Introduction
Another delicious feature went GA (General Availability) this week: Security Baselines in Microsoft Intune.
The Security Baselines in Intune is the equivalent to what we have done with Group Policy for some years now, and is basically a set of pre-configured Windows settings, which are recommended for the enterprise by Microsoft.
This post is not a typical A-Z guide, but rather a first look into the feature and what initial experiences I had with moving from Security Baselines with Group Policy to Security Baselines with Intune in a Co-management scenario.
Creating the Security Baseline
First things first. A few steps covering how to create the baseline. This is pretty easy and straightforward and something that is a lot easier coming from doing this with Group Policy. If you are familiar with this process, go ahead and ignore the following paragraph 🙂
- Head into the Microsoft 365 Device Management portal: https://devicemanagement.microsoft.com
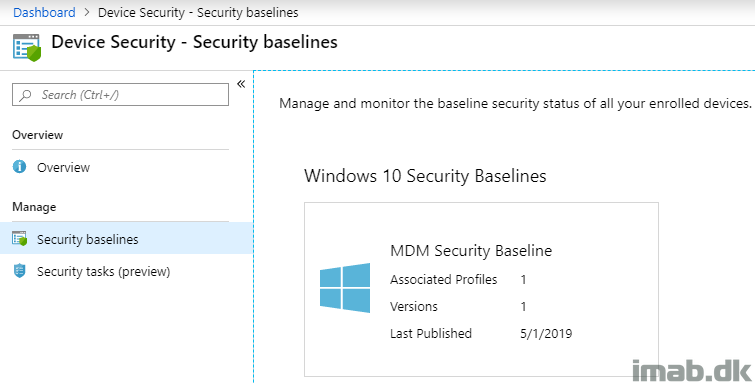
- Find and locate Security Baselines and navigate your way into Windows 10 Security Baselines
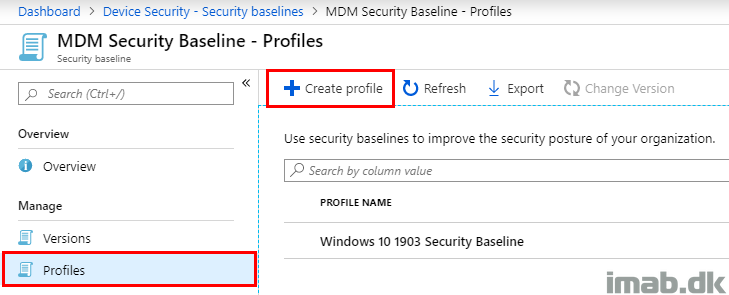
- Locate Profiles and click + Create profile
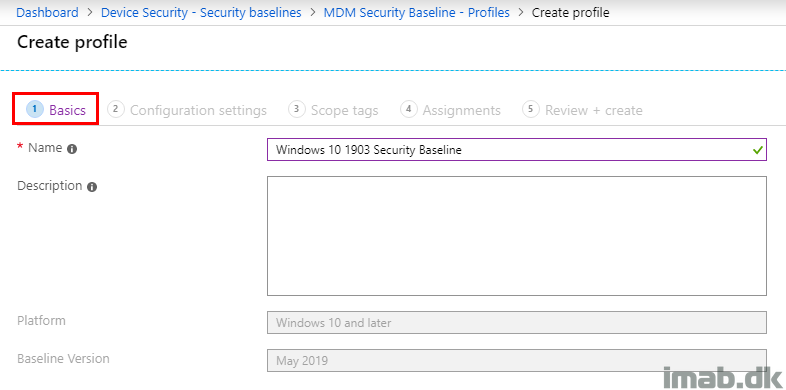
- Step 1. Give the Security Baseline a suitable name
- Mine in this example is called: Windows 10 1903 Security Baseline
- Step 2. Initially I’m keeping the defaults and thus not doing any changes to the settings of the baseline
- Step 3. Not using scope tags either. Leaving blank
- Step 4. Also leaving Assignments blank for now. Everything in here can be modified later on
- Step 5. Review the summary and create the baseline
Group for Assignment
As told in the beginning, this is not a typical A-Z guide, but rather some detailed information on what I did.
