Introduction
Coming Patch Tuesday this month, Microsoft revealed a whooping vulnerability in some infineon TPM chips; ADV170012
In the above article, Microsoft gives us some insight on the vulnerability itself, as well as how to detect and counter the vulnerability.
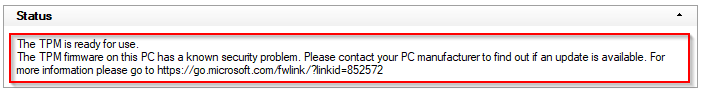
As how to detect the vulnerability, they released a patch which writes an entry to the event log and highlights the vulnerability in TPM.msc.
They also released a Powershell script, which they in turn – unfortunately – don’t go into much details about. They tells us to use PSremoting to query multiple computers and nothing else.
So, how about using ConfigMgr to detect whether our computers are vulnerable or not? Compliance Settings to the rescue!
I rewrote their script to instead return $true or $false, and make it usable to detect compliance or non-compliance.
So, following is my edition of the script, and how to setup the CI in ConfigMgr
Configuration
<#
.DESCRIPTION
Detect if Infineon TPM is vulnerable to Microsoft ADV170012 through Compliance Settings in ConfigMgr
.NOTES
FileName: CIDetectTPM.ps1
Author: Martin Bengtsson
Created: 14-10-2017
#>
$IfxManufacturerIdInt = 0x49465800 # 'IFX'
function IsInfineonFirmwareVersionAffected ($FirmwareVersion)
{
$FirmwareMajor = $FirmwareVersion[0]
$FirmwareMinor = $FirmwareVersion[1]
switch ($FirmwareMajor)
{
4 { return $FirmwareMinor -le 33 -or ($FirmwareMinor -ge 40 -and $FirmwareMinor -le 42) }
