Introduction
Long title, but that’s actually what this post is going to cover; how you can secure the access to company e-mail accounts and only allow access to such, if coming from an enrolled (compliant) Intune device and that device uses the Outlook app.
In this scenario, we only uses iOS devices and of such only allow enrollment of iOS devices, but this can of course be android and Windows as well. Everything in this post is achievable with the use of Microsoft Intune and Conditional Access in Azure. Curious? Read on 🙂
Configuration in Intune
First off, I’m not covering the part about compliance and Compliance Policies in Microsoft Intune. For this to fully work as expected, you have to have a compliance policy (in this case iOS) assigned to your users (or use the setting that consider a device compliant, if no compliance policy is assigned. Not recommended though. Also, this requires a minimum of AAD P1 license for Conditional Access to work.
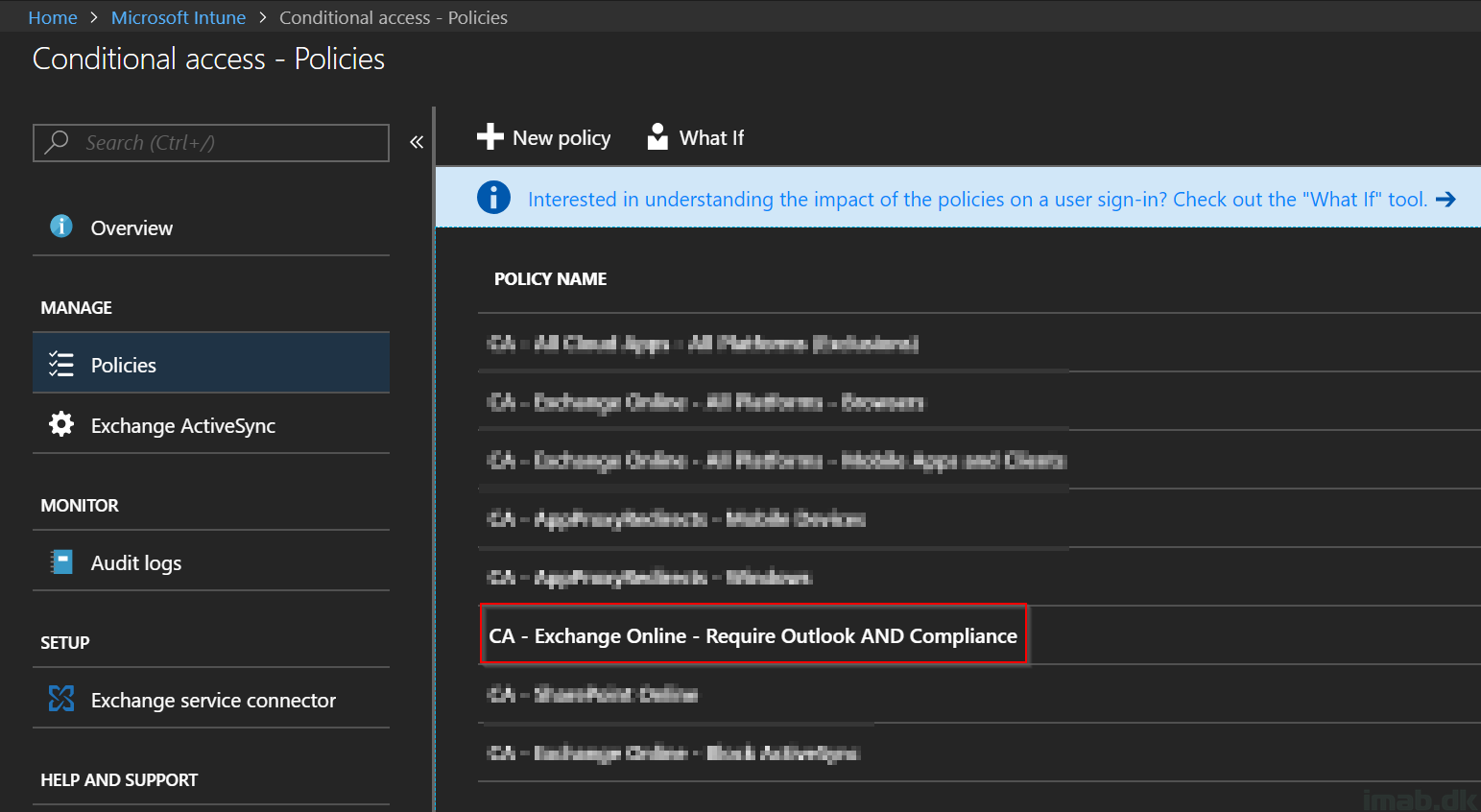
- First things first. Log into the Azure portal at portal.azure.com and locate or search for the Microsoft Intune blade and Conditional Access.
