Introduction
Co-management! It was announced last year at Ignite in Orlando and it’s being pushed heavily these days by Microsoft. For those who don’t know the ups and downs, co-management is basically (for those using ConfigMgr already) managing computers with both a Configuration Manager client and Intune MDM.
There are different possibilities to achieve co-management. It may sound complicated, but it’s not. I will walk you through the few steps required, as well as cover the precise prerequisites and how to troubleshoot issues if any. Note: This is precisely how I have done in a production environment. Curious? Read on 🙂
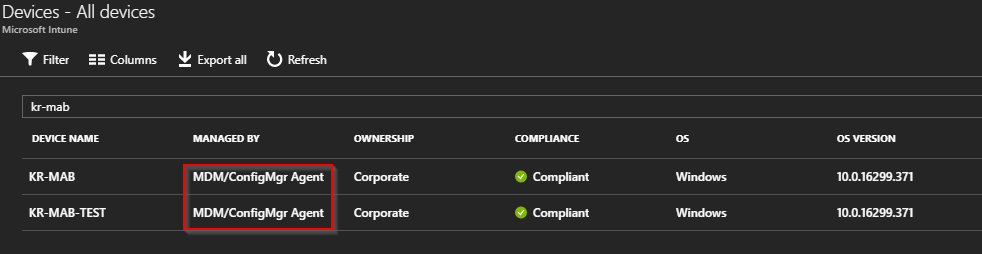
How to?
First off, there are a few prerequisites for this to be successful. Companies using Intune and ConfigMgr today, will most likely already comply with those. In this co-management scenario (Hybrid joined computers with Co-management in ConfigMgr), we have following prerequisites:
- Configuration Manager Current Branch version 1710 or later
- Azure AD
- EMS or Intune licensed users
- Azure AD automatic MDM enrollment enabled
- Intune subscription (MDM authority in Intune set to Intune)
- Note: This does not work if you are running a SCCM/Intune hybrid setup. Another good reason to start migrating now.
- Windows 10, version 1709 (and later)
- Hybrid Azure AD joined (joined to on-premise AD and (or registered in) Azure AD)
Hybrid Azure Active Directory joined devices