My intention here is to only target this to my Windows 10 1903 devices (The requirement for using the Baselines in Intune is minimum Windows 10 1809).
- Locate Groups -> All groups and click + New group
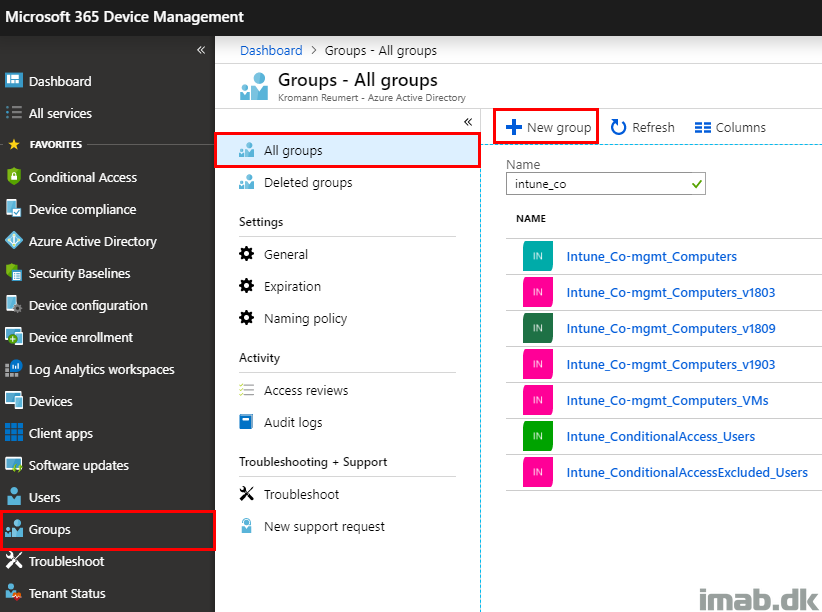
- Group type: Security
- Group name: Fill in with a suitable name
- Membership type: Dynamic Device
- Dynamic device members: (device.deviceOSVersion -contains “10.0 (18362)”) -or (device.deviceOSVersion -contains “10.0.18362”)
Assignment
- Head back and edit your newly created Security Baseline and add the assignment of the group you just created
