Introduction
A few days ago Microsoft released a new extension for the Google Chrome browser. More specifically, they released the Windows Defender Browser Protection extension, which leverages the same security technologies used by Microsoft’s own browser; Edge. Microsoft describes their new extension with following words:
The Windows Defender Browser Protection extension helps protect you against online threats, such as links in phishing emails and websites designed to trick you into downloading and installing malicious software that can harm your computer.
With that in mind, why not make that a permanent part of securing your environment and do so by forcing an automatic installation and thus render the users unable to disable or remove the extension. Read on, this is how you can do that using Configuration Manager.
Configuration Manager
As an initial note, this can of course be done with group policies as well (Google provides their own administrative templates for this purpose). But when speaking modern management and how we should consider moving workloads away from on-premise infrastructure, I actually think managing this through Configuration Manager is considered more modern than an old fashioned group policy. Another consideration is computers not joined to a domain. No domain, no centrally managed group policies. Also, ConfigMgr just rocks! 🙂
Configuration Item
- Create a new Configuration Item. This is done in the Configuration Manager console, in the Assets and Compliance work space
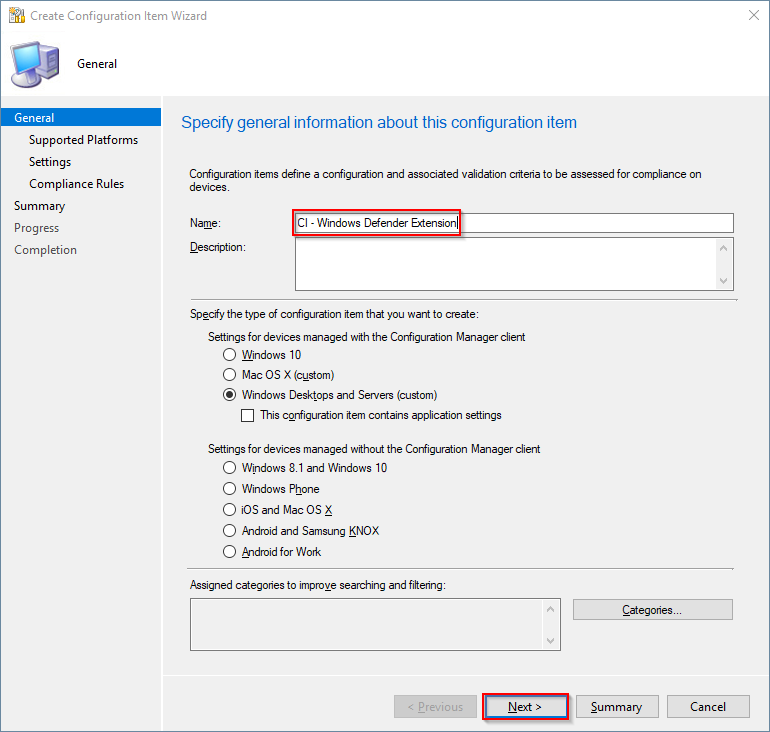
- Give it a suitable name and click Next
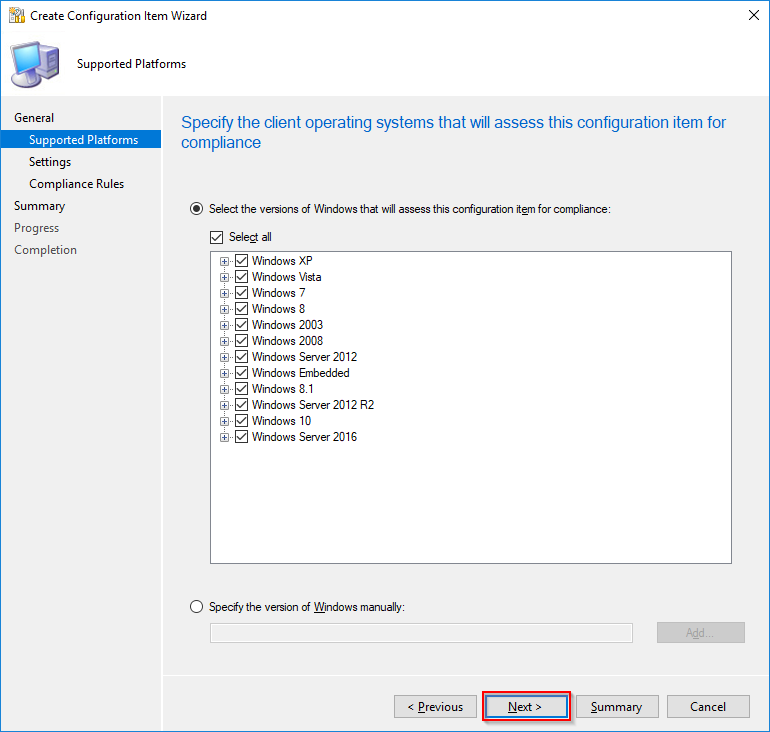
- Select the appropriate platforms for where the Configuration Item is expected to run and click Next
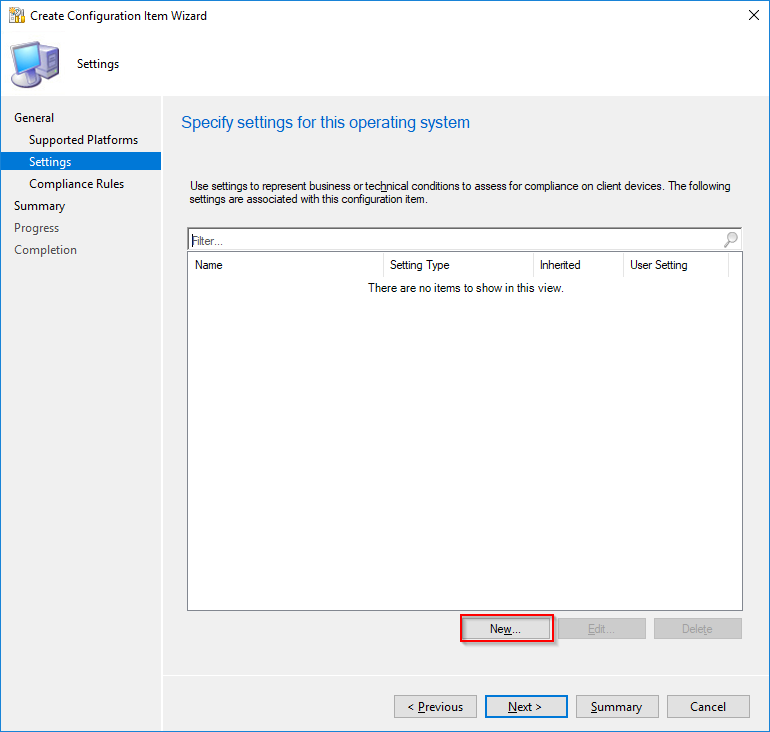
- Create a new settings configuration. Click New
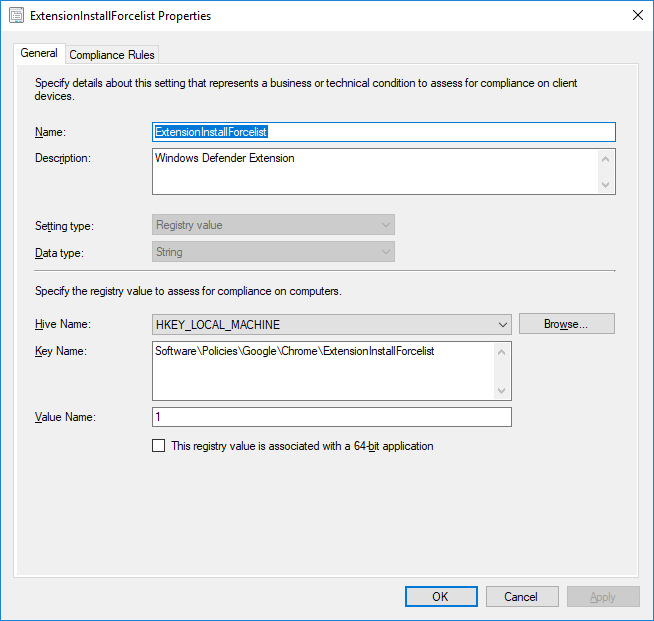
- Fill out the new settings configuration as shown below:
- Name: ExtensionInstallForcelist
- Description: Windows Defender Extension
- Key Name: Software\Policies\Google\Chrome\ExtensionInstallForcelist
- Value Name: 1 (This number is unique. Are you planning on adding other extensions this way, these should be added as 2, 3 and so forth)
- Create a new Compliance Rule
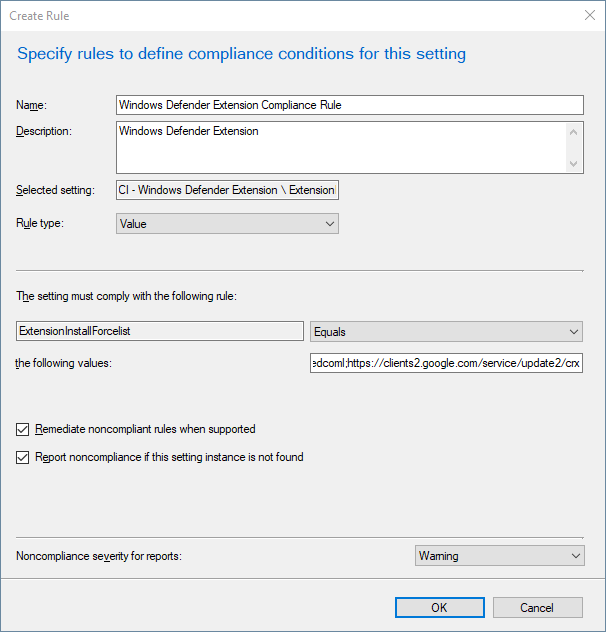
- Fill out the Compliance Rule as shown below:
- Name: Windows Defender Extension Compliance Rule
- Description: Windows Defender Extension
- Value: bkbeeeffjjeopflfhgeknacdieedcoml;https://clients2.google.com/service/update2/crx
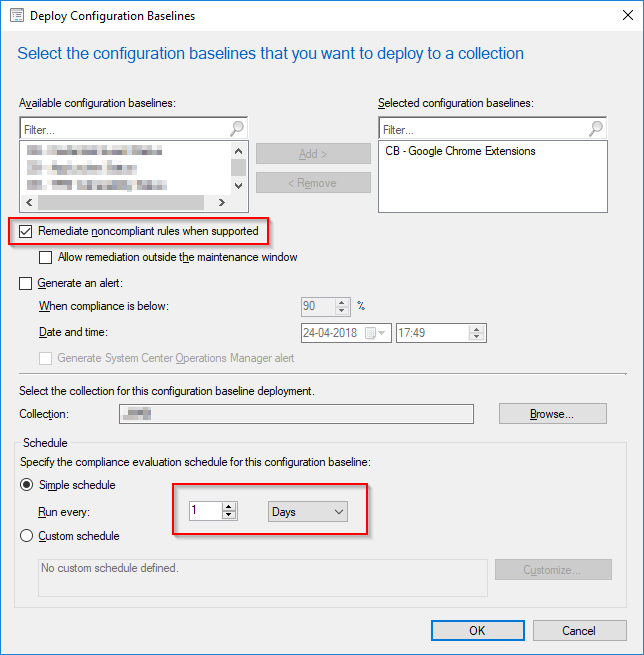
- Tick ON Remediate noncompliant rules when supported and Report noncompliance if this setting instance is not found
- Click OK and finish the wizard
- Close the usual completion window
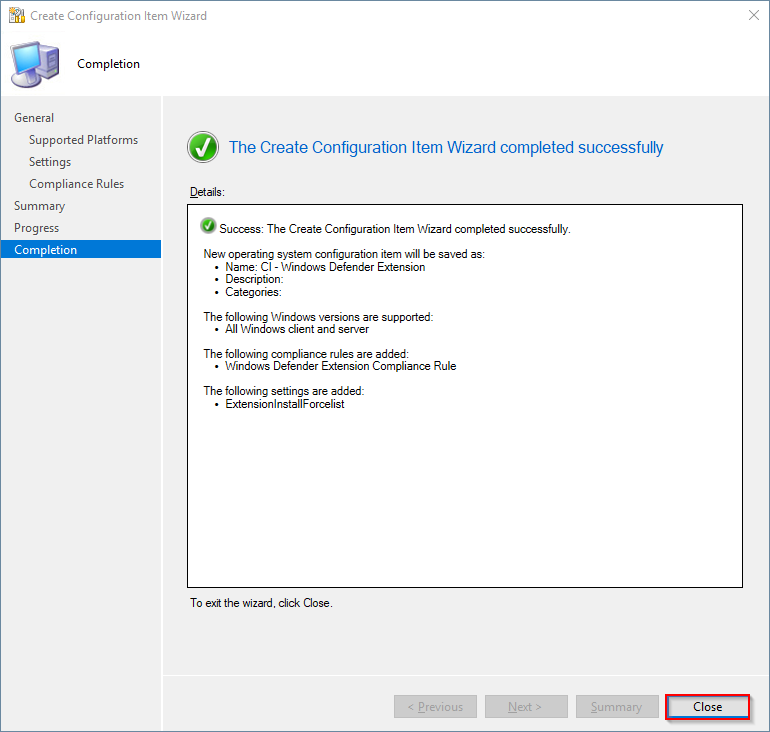
Configuration Baseline
