Introduction
This is becoming quite the tradition, and based on the count of views of my previous posts, a popular one indeed. 🙂
I’m a man of traditions, so I’m sticking true to that, and therefore updated my PowerShell script which will enable you to install RSAT for Windows 10 v20H2 automatically and unattended.
The script received some minor changes, and is now also capable of temporarily disabling WSUS, and re-enabling it again post installation.
Over the years and since I created the first script, I have received a lot of comments saying, that if a device is configured to use WSUS, installation of Features on Demand may fail if certain configuration is not in place. So this is another attempt to have the most success with the use of my script.
PowerShell
The script requires administrative rights as well as access to the Internet (RSAT is installed through Microsoft Update).
The script is build around Get-WindowsCapability, Add-WindowsCapability and Remove-WindowsCapability.
The script comes with 5 options:
- -All (-All is installing ALL the features within the RSAT bundle)
- -Basic (-Basic is only installing AD DS, DHCP, DNS, Group Policy Management and Server Manager)
- -ServerManager (-ServerManager is only installing the Server Manager)
- -Uninstall (-Uninstall removes all RSAT features again)
- -DisableWSUS ( -DisableWSUS will disable and re-enable WSUS in the process of installing RSAT)
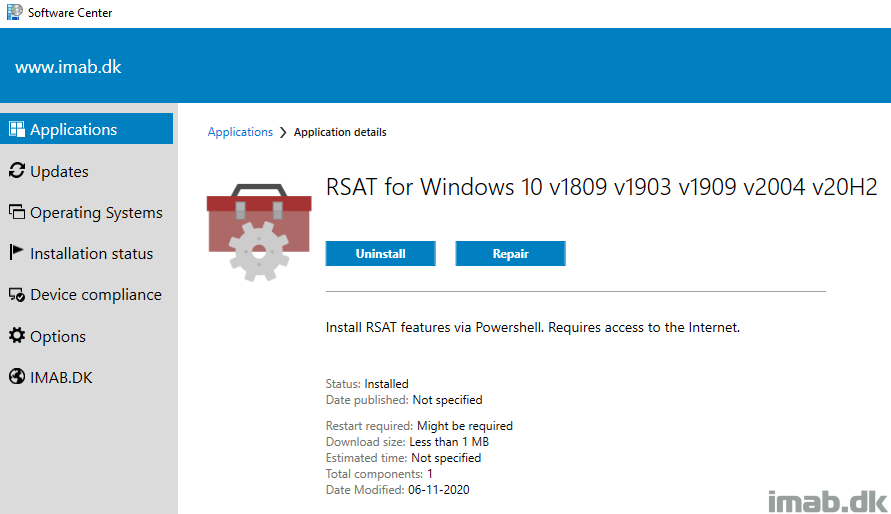
Below an example of running the script manually with the -Basic and -DisableWSUS parameters on Windows 10 v20H2:
Configuration Manager
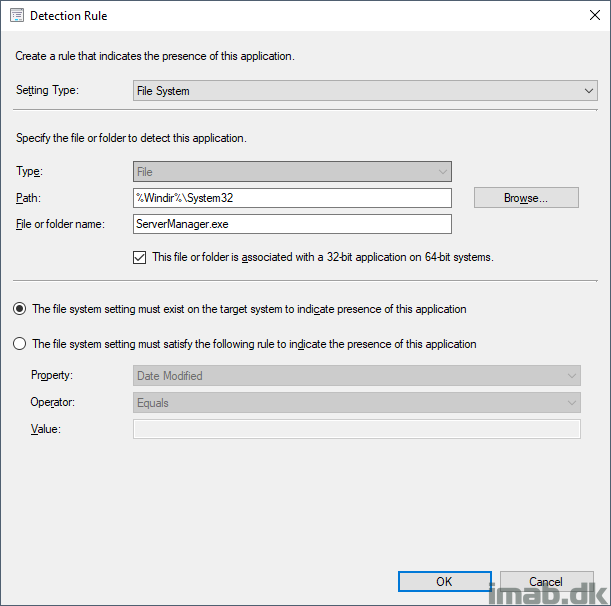
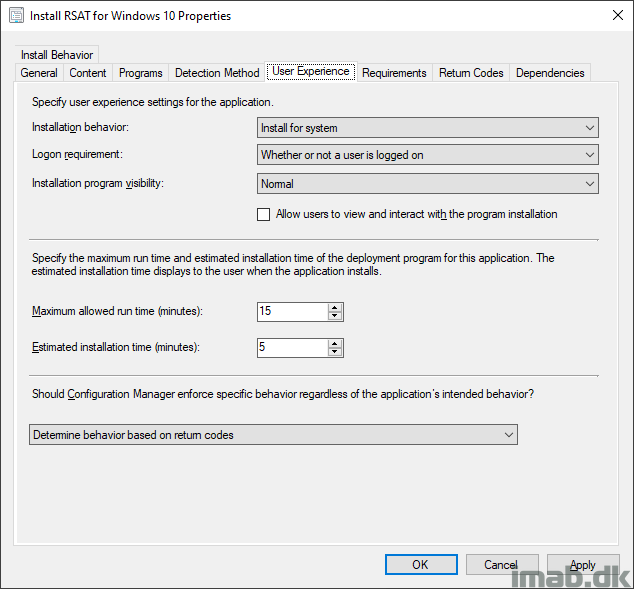
I’m putting the Powershell script to use with an application in ConfigMgr. While this is pretty standard ConfigMgr, I have included a few snippets of the application below.
