Introduction
Back in May i did a post on how to leverage Powershell App Deployment Toolkit and Configuration Manager to in-place upgrade to Windows 10 1803. Find the post in the link below:
Today I’m providing you with an update on the topic and giving you an updated version of the content. Note that the basic instructions for using all of this, is still found in my original post above.
What’s new?
I have slightly modified the Powershell script initiating the in-place upgrade task sequence to no longer include the registry tattooing.
Instead, this is done in the end of the actual task sequence. See below snippet. This allows the application in the Software Center to be rerun in case something goes amiss POST running the application. Note that this will yield an error in the application until the Application Deployment Eval Cycle has run and picked up the detection method.
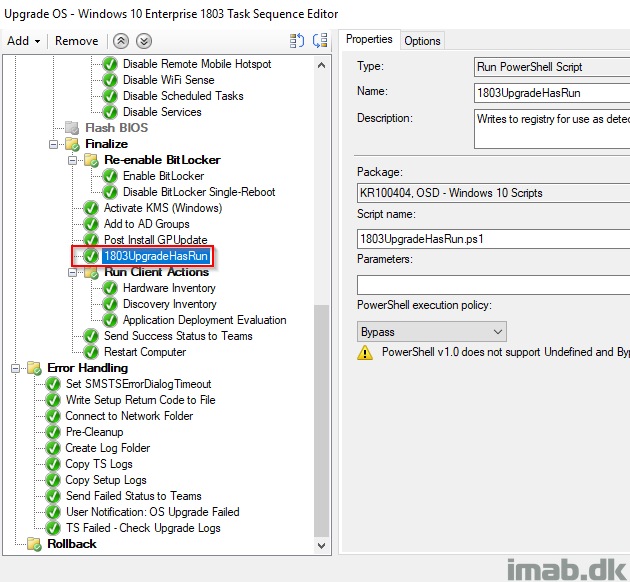
Execute-OSUpgrade.ps1
The script initiating the task sequence now looks like this:
function Write-Log {
[CmdletBinding()]
Param
(
[Parameter(Mandatory=$true,
ValueFromPipelineByPropertyName=$true)]
[ValidateNotNullOrEmpty()]
[Alias("LogContent")]
[string]$Message,
# EDIT with your location for the local log file
[Parameter(Mandatory=$false)]
[Alias('LogPath')]
[string]$Path='C:\ProgramData\Kromann Reumert\Execute-OSUpgrade.log',
[Parameter(Mandatory=$false)]
[ValidateSet("Error","Warn","Info")]
[string]$Level="Info",
[Parameter(Mandatory=$false)]
[switch]$NoClobber
)
Begin
{
# Set VerbosePreference to Continue so that verbose messages are displayed.
$VerbosePreference = 'Continue'
}
Process
{
# If the file already exists and NoClobber was specified, do not write to the log.
if ((Test-Path $Path) -AND $NoClobber) {
Write-Error "Log file $Path already exists, and you specified NoClobber. Either delete the file or specify a different name."
Return
}
# If attempting to write to a log file in a folder/path that doesn't exist create the file including the path.
elseif (!(Test-Path $Path)) {
Write-Verbose "Creating $Path."
$NewLogFile = New-Item $Path -Force -ItemType File
}
else {
# Nothing to see here yet.
}
# Format Date for our Log File
$FormattedDate = Get-Date -Format "yyyy-MM-dd HH:mm:ss"
# Write message to error, warning, or verbose pipeline and specify $LevelText
switch ($Level) {
'Error' {
Write-Error $Message
$LevelText = 'ERROR:'
}
'Warn' {
Write-Warning $Message
$LevelText = 'WARNING:'
}
'Info' {
Write-Verbose $Message
$LevelText = 'INFO:'
}
}
# Write log entry to $Path
"$FormattedDate $LevelText $Message" | Out-File -FilePath $Path -Append
}
End
{
}
}
# Name of your IPU task sequence here
$TaskSequenceName = "TEST"
$TSReferencePackageIDs = @()
# Get the Software Center
try {
$softwareCenter = New-Object -ComObject "UIResource.UIResourceMgr"
Write-Log -Message "Successfully connected to the Software Center"
}
catch {
Write-Log -Message "Cannot connect to the Software Center."