- This is a very fundamental requirement for this to work. I will not go into details on this part, but everything you need to know is outlined in a single Microsoft Docs: https://docs.microsoft.com/en-us/azure/active-directory/device-management-hybrid-azuread-joined-devices-setup. Again, my assumption here is that most companies using ConfigMgr/Intune and Windows 10 already have their devices registered/joined to Azure AD.
Azure AD automatic MDM enrollment enabled
This one is fairly simple. We need to allow users to enroll their Windows 10 devices into Intune. This is done in the Azure portal with a few clicks:
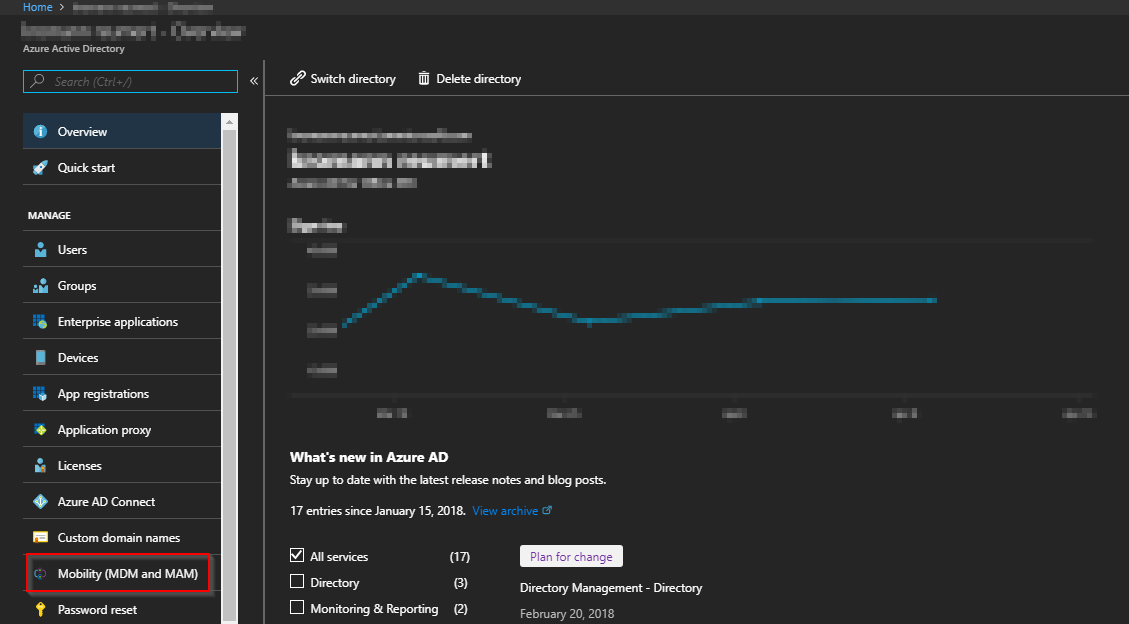
- Log into the Azure portal and bring up the Azure Active Directory
- Find and click on Mobility (MDM and MAM)
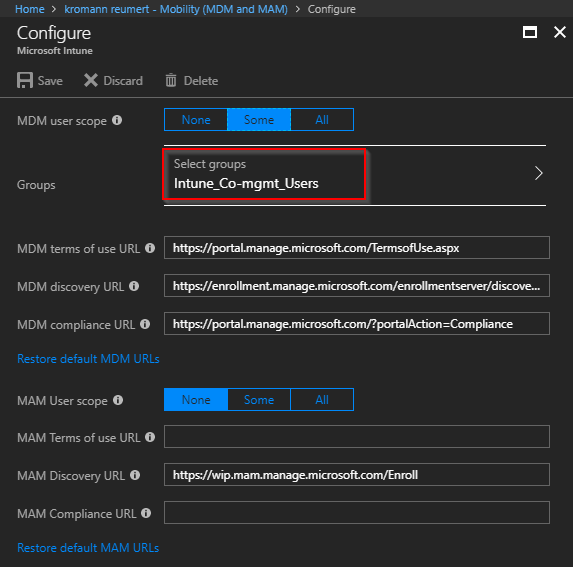
- Click on Microsoft Intune (the only option) which will display below options in the Configure blade
- Configure MDM user scope as it suits your environment. (this is the only part that is being configured). Some would argue that selecting All users is the way to go. I have a sort of OCD in this regard, where I know that the feature itself doesn’t work for users without an EMS license, and therefore I always restrict such feature to those who has. (behind that logic lies a Powershell script that syncs o365 licensed users, with additional groups. In this example Intune_Co-mgmt_Users). Also, for initial testing, I suggest you just select a few users.
Configuration Manager
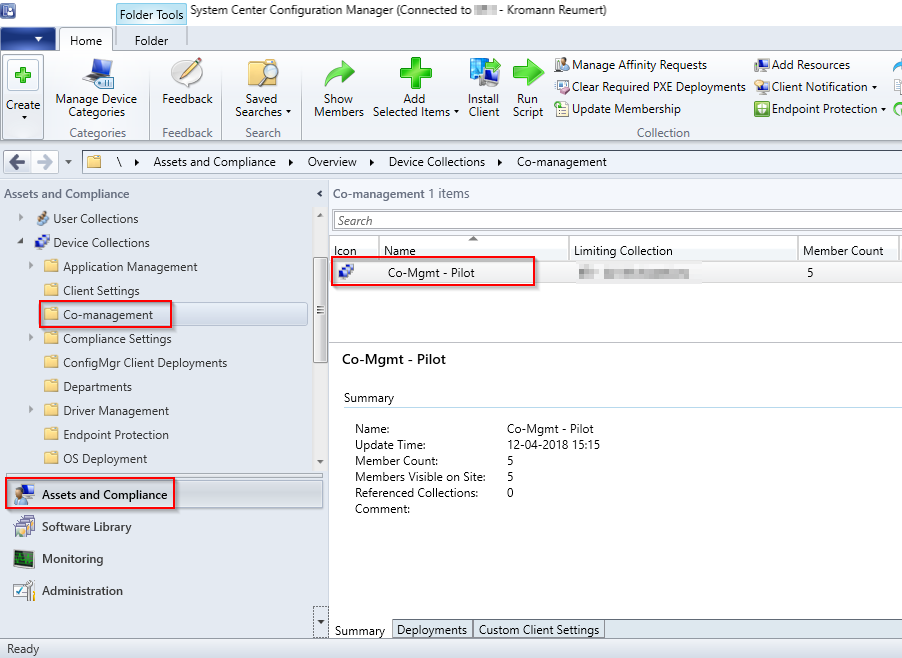
- Note: This step is only required if you want to pilot co-management on selected computers before releasing it in the wild (I recommend piloting before releasing anything in production).
