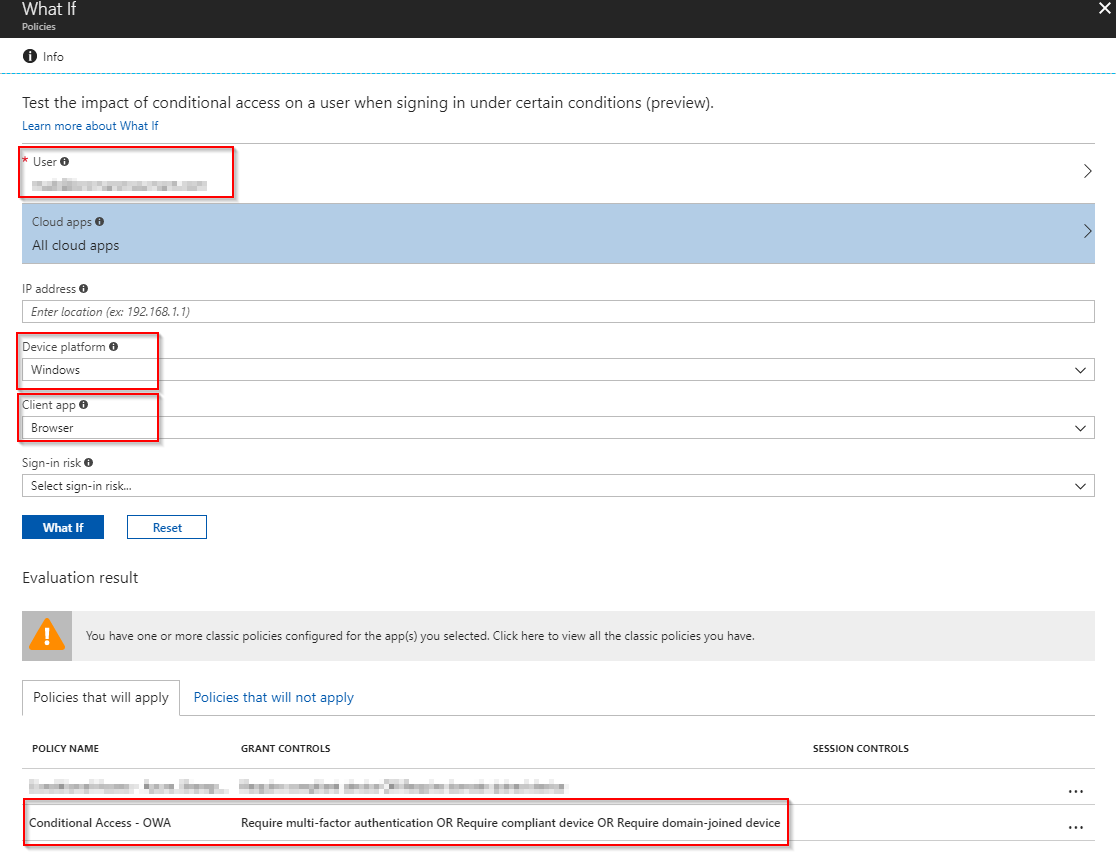
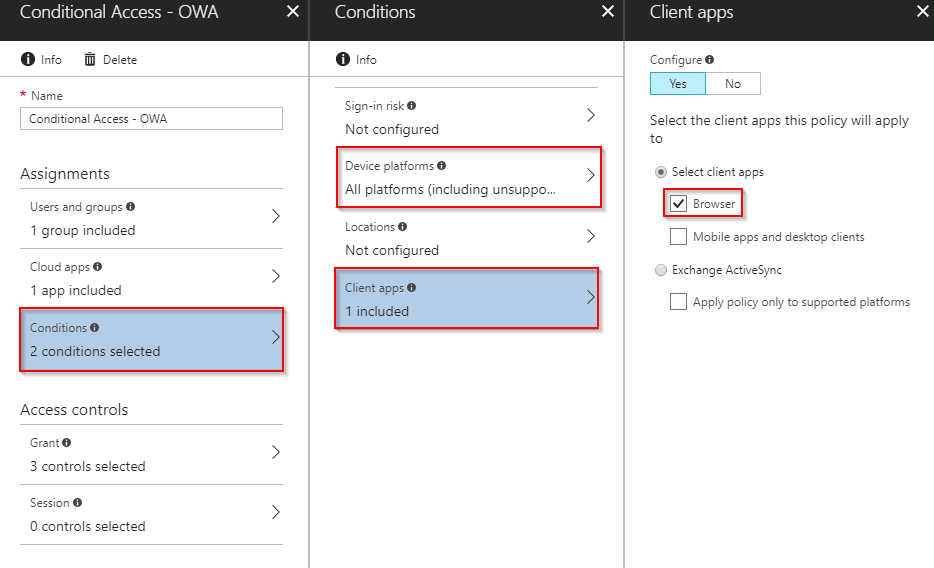
- As conditions, make sure that all device platforms are selected (as we’d like to target any browser on any platform) and select Browser in the Client apps menu.
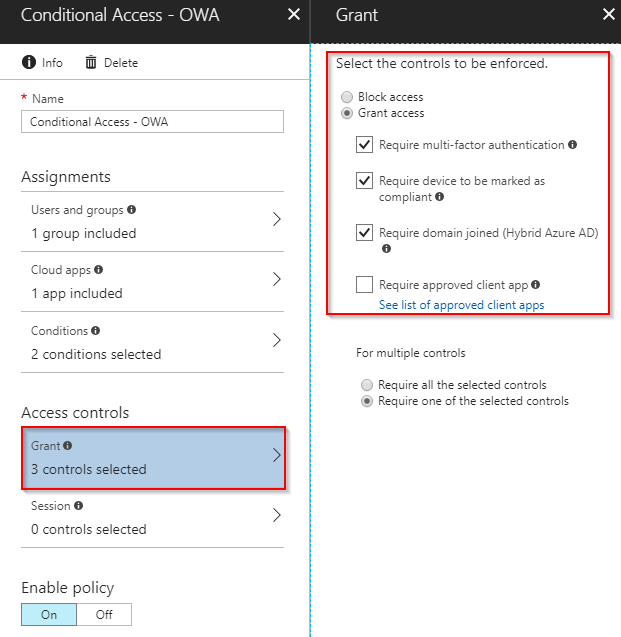
- In Access controls, select 1) Require MFA, 2) Require device to be compliant and 3) Require domain joined (hybrid Azure AD) and select that only one of these controls needs to be satisfied. Doing exactly this configuration, will make sure that if you are coming from a private device (hence not compliant and not domain joined) will trigger MFA when accessing webmail. On the other hand, coming from an Intune enrolled AND compliant device OR a domain joined PC will not require MFA.
Finally
Before enabling the policy, I recommend that you take a closer look at the new preview feature for Conditional Access, WhatIf. It will let you know the impact of your new CA policy by setting the desired conditions. It will also tell you, if you have configured any legacy CA policies in the old silverlight Intune portal which might interfere with your new CA policies.
Now, when signing into https://outlook.office365.com from my private computer, I’m required to approve the sign in request through my prefered MFA method.

Enjoy your new Conditional Access policy requiring MFA when signing into webmail (OWA) on a private device. 🙂