Introduction
NOTE: Script has been updated for v20H2 (2009): https://www.imab.dk/deploy-rsat-remote-server-administration-tools-for-windows-10-v20h2-using-configmgr-and-powershell/
I’m a little late to the 2004 party this time around, but nevertheless, I just found time to update my Powershell script, which will enable you to install RSAT for Windows 10 v2004 automatically and unattended.
Windows 10 v2004 was released to MSDN users early in May and to VLSC customers 2 weeks later. True to tradition, I’m showing you how you can leverage my script to install the RSAT features with Configuration Manager.
The script received a minor update, and is now also logging its actions into a local log file in C:\Windows\Install-RSATfeatures.log.
The script has now moved away from TechNet Gallery into my GitHub page: https://github.com/imabdk
Powershell
The script requires administrative rights as well as access to the Internet (RSAT is installed through Microsoft Update).
The script is build around Get-WindowsCapability, Add-WindowsCapability and Remove-WindowsCapability.
Yet again the script comes with 4 options:
- -All (-All is installing ALL the features within the RSAT bundle)
- -Basic (-Basic is only installing AD DS, DHCP, DNS, Group Policy Management and Server Manager)
- -ServerManager (-ServerManager is only installing the Server Manager)
- -Uninstall (-Uninstall removes all RSAT features again)
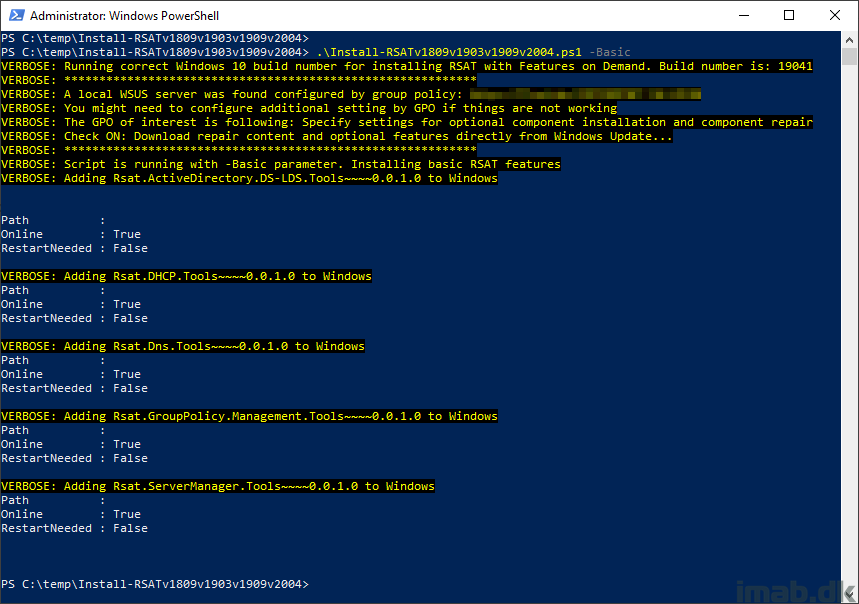
Below an example of running the script manually with the -Basic parameter on Windows 10 2004
Configuration Manager
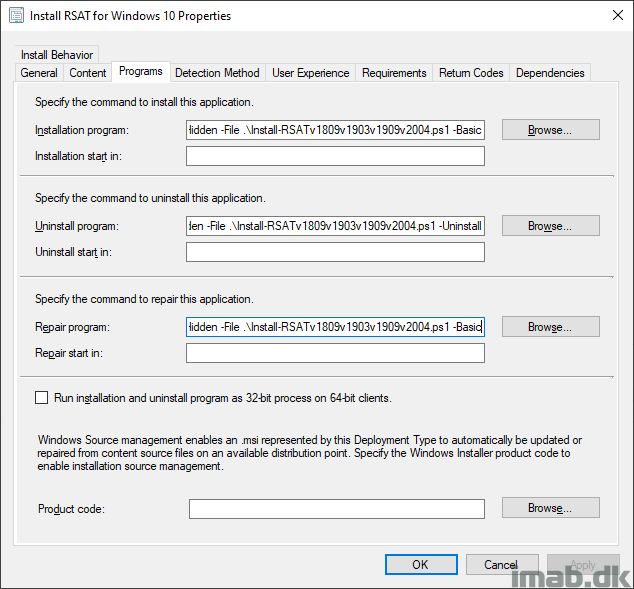
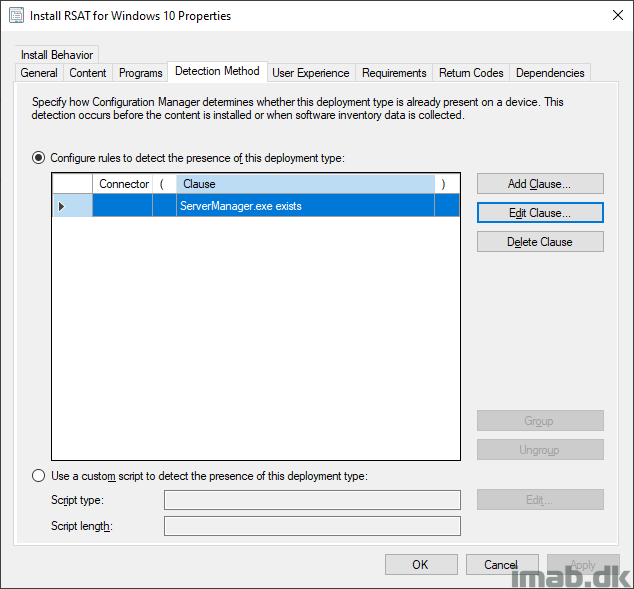
I’m putting the Powershell script to use with an application in ConfigMgr. While this is pretty standard ConfigMgr, I have included a few snippets of the application below.
The installation program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909v2004.ps1 -Basic
The uninstall program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909v2004.ps1 -Uninstall
The repair program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909v2004.ps1 -Basic
Download
The script is now located on my GitHub page: https://github.com/imabdk/Powershell/blob/master/Install-RSATv1809v1903v1909v2004v20H2.ps1
ENJOY 🙂
not working
What does that mean? What is not working? 🙂
It seems that I had a problem with the Internet, today everything worked out. many thanks
I was unable to install the RSAT with the PS script but, I found the solution:
Step 1 : Open Regedit, GOTO:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU
Put UsewWUServer to : ‘0’
Step 2 : Go to services.msc and restart the windows update service
Step 3 : run the script
All worked fine!
@Martin Bengtsson : do you think that it will be fine to add this prerequisites in the script?
Right, that can be necessary in some environments. I will include that into the script as an option 🙂 Thanks.
Thats a typical “user” statement… not working. You are to magically know what the error, or what the problem is, and then fix it!
Ha! So true 🙂
Hello,
Do we need to have windows update configured in group ?
Last time we created a similar script it didnt work, It worked after below setting
• Navigate to Computer Configuration\Administrative Templates\System
• Double click on Specify settings for optional component installation and component repair
• Check the “Enabled” radio button
• Check “Download repair content and optional features directly from Windows Update instead of Windows Server Update Service (WSUS)”
Any work around for this
That’s the exact same setting I’m referring to in the actual script. Personally I don’t have any issues, but I have received a lot of feedback saying, that if certain configurations are made on the computer, that setting might be required in order to install RSAT as a Feature on Demand.
Thank you so much. Work like a charm 🙂
Thank you! 🙂
Hello,
I am seeing this with any install:
VERBOSE: Adding Rsat.GroupPolicy.Management.Tools~~~~0.0.1.0 to Windows
Write-Log : Missing an argument for parameter ‘Message’. Specify a parameter of type ‘System.String’ and try again.
At C:\temp\Install-RSATv1809v1903v1909v2004.ps1:212 char:31
+ Write-Log -Message -Level Warn “Failed to add $Rs …
+ ~~~~~~~~
+ CategoryInfo : InvalidArgument: (:) [Write-Log], ParameterBindingException
+ FullyQualifiedErrorId : MissingArgument,Write-Log
Hello, seems like I screwed up the logging for when hitting the catch block. This has been corrected in the script on GitHub. However, you are likely to encounter the issue again, as something locally on your device seems to be preventing the addition of the individual features on demand. The script should log the correct error message now.
We had a lot of issues with downloading from windows update.
Instead of creating yet another gpo, I solved it by creating a folder for each windows build, and extracting the fod iso corresponding to the various builds.