- Before actually enabling Co-management in Configuration Manager, we need a collection for targeting the new Co-management policy. Remember, this only works for Windows 10 1709, so I’d recommend creating a dedicated collection only consisting of Windows 1709 clients. For your inspiration, mine looks like this.
- Next, enable Co-management. (Administration -> Cloud Services. Right click on Co-management and select Configure co-management)
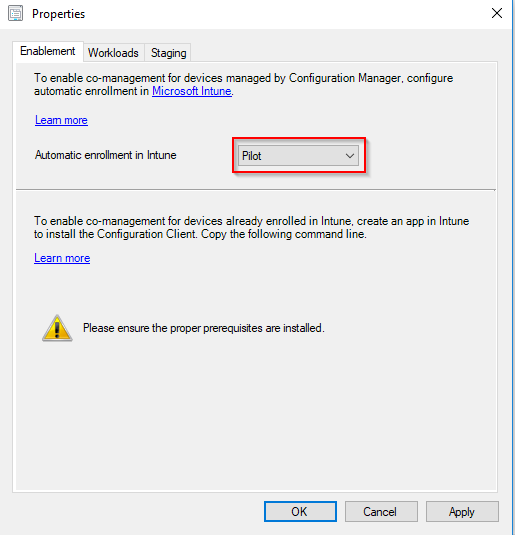
- My Co-management policy looks like this. Selecting pilot will enable you to limit this to a collection (recommended)
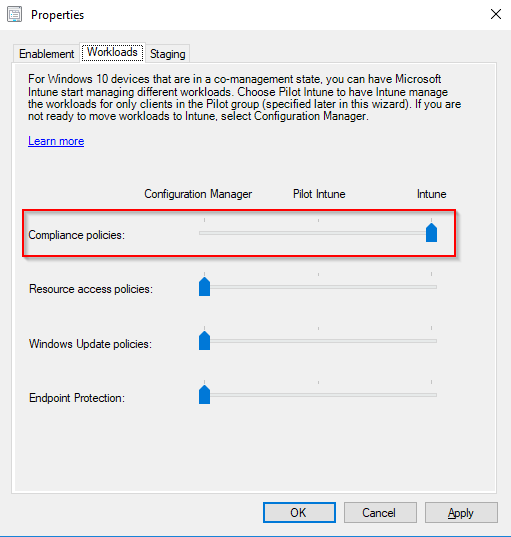
- Compliance policies are probably the first choice for most. This can of course be modified later on.
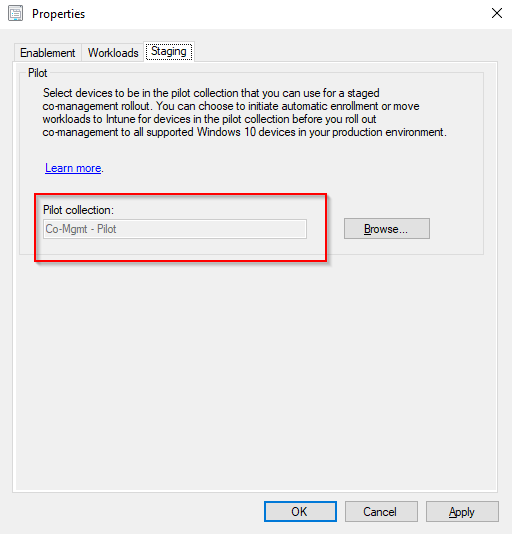
- Limit on the collection we created earlier. In this example Co-mgmt – Pilot
What else?
Actually, that’s about it in terms of configuration and setup: Your Windows 10 1709 devices are joined/registered with Azure, you allow certain users to enroll them in Intune and you have enabled co-management in Configuration Manager and deployed the co-management profile to a pilot collection. What else do you need to know?