- Once located, create a new Conditional Access policy on + New Policy
- Give it a suitable name. For inspiration, mine is called: CA – Exchange Online – Require Outlook AND Compliance
- Assign the policy to the desired user or a group consisting of users (not a bad idea to test this on a single user first)
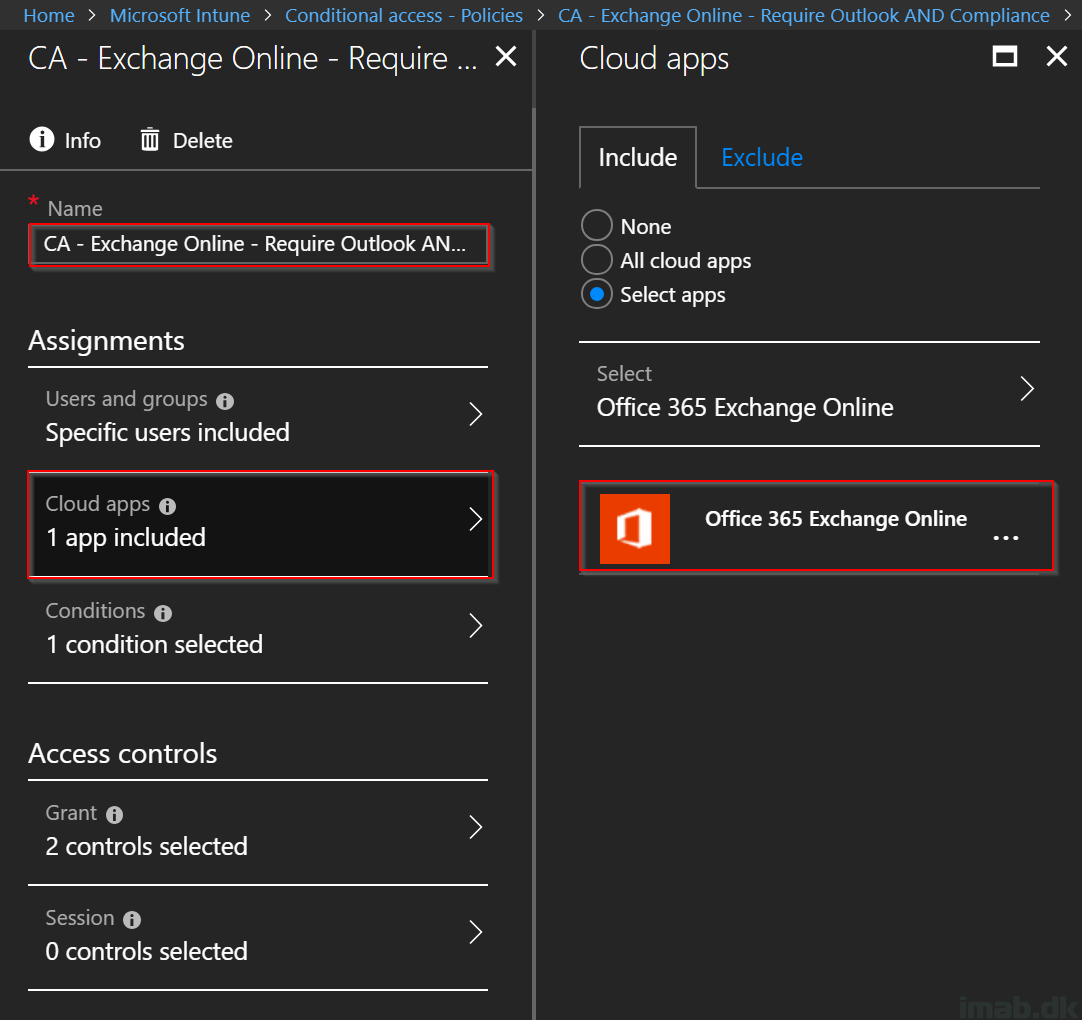