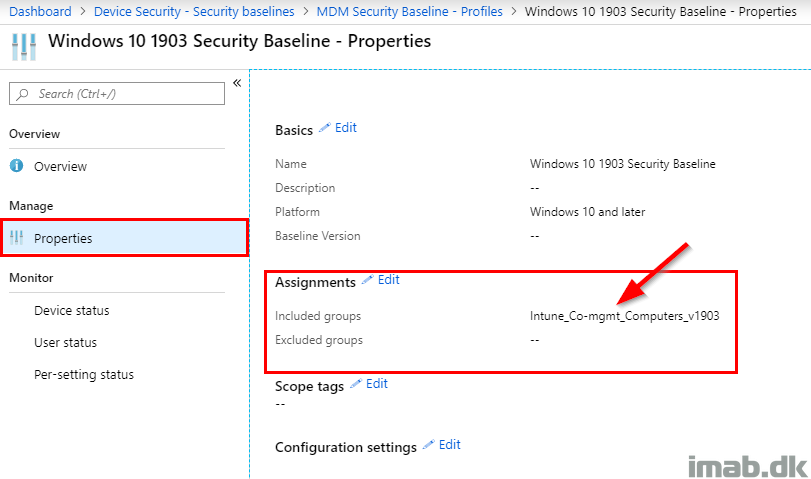
Monitoring
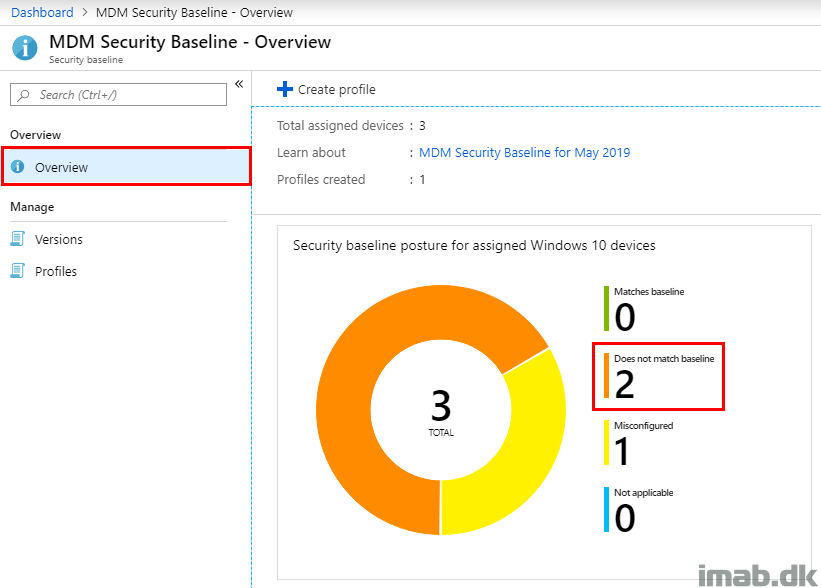
- Watch the overview for the entire MDM Security Baseline section. In my scenario, the status came out as misconfigured as shown below
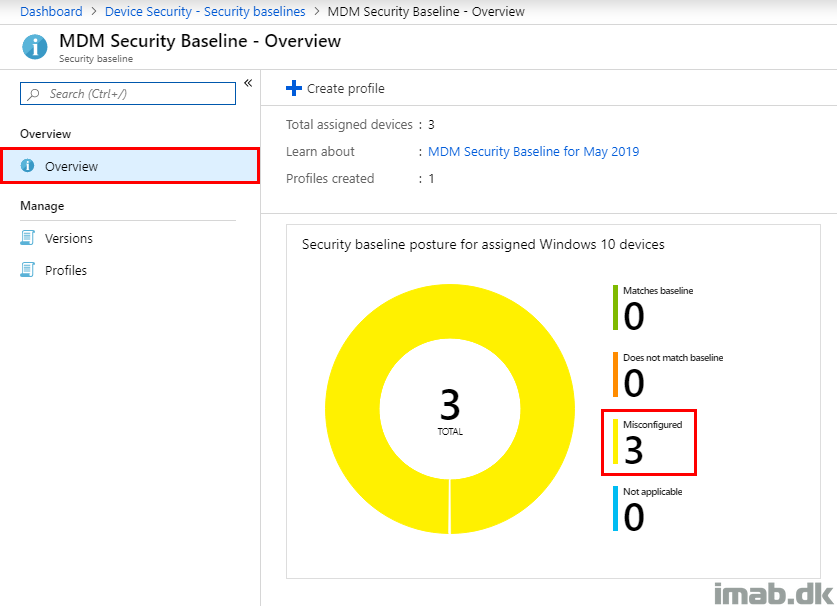
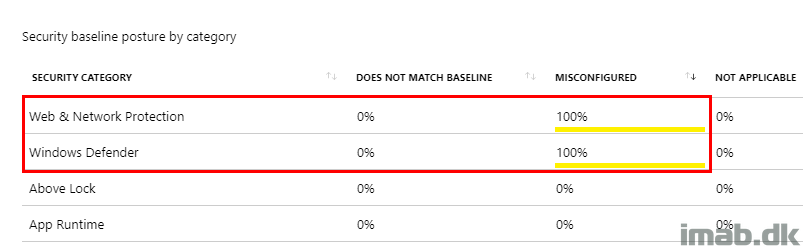
- Drilling into the posture by category, the overview highlights that something in the Windows Defender category is noted as misconfigured
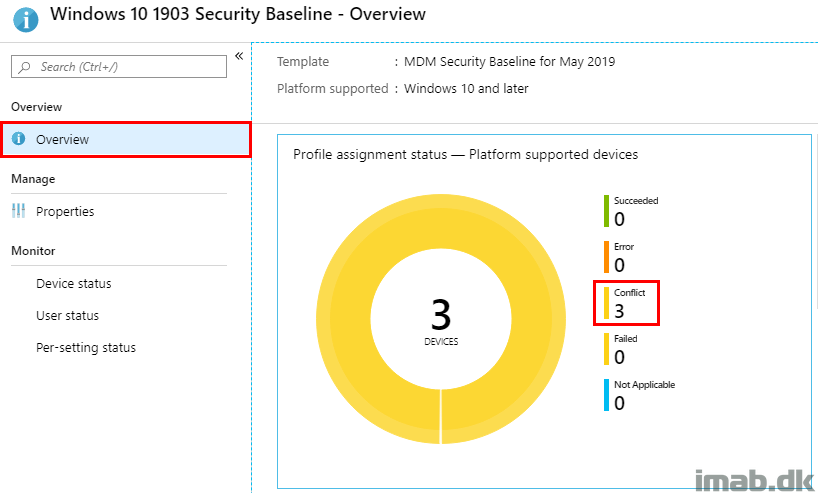