Monitor the deployment
- Head to the Monitor node, select Deployments and search for CoMgmt. This will display the deployments of the co-management profile.
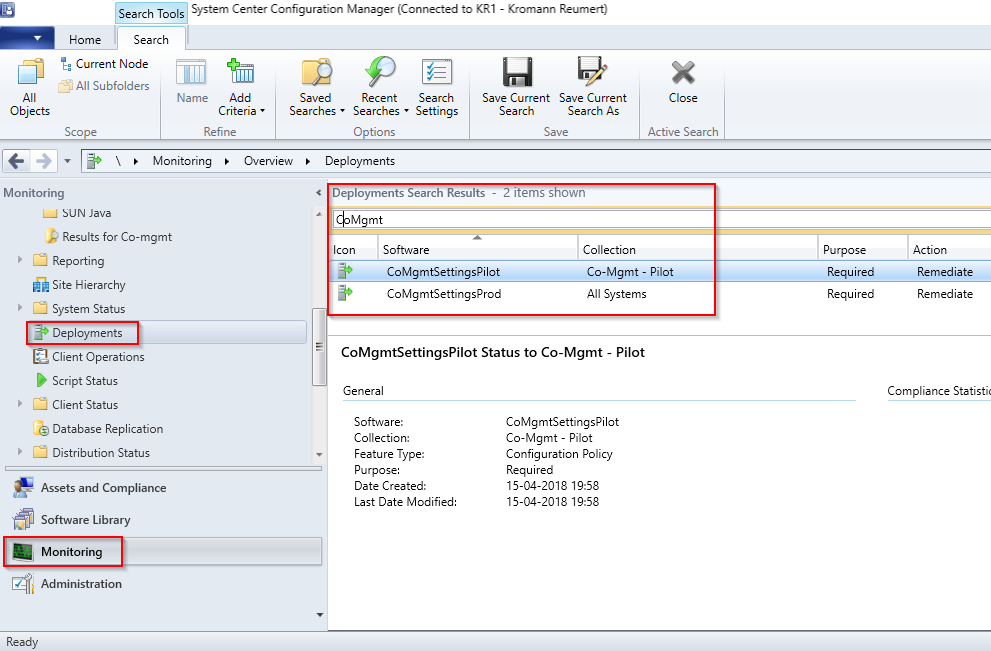
- Right click on your deployment and select Properties. This gives you the option to modify the schedule. By default it runs once a day. Seeing this is a pilot, and you expect to change stuff, I recommend setting this to run more often. I’m running this every hour.
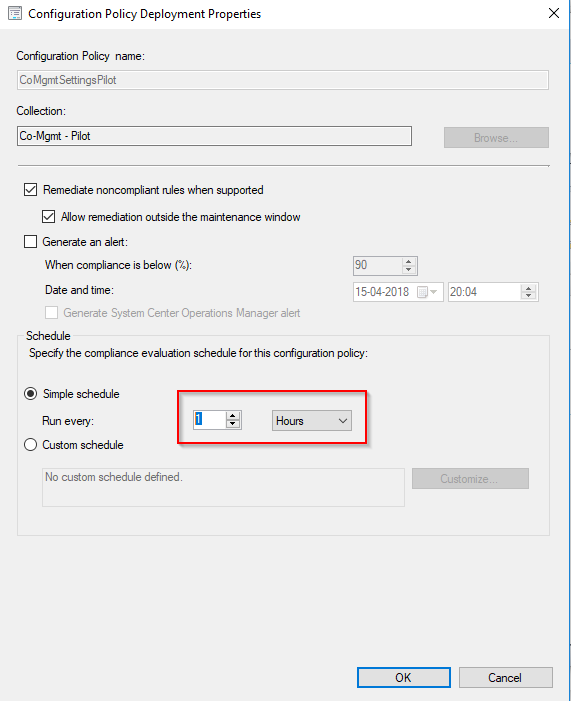
Useful query
Following is a query which will display all the possible information about co-management for all co-managed devices. This can of course be modified to suit any needs, and is currently only displaying those clients that indeed is co-managed. A device is co-managed when the MDMEnrolled field and ComgmtPolicyPresent fields both have a value of 1.