Then I added -Source “location of $build fod files” -LimitAccess to the add-windowscapability command-line.
Yeah, that’s on my to do as well, to allow local source for that scenario 🙂 Thank you!
Hi 🙂
We have tried your script, thanks for that, nice to see a Dane in a good tech blog 🙂
Ok when running the script we got an 0x800f0954 error, so we set these settings as suggested above:
“Navigate to Computer Configuration\Administrative Templates\System
• Double click on Specify settings for optional component installation and component repair
• Check the “Enabled” radio button
• Check “Download repair content and optional features directly from Windows Update instead of Windows Server Update Service (WSUS)””
But then we just get a 0x8024002e error instead, have anyone experienced that?
We are running a Wsus server.
Having issues with your script. I run the script in admin Powershell, but all it does is display the local WSUS lines, nothing else. I modified the Group Policy and ran GPUPDATE /Force but still noting. Thanks for any help
Getting a bunch of errors regarding & symbol.
At C:\temp\Install-RSATv1809v1903v1909v2004.ps1:148 char:21
+ Sign up
+ ~
The ampersand (&) character is not allowed. The & operator is reserved for future use; wrap an ampersand in double
quotation marks (“&”) to pass it as part of a string.
At C:\temp\Install-RSATv1809v1903v1909v2004.ps1:175 char:190
+ … ata-ga-click=”(Logged out) Header, go to Features”>Features <span cla …
+ ~
The '→Customer stories <span cla …
+ ~
The '→Security <span cla …
+ ~
The '→Explore GitHub <span cla …
+ ~
The '→Learn & con …
+ ~
The ampersand (&) character is not allowed. The & operator is reserved for future use; wrap an ampersand in double
quotation marks (“&”) to pass it as part of a string.
Not all parse errors were reported. Correct the reported errors and try again.
+ CategoryInfo : ParserError: (:) [], ParseException
+ FullyQualifiedErrorId : AmpersandNotAllowed
You must have copied too much from GitHub and not just the script itself. Get into the Raw piece of the script and copy from there instead 🙂
Actually I didn’t copy anything at all. Just right-clicked on the link for the script and clicked “Save Link As” which downloaded the script, and then I ran it. (saved from https://github.com/imabdk/Powershell)
However I just tried opening the script and copying and pasting into Notepad. That seems to have worked. Weird that just saving it, apparently broke it.
Happy that it’s working 🙂
Just to back this up, when I right-clicked the link for the script and clicked “Save Link As”, it downloaded the PS1 file but I got all the same errors as John. When I copied the actual code and pasted it into a notepad file and saved it as the PS1 script, it worked just fine.
Thanks for letting me know. Must be something in GitHub or related to the browser. I don’t think I can upload the script in any other fashion.
FYI, if you are in an environment where the GPO “Specify settings for optional component installation and component repair” is not set and you do have a WSUS server set. This script will detect the WSUS server and notify you. I have modified the script based on that detection, for my purposes to enable the registry key for that GPO and to temporarily tell the PC not to use the WSUS server. This enables the install every time.
Example:
********************************************
if ($WUServer -ne $null) {
Write-Log -Message “A local WSUS server was found configured by group policy: $WUServer”
Write-Log -Message “You might need to configure additional setting by GPO if things are not working”
Write-Log -Message “The GPO of interest is following: Specify settings for optional component installation and component repair”
Write-Log -Message “Check ON: Download repair content and optional features directly from Windows Update…”
Write-Log -Message “Running commands to enable FoD for this install session”
Write-Log -Message “***********************************************************”
New-ItemProperty -Path HKLM:\Software\Microsoft\Windows\CurrentVersion\Policies\Servicing -Name RepairContentServerSource -Value 2 -PropertyType DWord
Set-ItemProperty -Path HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU -Name UseWUServer -Value 0
Restart-Service -Name wuauserv
********************************************
This creates the registry key for the GPO if it does not exist and fails if it already exists but continues. Next GPO enforcement will set it back, but a good enough window to get the online download going. It also disables the UseWUServer and restarts the WUAUSERV service so you go out to the internet instead of your local WSUS. Following each potential conclusion you should set this back.