- Select Office 365 Exchange Online in the Cloud apps section
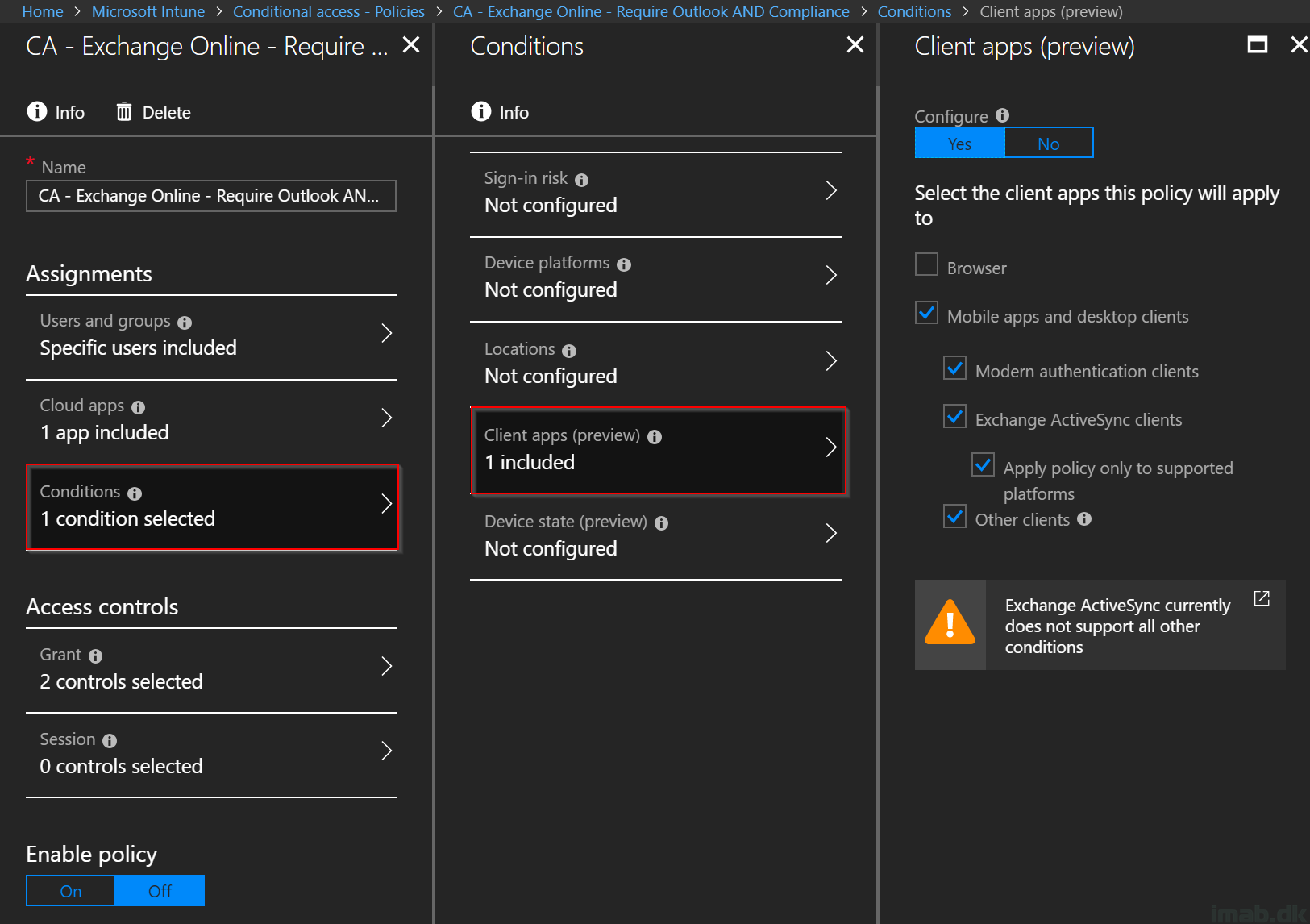
- In the Conditions section, select Mobile apps and desktop clients in the Client apps section. The extension of Modern auth. clients, Exchange ActiveSync clients and other clients is brand new (at the time of writing). Selecting all of the options is going to cover all possible scenarios