select SMS_R_System.NetbiosName, SMS_Client_ComanagementState.Authority, SMS_Client_ComanagementState.AADDeviceID, SMS_Client_ComanagementState.ComgmtPolicyPresent, SMS_Client_ComanagementState.EnrollmentErrorDetail, SMS_Client_ComanagementState.EnrollmentFailed, SMS_Client_ComanagementState.EnrollmentStatusCode, SMS_Client_ComanagementState.HybridAADJoined, SMS_Client_ComanagementState.MDMEnrolled, SMS_Client_ComanagementState.MDMWorkloads, SMS_Client_ComanagementState.AADJoined from SMS_R_System inner join SMS_Client_ComanagementState on SMS_Client_ComanagementState.ResourceID = SMS_R_System.ResourceId where SMS_Client_ComanagementState.ComgmtPolicyPresent = 1 and SMS_Client_ComanagementState.MDMEnrolled = 1
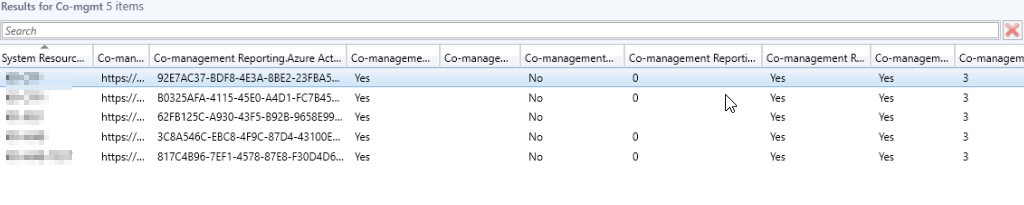
Log file
Client side there is a useful log to monitor as well: C:\windows\ccm\Logs\CoManagementHandler.log
A snip from the same log file during the enrollment of a Windows 10 1709 pc looks like this. (once the configuration policy hits the computer)
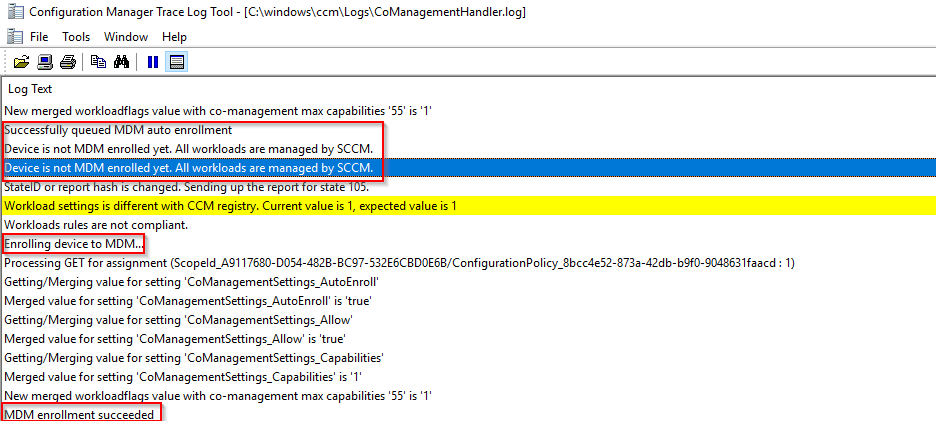
Confirming enrollment
Subject to the Access work or school in Settings you will find the Info button once the computer is fully enrolled into Intune.