Exmaple:
*****************************************
if ($PSBoundParameters[“All”]) {
Write-Log -Message “Script is running with -All parameter. Installing all available XPS features”
$Install = Get-WindowsCapability -Online | Where-Object {$_.Name -like “XPS*” -AND $_.State -eq “NotPresent”}
if ($Install -ne $null) {
foreach ($Item in $Install) {
$XPSItem = $Item.Name
Write-Log -Message “Adding $XPSItem to Windows”
try {
Add-WindowsCapability -Online -Name $XPSItem
}
catch [System.Exception] {
Write-Log -Message “Failed to add $XPSItem to Windows” -Level Warn
Write-Log -Message “$($_.Exception.Message)” -Level Warn
}
}
Set-ItemProperty -Path HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU -Name UseWUServer -Value 1
Restart-Service -Name wuauserv
}
else {
Write-Log -Message “All XPS features seems to be installed already”
Set-ItemProperty -Path HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU -Name UseWUServer -Value 1
Restart-Service -Name wuauserv
}
}
***************************************
I have modified this script to work for other FoD like XPS writer, etc. and it works perfectly. Thank you Martin!
I get this Failed error for each component being installed:
Adding Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows
WARNING: Failed to add Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows WARNING: Add-WindowsCapability failed. Error code = 0x800f0907
I did set “Download repair content and optional features directly from Windows Update” to enabled. We do have WSUS. Is it possible that my organization is blocking Windows Update servers? Thank you.
Hi,
Thank.
Is there a way to install it offline ?
Could you please provide us the nice RSAT icon ?
Thanks 🙂
Tried several times to just download the actual .PS! file with the script, but kept getting a ton of extra text in the .PS1 file not related to the RSAT install. I’m guessing it must have been saving the GitHub link/context and not the actual PS script itself. Would love to see updates continue to post to the Microsoft site, when we can easily download the actual PS script itself. Way less confusing than navigating to the script in GH.
I ended up copying the script content and making my own PS1 file just to get past this.
Appreciate the script however!
Thank you so much for this script!
It worked flawlessly on my company machines.
You have to wonder why Microsoft made is so hard to install these tools, since it requires both this script and messing with the local GPO regarding our configured WSUS server.
Getting the following error:
[D] Do not run [R] Run once [S] Suspend [?] Help (default is “D”): R
VERBOSE: Running correct Windows 10 build number for installing RSAT with Features on Demand. Build number is: 19041
VERBOSE: ***********************************************************
VERBOSE: A local WSUS server was found configured by group policy: http://ProdPatch01.cdd.loc:8530
VERBOSE: You might need to configure additional setting by GPO if things are not working
VERBOSE: The GPO of interest is following: Specify settings for optional component installation and component repair
VERBOSE: Check ON: Download repair content and optional features directly from Windows Update…
VERBOSE: ***********************************************************
VERBOSE: Script is running with -Basic parameter. Installing basic RSAT features
VERBOSE: Adding Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows
WARNING: Failed to add Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024002e
VERBOSE: Adding Rsat.DHCP.Tools~~~~0.0.1.0 to Windows
WARNING: Failed to add Rsat.DHCP.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024002e
VERBOSE: Adding Rsat.Dns.Tools~~~~0.0.1.0 to Windows
WARNING: Failed to add Rsat.Dns.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024002e
VERBOSE: Adding Rsat.GroupPolicy.Management.Tools~~~~0.0.1.0 to Windows
WARNING: Failed to add Rsat.GroupPolicy.Management.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024002e
VERBOSE: Adding Rsat.ServerManager.Tools~~~~0.0.1.0 to Windows
WARNING: Failed to add Rsat.ServerManager.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024002e
Works out of the box, thank you very much for your efforts!
Thx, works exactly as stated.
Great script, thanks a lot for your efforts!
The -disableWSUS feature works great when RSAT is not installed yet.
However, if the PS gets executed with -disableWSUS parameter when RSAT is already installed, the regkey is set to 0 but not set back to 1. Only a ‘already installed’ message appears, but the reg key doesn’t get touched again.
I would appreciate if you could improve that in your next release.
Oh snap. Let me fix that asap. And sorry about that – thought I tested all the scenarios. Will fix asap, possibly tonight and let you know. Thanks!
Genius. Tak og glædelig jul!
Thanks for your work! Should this run fine in Windows 11 as well?