5 { return $FirmwareMinor -le 61 }
6 { return $FirmwareMinor -le 42 }
7 { return $FirmwareMinor -le 61 }
133 { return $FirmwareMinor -le 32 }
default { return $False }
}
}
function IsInfineonFirmwareVersionSusceptible ($FirmwareMajor)
{
switch ($FirmwareMajor)
{
4 { return $True }
5 { return $True }
6 { return $True }
7 { return $True }
133 { return $True }
default { return $False }
}
}
$Tpm = Get-Tpm
$ManufacturerIdInt = $Tpm.ManufacturerId
$FirmwareVersion = $Tpm.ManufacturerVersion -split "\."
if (!$Tpm)
{
#No TPM found on this system, so the issue does not apply here."
Return $True
}
else
{
if ($ManufacturerIdInt -ne $IfxManufacturerIdInt)
{
#This non-Infineon TPM is not affected by the issue."
Return $True
}
else
{
if ($FirmwareVersion.Length -lt 2)
{
#Could not get TPM firmware version from this TPM."
Return $True
}
else
{
if (IsInfineonFirmwareVersionSusceptible($FirmwareVersion[0]))
{
if (IsInfineonFirmwareVersionAffected($FirmwareVersion))
{
#This Infineon firmware version {0}.{1} TPM is not safe. Please update your firmware." -f [int]$FirmwareVersion[0], [int]$FirmwareVersion[1])
Return $False
}
else
{
#This Infineon firmware version {0}.{1} TPM is safe." -f [int]$FirmwareVersion[0], [int]$FirmwareVersion[1])
Return $True
}
}
else
{
#This Infineon firmware version {0}.{1} TPM is safe." -f [int]$FirmwareVersion[0], [int]$FirmwareVersion[1])
Return $True
}
}
}
}
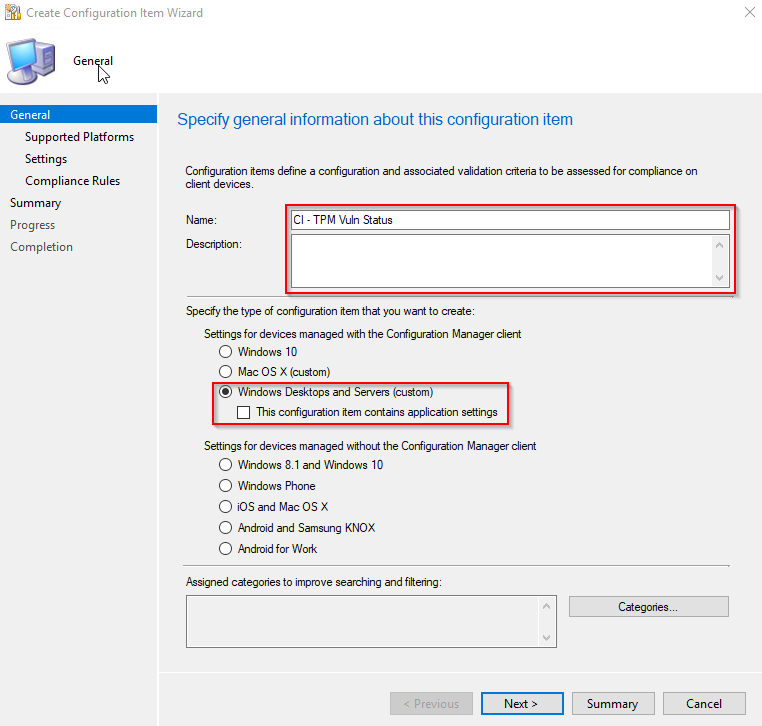