- And drilling further into the overview for the actual baseline, the devices are noted as in conflict
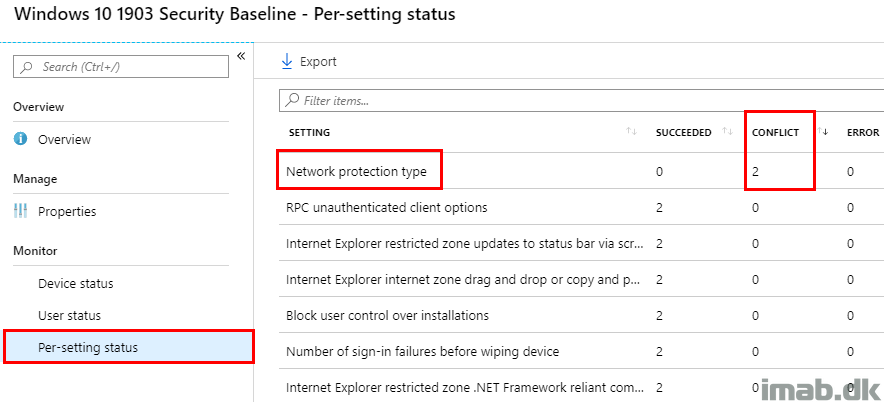
- Further to browsing the specific baseline, you will find a section called Per-setting status. Looking at this in particular, you will find the actual setting which is in conflict. In this scenario that is network protection
Reason for Conflicts
The reason for the conflicts happening in my scenario, is due to me having Network Protection in Windows Defender set to something else than what the baseline by default is dictating.