exit 1
}
# Get the Task Sequence object
$taskSequence = $softwareCenter.GetAvailableApplications() | Where-Object { $_.PackageName -eq "$TaskSequenceName" }
if ($taskSequence) {
$taskSequenceProgramID = $taskSequence.ID
$taskSequencePackageID = $taskSequence.PackageID
foreach ($i in $taskSequence.GetMemberPrograms()) {
$TSReferencePackageIDs += $i.PackageID
}
}
else {
Write-Log -Message "Failed to retrieve the Windows 10 upgrade from the Software Center."
exit 1
}
# Try executing the task sequence
try {
$RunTS = $softwareCenter.ExecuteProgram($taskSequenceProgramID,$taskSequencePackageID,$true)
}
catch [Exception] {
Write-Log -Message "$_" ; exit 1
}
1803UpgradeHasRun.ps1
For your convenience, the Powershell script tattooing the registry is provided below (this is the step I highlighted in the snippet from the task sequence above):
$Today = (Get-Date).ToString("dd/MM/yyyy")
$RegistryPath = "HKLM:\Software\YourCompany"
if (-not(Test-Path -Path $RegistryPath)) {
New-Item -Path $RegistryPath –Force
}
New-ItemProperty -Path $RegistryPath -Name "1803UpgradeHasRun" -Value 1 -PropertyType "String" -Force
New-ItemProperty -Path $RegistryPath -Name "1803RunDate" -Value $Today -PropertyType "String" -Force
Powershell App Deployment Toolkit
In regards to the Powershell App Deployment Toolkit, following are added/changed:
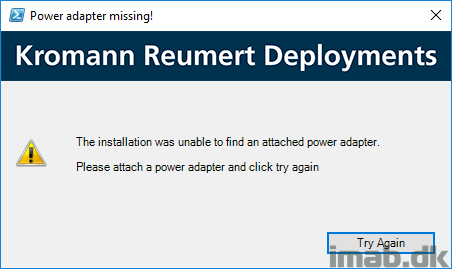
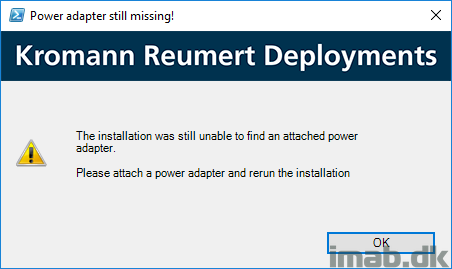
- Testing for attached power adapter
- If no power adapter is attached, allow the user to attach one and continue
- If no power adapter is attached, the script will exit the installation with exit code 1618 (fast retry in the application, which means SCCM will retry the installation 10 times every 2 hours)
- Allows the user to say no to proceeding the installation, which again will exit the installation with exit code 1618 and thus acts like a sort of deferal
Download the changes here: PSADT_1803UpgradeV2.zip (12201 downloads )
The battery check looks like below pictures.