- Create a new CI. Give it a name and enable it to run on all Windows Desktops and Servers (Custom)
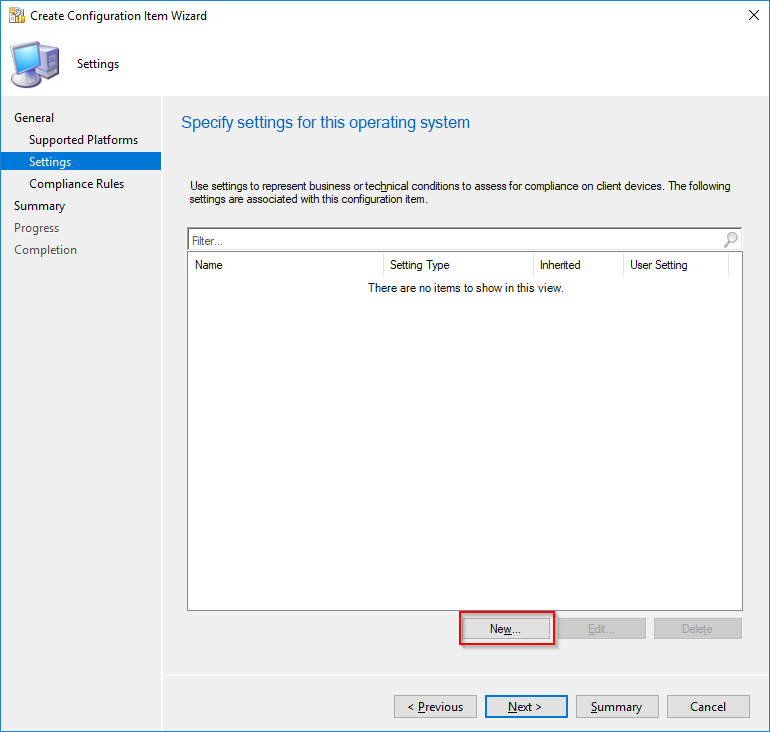
- At the Specify settings for this OS page, click New
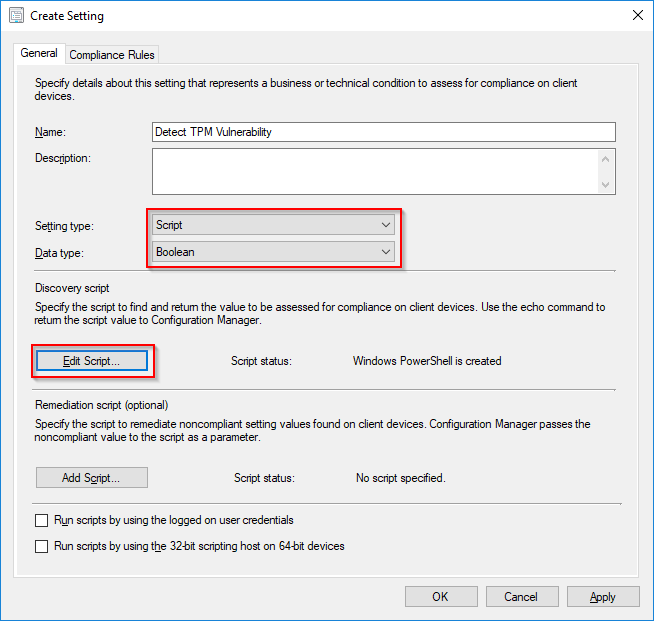
- In the Create Setting page, select Script and Boolean. Insert my script from above in Edit Script
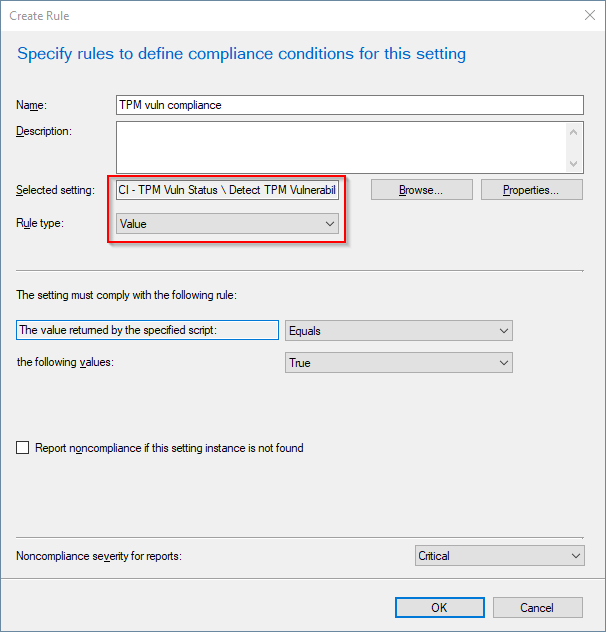
- In the Create Rule page, select the newly created CI
- Add the completed Configuration Item to a Configuration Baseline and deploy to selected collections
Summary
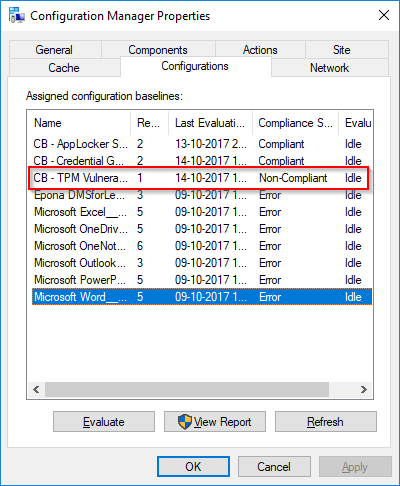
- Taking a closer look directly on the client on the Configurations tab of the ConfigMgr client, you will either notice a compliant or non-compliant state
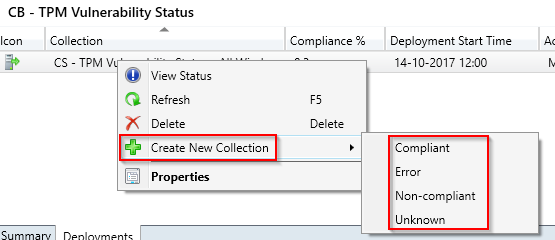
- For a better summary of compliance, I personally like to create collections. Go to the deployment of the Configuration Baseline, and right click. Below is your options to create additional collections
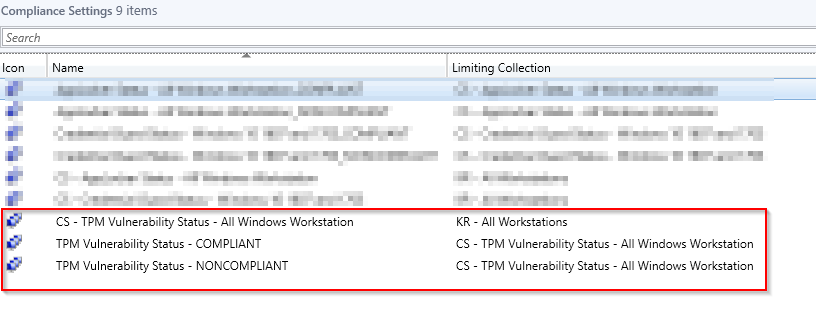
- The net result is a set of collections which memberships clearly tells the compliance state of the TPM vulnerability
Download my CI and baseline here: https://www.imab.dk/mab/CB_TPMVulnerability_Status.zip
Enjoy 😎
Many thanks, this works great except,
the command get-tpm is not availbe in PowerShell 2.0 which is the default on Win 7.
if you replace
$Tpm = Get-Tpm
with
$Tpm = Get-WMIObject –class Win32_Tpm –Namespace root\cimv2\Security\MicrosoftTpm
it will work on 7 and 10