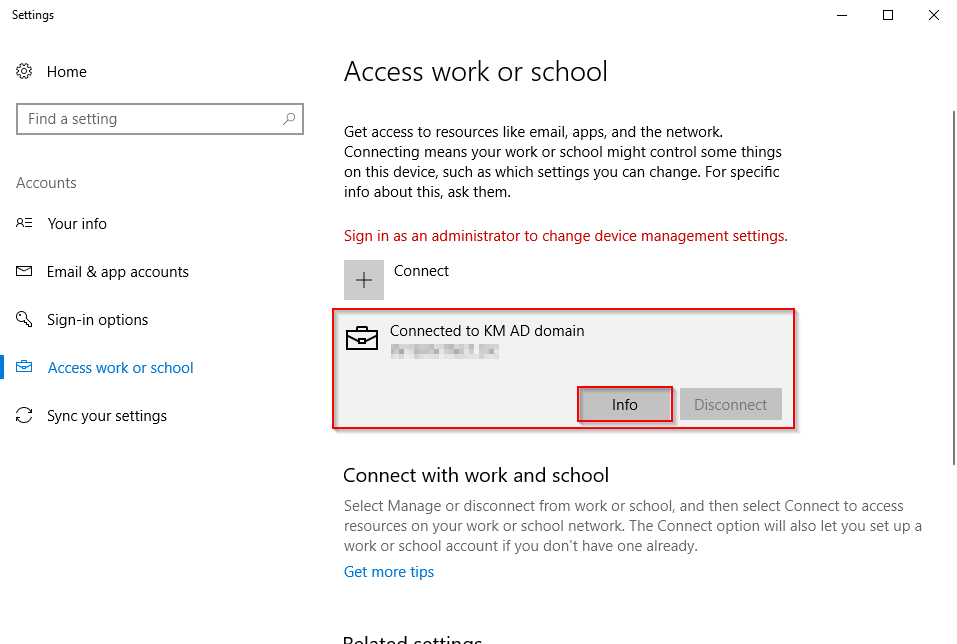
This will display additional information about the enrollment, as well as enabling you to do a manual sync
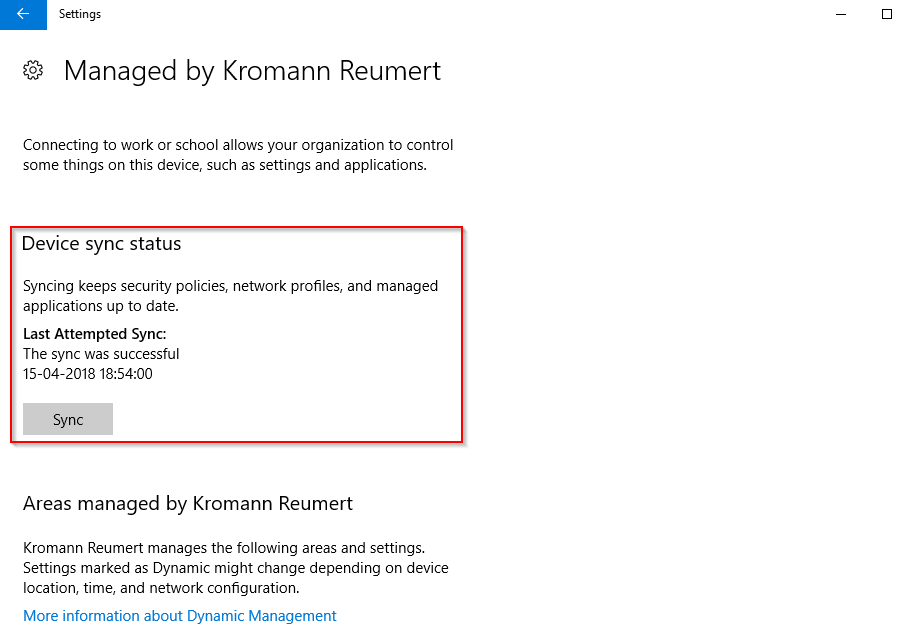
Next up, is to move some more workloads into Intune MDM. Another blog post incoming for that. Currently you can move:
- Endpoint Protection (starting in Configuration Manager version 1802)
- Windows Update policies
- Resource access policies
- Device compliance policies
Please leave a comment, if this was useful 🙂
References:
https://docs.microsoft.com/en-us/sccm/core/clients/manage/co-management-overview
Amazing work!
I am facing a weird issue where SCCM detects my machines as Azure AD Joined instead of Hybrid Azure AD Joined.
Any help appreciated!
https://www.windows-noob.com/forums/topic/16319-sccm-1802-co-management-not-properly-detecting-hybrid-azuread-joined-devices-shows-as-azuread-joined/
Hi I’m confused Auto enrollment can be done via Azure AD and or on-prem AD using GPOs?
With co-management, the device is enrolled into Intune by the ConfigMgr client (assuming you comply with all the prerequisites) 🙂