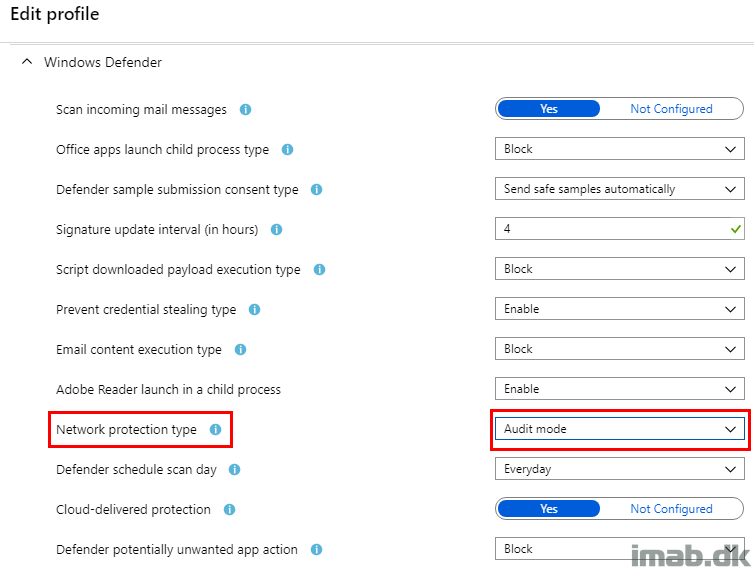
- This is confirmed by taking a look on the Device Configuration Profile for Windows Defender also assigned to the device. See below illustration
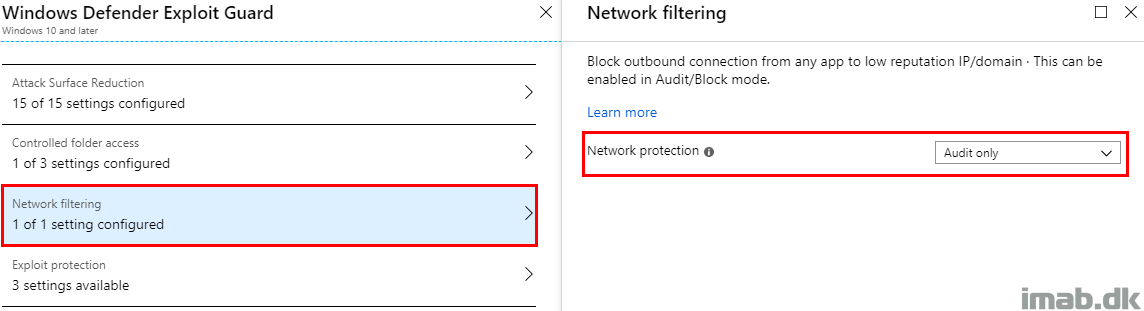
- And when comparing that to the Security Baseline, you will see a difference. I’m configuring network protection to Audit Only, where the Security Baselines wants this to be set to Enable
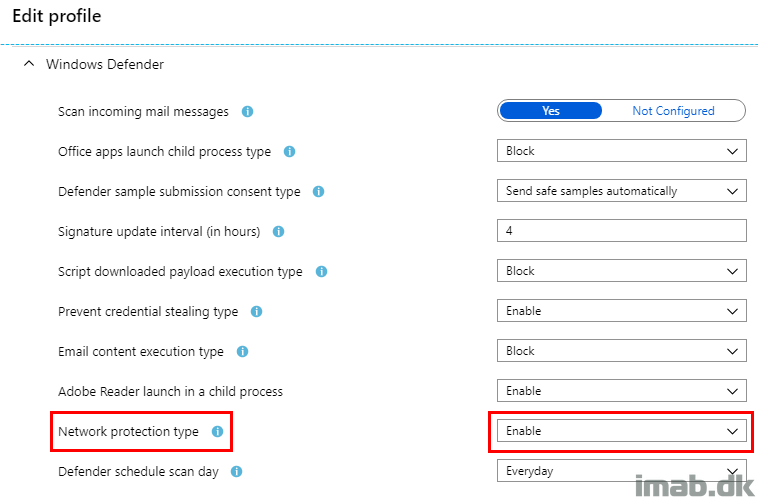
- In order to fix the conflict, I’m going to change the Security Baseline to also set Network Protection to Audit
- I currently don’t want Network Protection enabled and in this scenario the separate Configuration Profile wins while the Security Baseline will report a conflict
Monitoring again
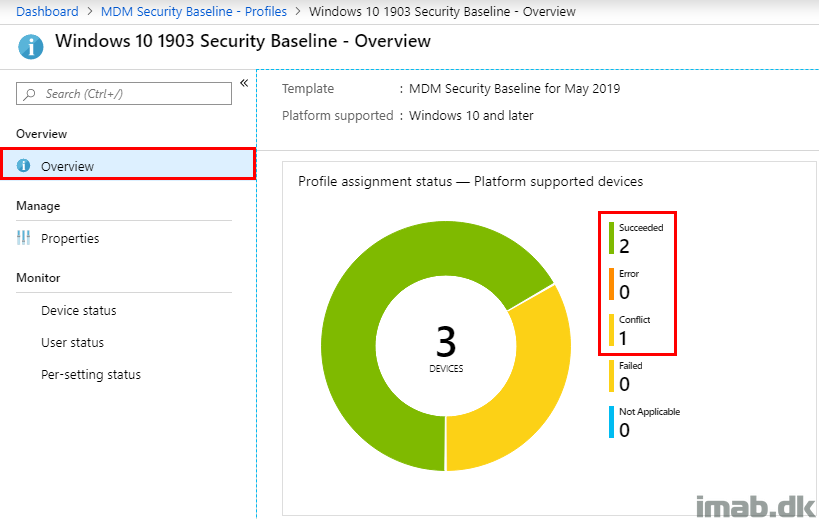
- Following above changes to the Security Baseline, we head back to the monitoring part and you will now notice that the overall posture will move the devices into Does not match baseline. This is expected, as we now differ from the default settings in the Security Baseline