End user experience
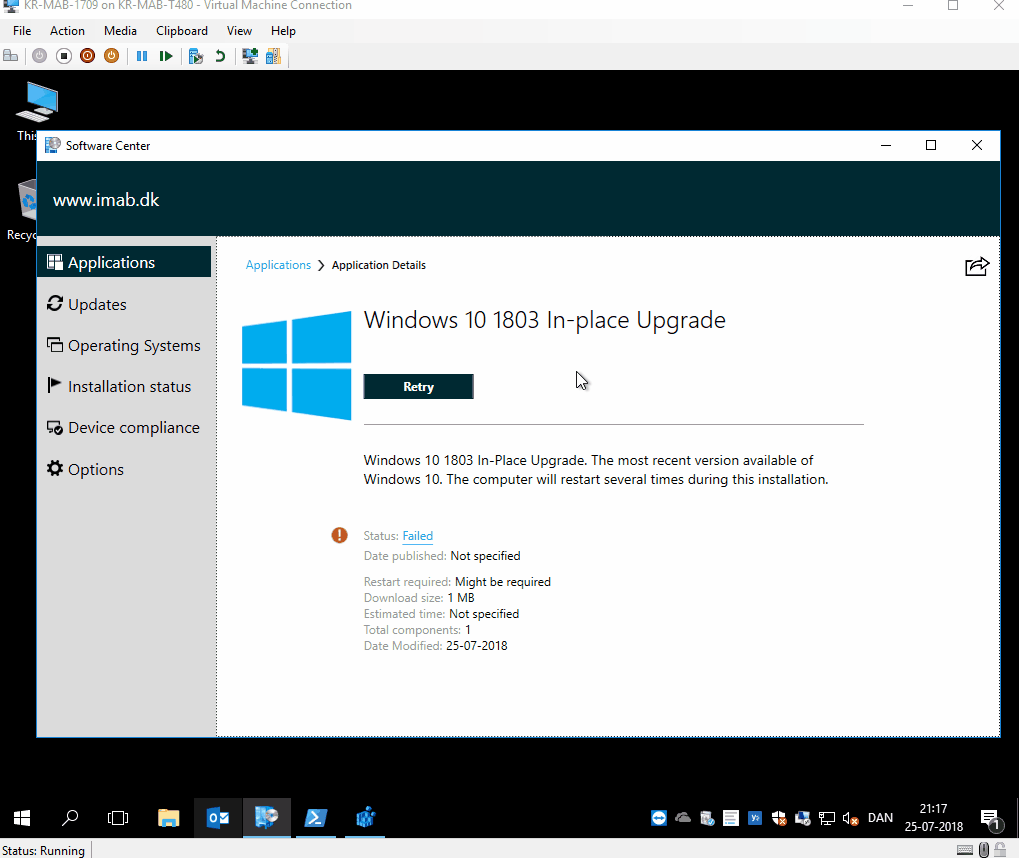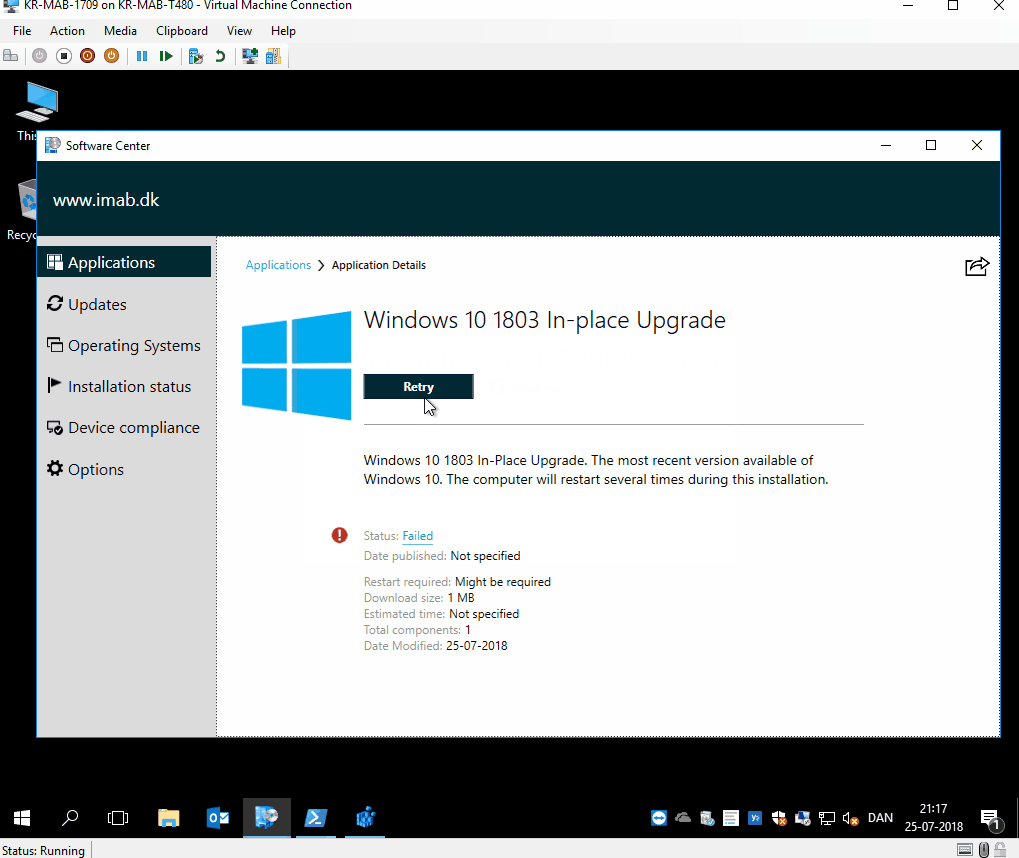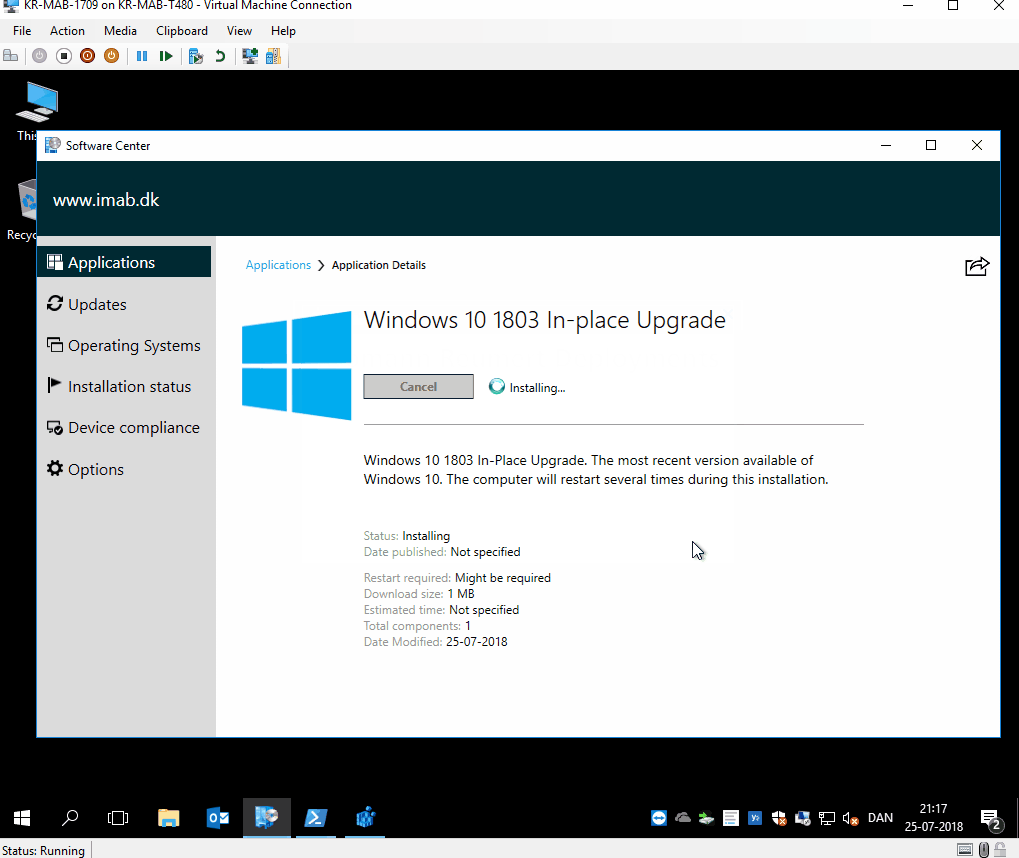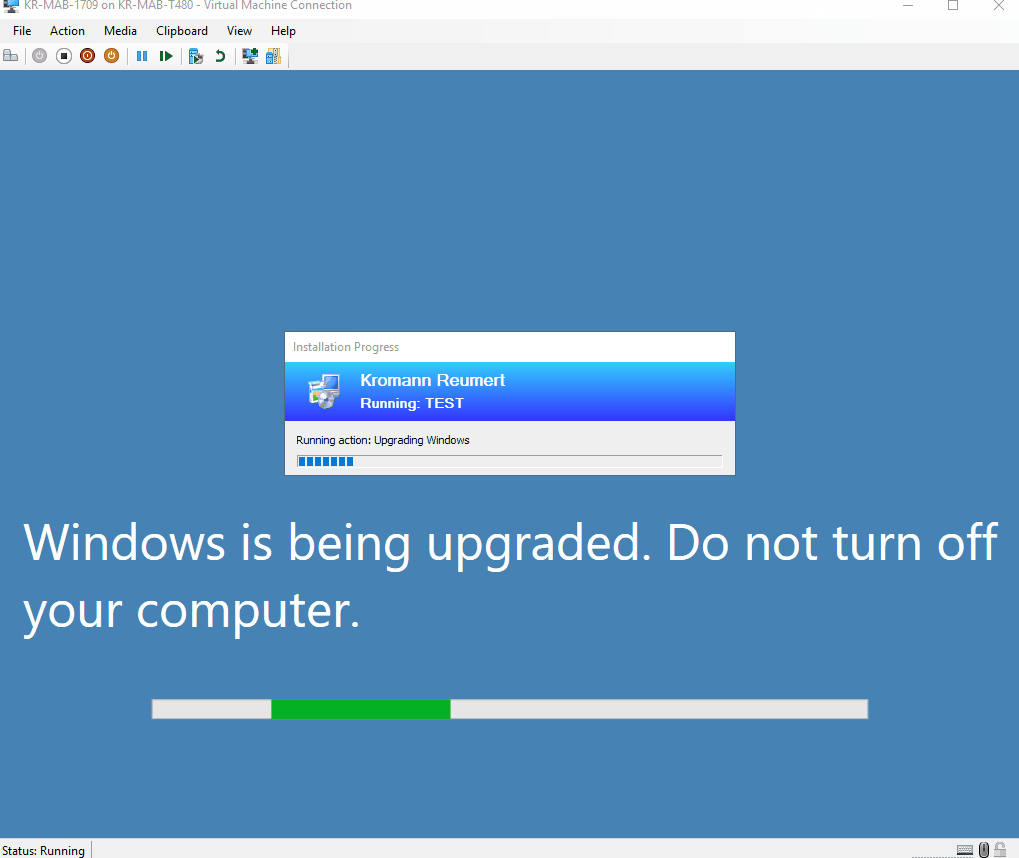
All of above was added/changed due to some comments on my previous post. Thank you for the feedback – much appreciated.
Please let me know if this is useful. Enjoy 🙂
Hi Martin Bengtsson,
can you share the task sequence you were using?
Can you share the task sequence you were using?
This is fantastic! Thank you for sharing this, it has certainly made my life a lot easier when it comes to upgrading Windows 10. Just one thing… it would be handy to have a connected ethernet check as well as the battery check. I have to update a number of Surface devices and need them to be plugged into via the ethernet adaptor before upgrading.
Thank you! Checking on Ethernet cable is perfectly doable, but in my test wasnt 100% accurate on all models why I didnt include it 🙂
Hi Martin,
has your Upgrade OS Task Sequence changed in any significant manner to cater for these enhancements?