- Note that when having Exchange ActiveSync clients selected, it’s currently not supported to have any other conditions configured. As of such, the Client apps section will be the only configured in this example
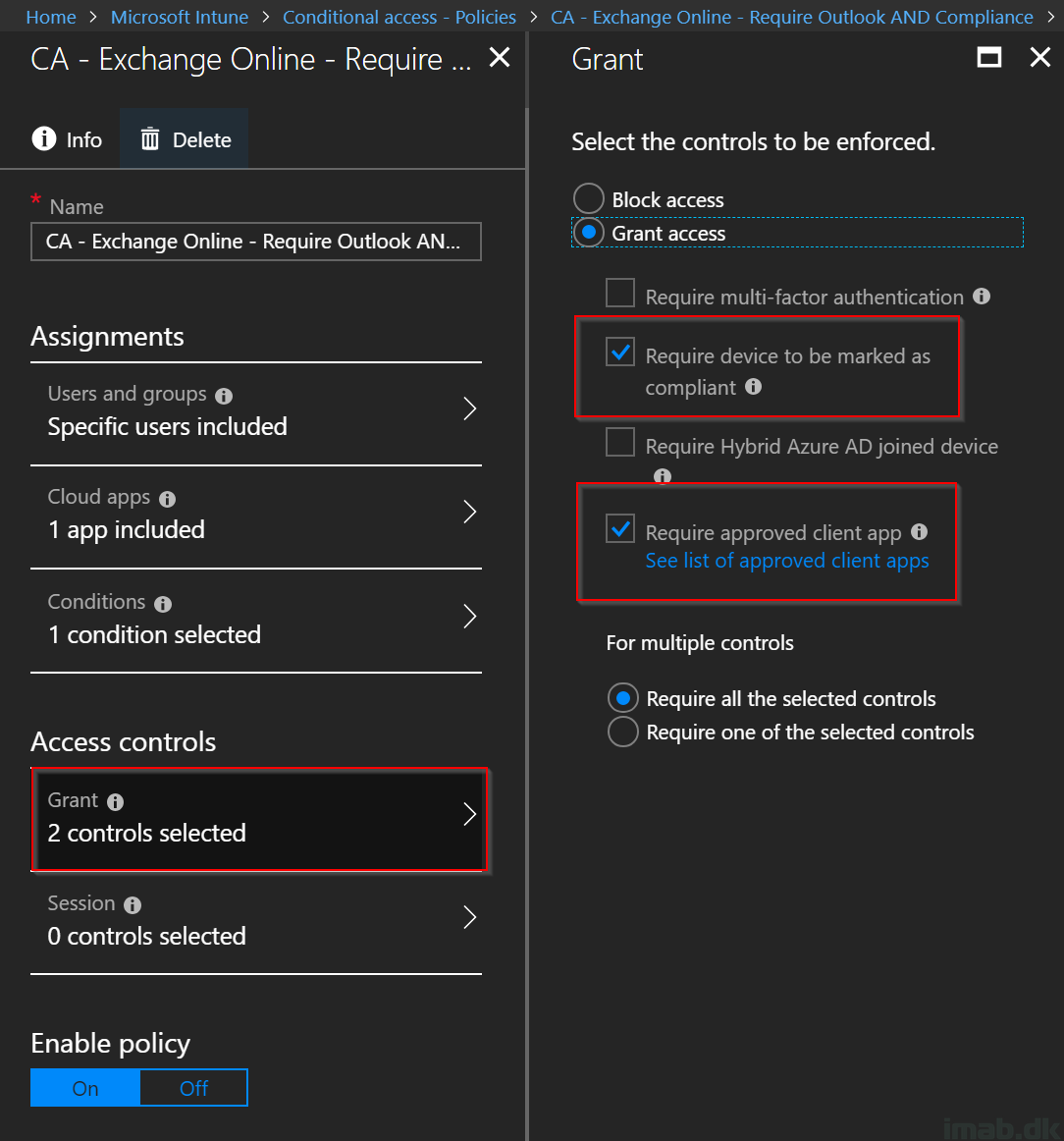
- In the Grant section, select Grant access to Require device to be marked as compliant and