There is no deployment of a Configuration Item without a Configuration Baseline, so it goes without saying (almost) that we also need to create a baseline for the purpose (unless you have an existing you will rather use)
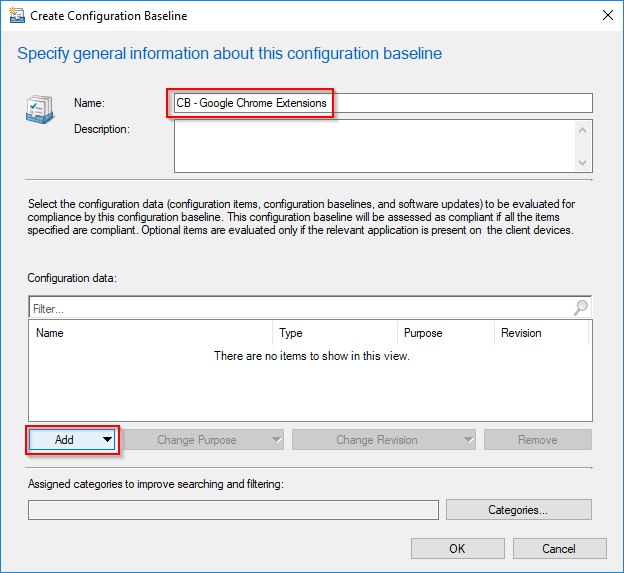
- Create a new Configuration Baseline in the Configuration Manager console, in the Asset and Compliance work space.
- Give it a suitable name and click Add > Configuration Item
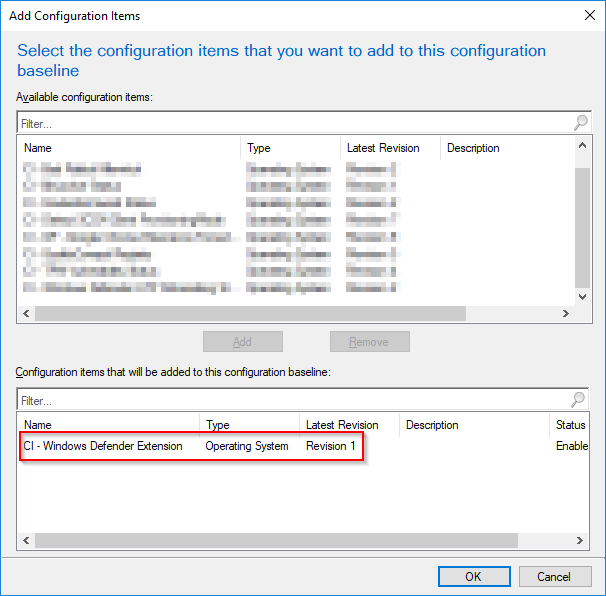
- Add your newly created Configuration Item and click OK
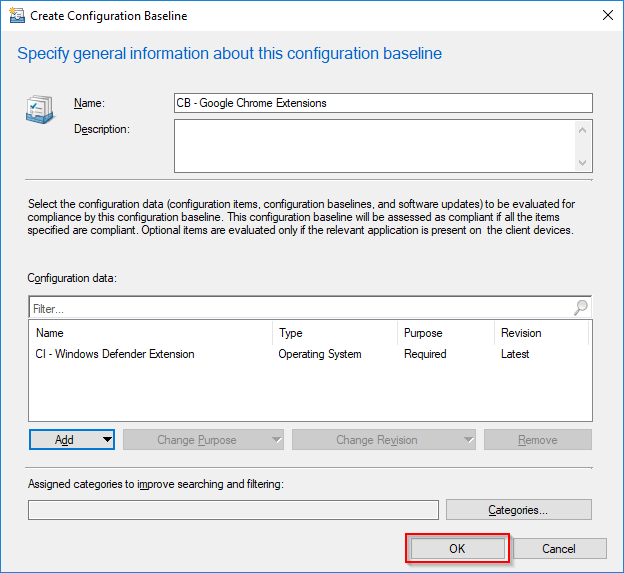
- Complete the creation of the Configuration Baseline on OK
Deployment
Finally the Configuration Baseline consisting of your Configuration Item needs to be deployed. When deploying the baseline, remember to tick ON Remediate noncomliant rules when supported. Also, consider how often the compliance should be evaluated. For comparison group policies updates per default every 90 minutes. If this is replacing a GPO, consider to lower the schedule.
