Introduction
This Friday (Apr 27, 2018) Microsoft announced and acknowledged a new issue with WSUS and Configuration Manager causing clients querying WSUS to consume unexpected high network bandwidth. Everything in details here: https://support.microsoft.com/en-us/help/4163525/high-bandwidth-use-when-clients-scan-for-updates-from-local-wsus-serve
Microsoft has in this regard issued an update that limits how often the Appraiser runs the Windows Update query. To determine if a client has the update (and therefore considered compliant in this regard), you can check the value of a given registry key. As usual, we don’t like to do stuff manually, so how about using Configuration Manager and Powershell? Read on 🙂
Configuration Manager
First off, I’m not covering all the parts required to create a Configuration Item and Configuration Baseline. I have done that several times previously. I’m merely sharing the actual Powershell script I created to determine the actual compliance. The Powershell script is then used with the Configuration Item. I will however, just share the entire CI and CB in a download link 🙂
The explanation given from Microsoft about the registry key and its values, are that if the value is equal to or between 1704 and 1749 or 1752 and above, everything is considered OK (compliant in this regard). So I’m querying the registry key and return either true or false. This can be used to report compliance with a Configuration Item and Baseline.
For testing, I added some output on the screen in terms of Write-Host. Remove the # if you want to test it locally.
$RegistryPath = "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Appraiser"
$ValueOf = Get-ItemProperty -Path $RegistryPath -Name "LastAttemptedRunDataVersion"
$Value = $ValueOf.LastAttemptedRunDataVersion
$Value1 = 1704
$Value2 = 1749
$Value3 = 1752
if (Test-Path -Path $RegistryPath) {
if (($Value -ge "$Value1") -and ($Value -le "$Value2") -or ($Value -ge "$Value3")) {
#Write-Host -ForegroundColor Cyan "Value is equal to or between" $Value1 "and" $value2 "or greater than" $Value3". Value is:" $Value
Return $true
}
else {
#Write-Host -ForegroundColor Cyan "Value is out of the set ranges. Value is:" $Value
Return $false
}
}
else {
#Write-Host -ForegroundColor Cyan "RegistryPath does not exist"
Return $false
}
Download
Download both the CI and CB following this link: https://imab.dk/mab/CompatAppraiserCI-CB.zip
Result
So, download the CI and CB, import it into your Configuration Manager and deploy it to a selected collection (the issue involves Windows 7, 8.1 and all Windows 10 versions), you will immediately (depending on some factors as how often computers refresh their policies) see the compliance count:
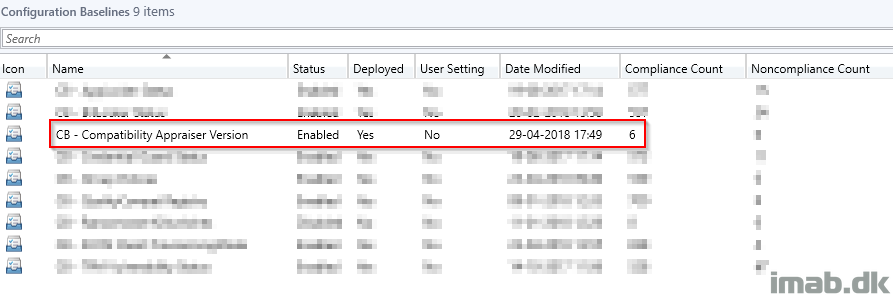
Another preferred method of mine to monitor compliance of a given Configuration Baseline, is to create collections based on the count. You do so by right clicking on the actual deployment of the Configuration Baseline as shown below:
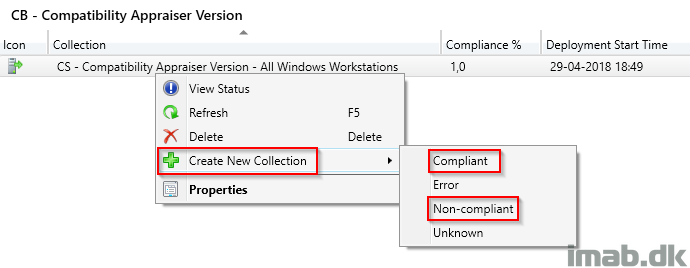
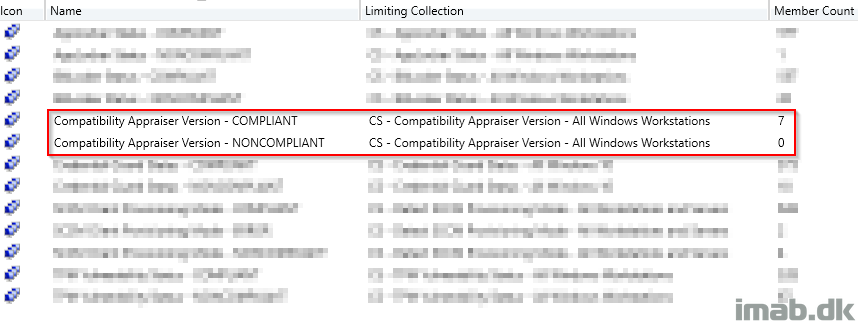
Which will give you collections similar to those shown here:
Final note
Or, you can of course just disable the scheduled task, as mentioned in the article as well. However, that won’t be a great idea if you are using Windows Analytics or planning to use Windows Analytics.
Please share and leave a comment, if this was useful 🙂
References:
https://support.microsoft.com/en-us/help/4163525/high-bandwidth-use-when-clients-scan-for-updates-from-local-wsus-serve