Looking at the TS snippet you provided above it’s a bit different to the original one you shared in Part 2.
I’m still working on pulling all this good stuff together along with WaaS stuff from Mike Terrill and Gary Blok.
You three should all work together on the Mother of all IPU task sequences!
Hi Andy, yeah I believe it changed slightly. I’m still using Powershell App Deployment Toolkit to initiate the TS, but the TS I’m sharing in part 2 of my WaaS posts, is the one I’m using today. For one I’m back at tattooing the registry for the detection method in the the actual PSADT application, but enabled the option to repair it. It’s just minor things that have changed 🙂 Thank you for kind words – that’s something that motivates me 🙂
Hi Martin, your blogs for WaaS are a great inspiration! Thank you so much for all the scripts 🙂
This is a very hot topic and especially improving the user experience in the upgrades is a important thing!
Have a nice spring and be proud of your work!
Thank you so much, Tommi 🙂
I’ve just been reading through your Toast notification post which of course linked through to this. Amazing work, thank you for a) explaining your methods b) letting other people use your code and c) making our work better!
Thank you so much for providing feedback – it’s invaluable to me 🙂
Hi Martin,
In your Toast notification, what species the logo in the top left hand corner as the Software Center logo? I’ve amended one for a deployment and its the Powershell logo? thanks,
Hey Jimbo, it’s the app doing the notification, more specifically the changes to the registry I’m doing during the script. I’ve included Powershell as a second option if the toast is used on a device without sccm client, but the default should be Software Center.
Thats great thank you, I see if it now. All fixed 🙂
Hi Martin!
How should I determine the software detection when I am deploying the software upgrade?
In your previous post where you were tagging/tattoing the registry the Upgrade works like a charm because the InPlace Upgrade (The application..) can detect the tattoed registry and triggers the OSUpgrade TS, but right now, with this new “style” I am not able to reproduce the gif above. I can deny the Install one time, then I got an error, I re-run the software detection / app detection but nothing gets detected and the OS Upgrade starts automaticly, however the above gif gives a “Retry” ability. Now this does not appear for me.
Also, the 1803HasRun.ps1 need any special deployment option? User or Computer? Have to be avaiable or it have to be required?
Kind Regards,
Krisztián Mauréry
PPCU
Pazmany Peter Catholic University
Thank you for this brilliant post and amazing work. This was working for me and stopped…I am not certain what changed. I continue to have the following errors below. If anyone is still checking or have any idea’s , I am all ears. I have verified I can advertise and the task sequence downloads from the primary site.
2019-07-26 12:45:01 INFO: Successfully connected to the Software Center
2019-07-26 12:45:01 INFO: Failed to retrieve the Windows 10 upgrade from the Software Center.
2019-07-26 12:45:12 INFO: Successfully connected to the Software Center
2019-07-26 12:45:12 INFO: Failed to retrieve the Windows 10 upgrade from the Software Center.
2019-07-26 12:45:25 INFO: Successfully connected to the Software Center
2019-07-26 12:45:25 INFO: Failed to retrieve the Windows 10 upgrade from the Software Center.
2019-07-26 12:45:36 INFO: Successfully connected to the Software Center
2019-07-26 12:45:36 INFO: Failed to retrieve the Windows 10 upgrade from the Software Center.
2019-07-26 12:45:55 INFO: Successfully connected to the Software Center
2019-07-26 12:45:55 INFO: Failed to retrieve the Windows 10 upgrade from the Software Center.
Thanks.
How can we defer the restart at the end of the windows 10 update?
Hi Martin,
What about sharing the TS? How is deploying the TS? Because you have TS and Application to deploy. The both are available in Software center. It is for user difficult to know what should be installed.
Is the TS available to install or not?
Could you please to tell how is the TS to deploy?
Thanks