Require approved client app. Select Require all the selected controls as well, which logically will create an AND between the two controls and thus require BOTH of the controls
End user experience
Again, test this first. And remember to enable the policy before doing so. 🙂
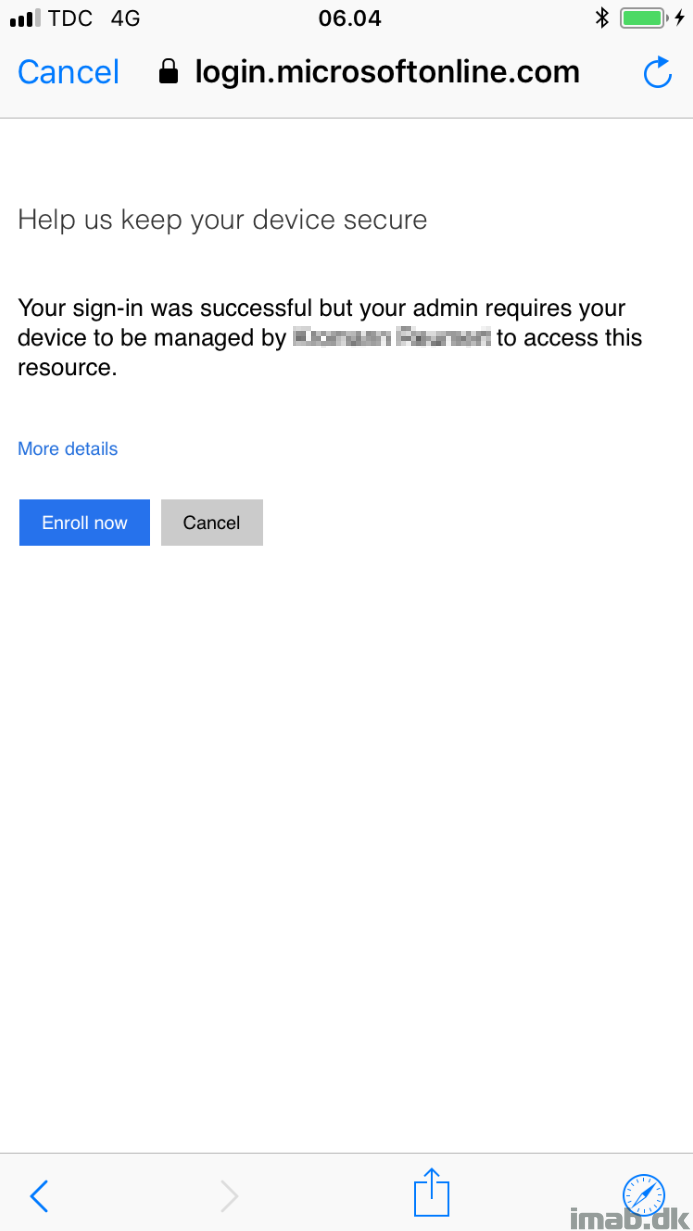