End user experience
Once the SCCM client has updated its policies (Machine policies) and the Configuration Baseline has run, you will notice the extension being installed automatically and without an option to remove or disable it.
Test it!
A friendly comment reminded me of the Windows Defender Demo site. Head over there and test your new extension: https://demo.wd.microsoft.com/
Please share and leave a comment, if this was useful 🙂
Shouldn’t this say to tick on?
“remember to tick off Remediate noncompliant rules when supported”
You are absolutely right – my apologies. I will correct it asap. Thanks!
The extension can be set to be turned off even though it is forcibly deployed (also via Chrome Enterprise GPO ADMX templates). Is there a way to ensure the “Safeguard against suspicious and malicious sites” On/Off option within the extension is forced on?
The extension can also be tested here which is helpful: https://demo.smartscreen.msft.net/
Right, I noticed that as well. I actually don’t know. I’ll that as a note – thank you 🙂
somebody already found how to disable the switch button to desactivate safeguard
Do share knowledge 🙂
I know this is an old thread but I would like to know how to disable the switch as you mentioned someone has already found a way to disable it. Thanks
I also wish to know how to disable the “Safeguard against suspicious and malicious sites” switch and force it to be enabled in Incognito mode as well.
Where do you find the compliance rule value of bkbeeeffjjeopflfhgeknacdieedcoml;https://clients2.google.com/service/update2/crx? I assume it’s not the same for every extension you want to add.
Each extension, once installed, leaves behind a .json file in the users profile (\AppData\Local\Google\Chrome\User Data\Default\Extensions\bkbeeeffjjeopflfhgeknacdieedcoml\1.653_0). This file contains the details you will need 🙂
You can also find it when you browse the extension in the browser:
https://chrome.google.com/webstore/detail/lastpass-free-password-ma/hdokiejnpimakedhajhdlcegeplioahd?hl=en-US
Key part in this case being : “hdokiejnpimakedhajhdlcegeplioahd”
How to remove the Chrome Extension you just created in Configmgr if need be?
Delete the registry keys instead of adding them 🙂
Thanks!!!
Thank you! 🙂
How do you force it to be pinned on the toolbar in chrome? Thanks
So I’ve followed this for another extension I am trying to deploy through SCCM.. however my test machine that I am deploying to is stuck on 0% compliance and “Action – Remediate”.
I have checked that the string is correct (for reference I am installing the “Windows Accounts extension, ppnbnpeolgkicgegkbkbjmhlideopiji”
Does anyone have any ideas?? Thanks!
How do you do this if you only have LOCAL copy of the extension and not via google, in your example ID is the first part then semicolon then the site where it getting the extension
bkbeeeffjjeopflfhgeknacdieedcoml;https://clients2.google.com/service/update2/crx
can I do the same if I put a local path or can I do it file:\\\c:\…
Thank you!
Hi there,
Greetings!!
I have used this article to deploy the extension policy and it has worked great, Thanks a lot!
The only thing is the extension is not pinned near to search bar rather it is hidden in the extension icon, Are there any settings in the baseline to make the extension pin to the user?