The installation program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909v2004v20H2.ps1 -Basic
The uninstall program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909v2004v20H2.ps1 -Uninstall
The repair program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909v2004v20H2.ps1 -Basic
Download
The script is now located on my GitHub page: https://github.com/imabdk/Powershell/blob/master/Install-RSATv1809v1903v1909v2004v20H2.ps1
ENJOY 🙂
Hi,
When creating SCCM Application – what type of Application do you select in ‘Create Application Wizard’ window?
I have tried – for me this installation fails. Error: 0x1(1)
https://ibb.co/cX9V1db
Awesome script. I’ve used it more times then I can count now but thought I would let you know that the link at the bottom of this post seems to have a bad version of the script linked to it. If you right click on it and select save as the script fails on line 169 at character 35. But if you go to your GitHub page and get the script from the raw option everything works perfectly.
I’ve heard that before, and I’m not sure why. I usually always, also with anybody else’s scripts go into raw mode and copy/paste from there. Not sure what the browser does when selecting to download 🙁
works like charm !!!
Thanks! Solved my issue of the install failing via the GUI
Thanks for putting this together.
Good Script, works perfect, solved my different requirements.
Thank you
BitLocker management would be a great addition to Basic. Thanks!
This is what I have when I run the script.
VERBOSE: Running correct Windows 10 build number for installing RSAT with Features on Demand. Build number is: 19042
VERBOSE: ***********************************************************
Hi Martin,
Absolutely love this script, would you be able to update it for 21H1 and 21H2?
Thanks!
Will this script work as-is for Win10 21H2, or Win11? Or what needs to be updated in the script for it to work?
How easy would it be to use the Offline Media with this script?
Has anyone managed to get this working with 21H2 yet? It would be great if it could.
I was just looking for something to help with my 21H2 install of RSAT as well. I have tried numerous links and scripts. No luck. Hope to get some assitance with Win 10 21H2 LTSC
If you’re one of the many poor souls like me trying to Google a fix for 21H2, I believe I might have gotten it working:
Under the DisableWSUS parameter, add the following PS lines:
Set-ItemProperty -Path “HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\AU” -Name “UseWuServer” -Value 0
Set-ItemProperty -Path “HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\AU” -Name “UseUpdateClassPolicySource” -Value 0
Set-ItemProperty -Path “HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\” -Name “SetPolicyDrivenUpdateSourceForDriverUpdates” -Value 0
Set-ItemProperty -Path “HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\” -Name “SetPolicyDrivenUpdateSourceForFeatureUpdates” -Value 0
Set-ItemProperty -Path “HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\” -Name “SetPolicyDrivenUpdateSourceForOtherUpdates” -Value 0
Set-ItemProperty -Path “HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\” -Name “SetPolicyDrivenUpdateSourceForQualityUpdates” -Value 0
Set-ItemProperty -Path “HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\” -Name “DisableDualScan” -Value 0
In any of the script blocks that re-enable the WSUS settings, set those values to 1. I was able to successfully run this script on a Windows 10 22H2 VM and install my desired RSAT tools.
I haven’t yet tested this on Windows 11, but I imagine it would work. Also, I take no responsibility for breaking your crap if you try this.
For all those who use the script and have had problems since 22H2, here is a tip:
under this line:
Set-ItemProperty -Path “HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\AU” -Name “UseWuServer” -Value 0
add this line:
New-ItemProperty -Path “HKLM:\Software\Microsoft\Windows\CurrentVersion\Policies\Servicing” -Name “RepairContentServerSource” -Value 2
and to remove this setting setover this line:
Set-ItemProperty -Path “HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\AU” -Name “UseWuServer” -Value 1
add this line:
Remove-ItemProperty -Path “HKLM:\Software\Microsoft\Windows\CurrentVersion\Policies\Servicing” -Name “RepairContentServerSource” -Force
This Setting:
https://admx.help/?Category=Windows_10_2016&Policy=Microsoft.Policies.Servicing::Servicing