For the end user on a iOS device, there will be following experiences. First one is when trying to access a company e-mail account from a non-enrolled (non-compliant) device:
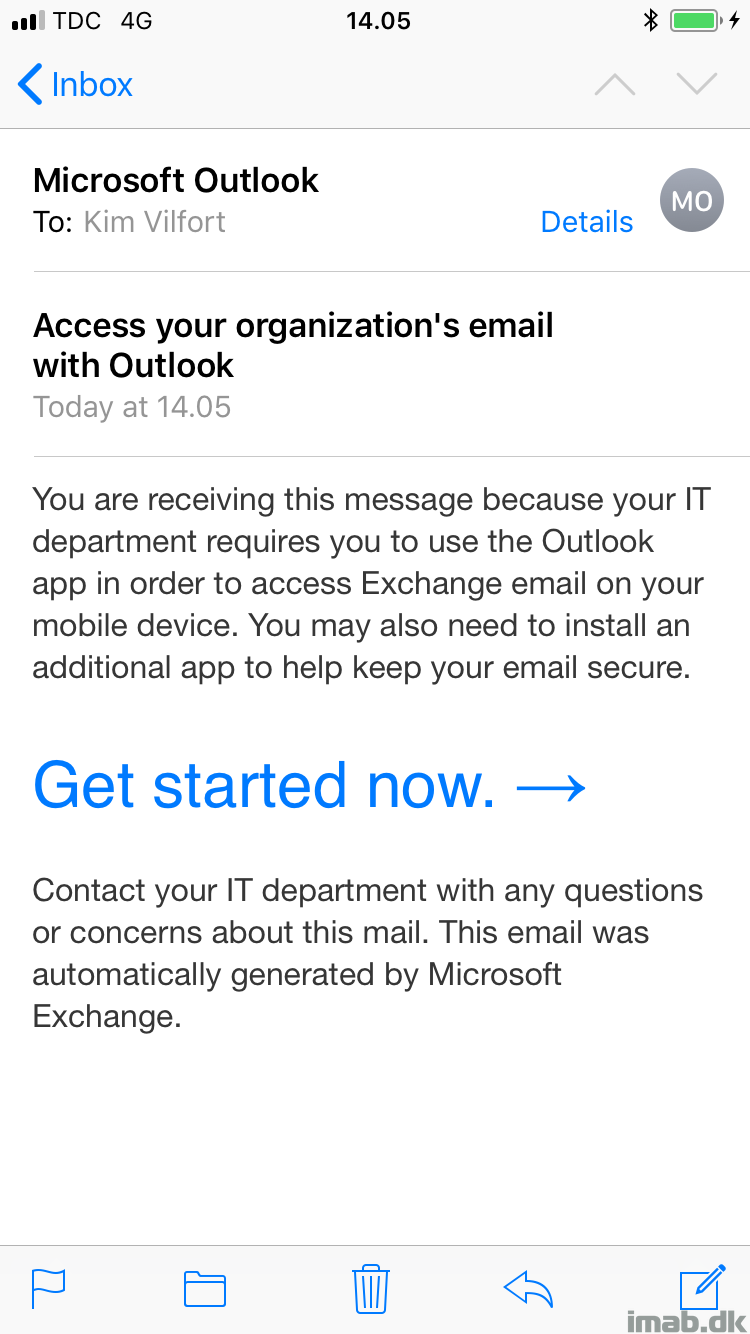
Secondly, when the device is enrolled and trying to access the same company e-mail account from the native iOS mail app:
I hope this was helpful. Please like and share 🙂
Great guide thanks for the help