- And as previously, when drilling into the actual Security Baseline, the devices are moving from conflict into Succeeded as no settings are no longer conflicting with each other
Moving from GPO to Intune
When coming from Security Baselines with Group Policy into Security Baselines in Microsoft Intune, there are 2 additional things that might be interesting.
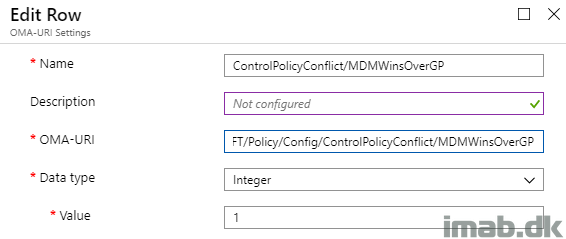
MDMWinsOverGP
This is a CSP policy, which when assigned to the device, can make sure that the MDM policy wins when its equivalent Group Policy also is applied to the device.
More info here: https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-controlpolicyconflict
WMI Filter
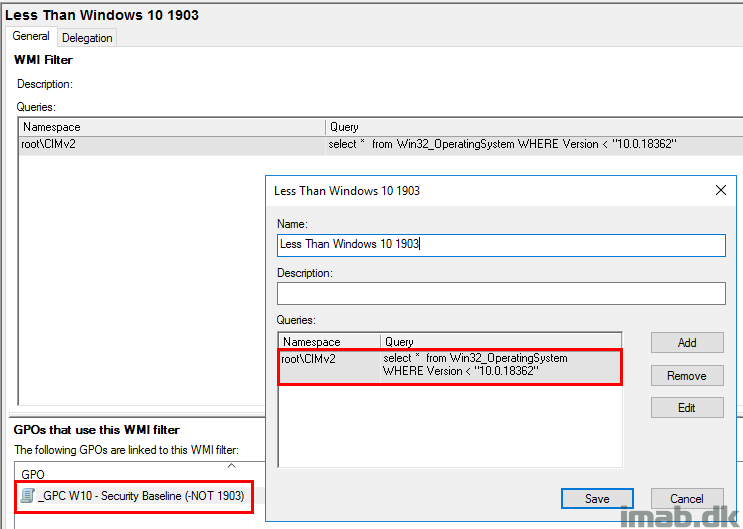
If you currently have the Security Baseline applied with Group Policy, consider making the switch to Microsoft Intune following a new version of Windows 10 and leverage a WMI filter on the GPO.
Below is an example, where my “old” Security Baseline only applies to Windows 10 versions less than 1903, making sure that my 1903 devices moving forward only is targeted with the settings from Intune.
ENJOY 🙂