Introduction
I’m currently working on getting my Windows 11 devices CIS (CIS Center for Internet Security (cisecurity.org) compliant in regards to their benchmark. This takes some effort, especially if you don’t use Group Policy anymore. 🙂
- For those who don’t know CIS benchmarks, get more details here: CIS Benchmarks (cisecurity.org) and here: Center for Internet Security (CIS) Benchmarks – Microsoft Compliance | Microsoft Docs
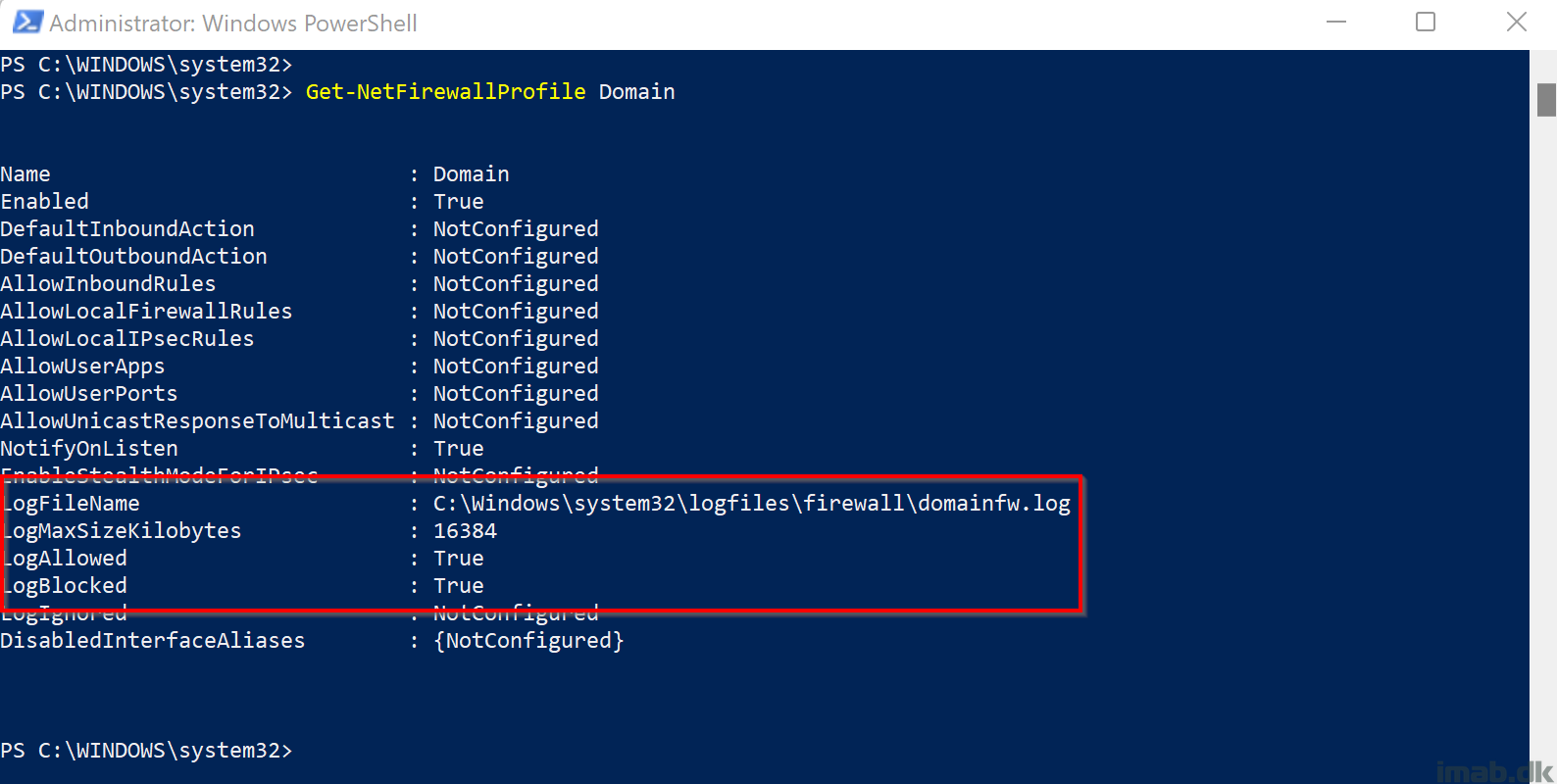
The CIS Benchmark for Microsoft Windows 11 Enterprise dictates that logging for Windows Firewall is enabled, and is configured with certain settings. None of those settings, at the time of writing, are available natively via Intune, so I have chosen to resort to PowerShell and Proactive Remediations.
My scripts will create each log file, for each firewall profile: Domain, Private, Public and make sure those log files are configured with the correct permissions (otherwise the Defender engine won’t have permissions to write to the files). Firewall logging will then be enabled with the recommended values.