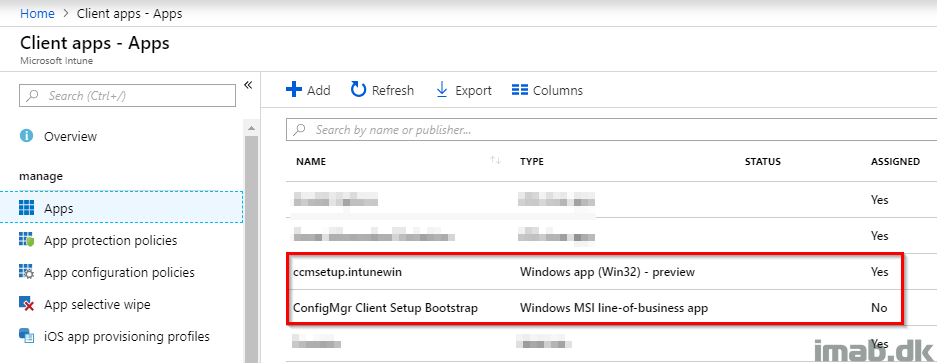
Introduction
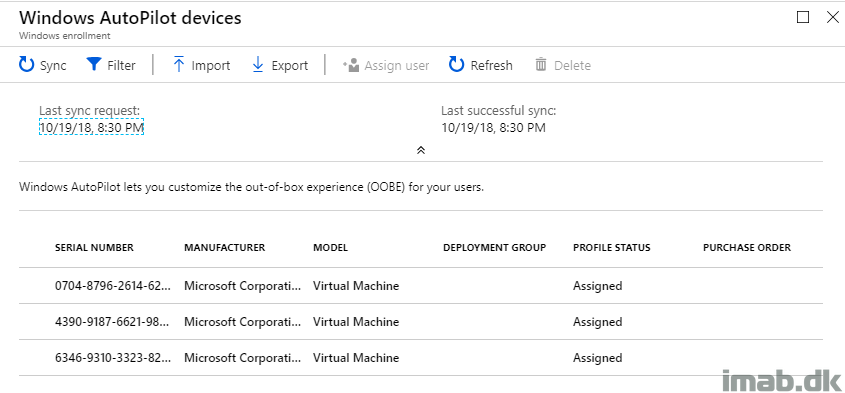
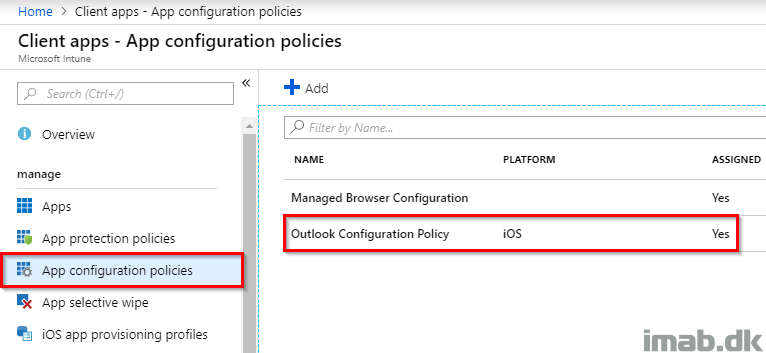
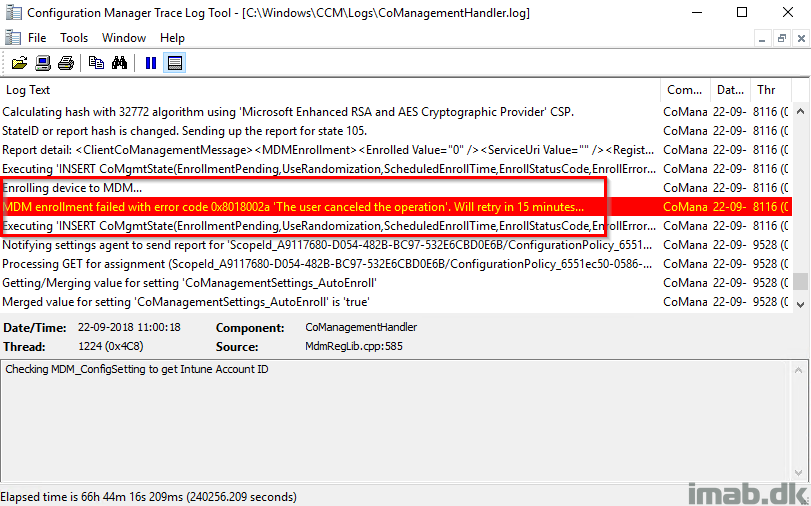
Last week I blogged about how to get properly started with Windows AutoPilot. This week I’m continuing on the topic, and going into details on how you can deploy the SCCM (System Center Configuration Manager) client as a part of the Windows AutoPilot enrollment and thus achieve Co-management with SCCM and Microsoft Intune.
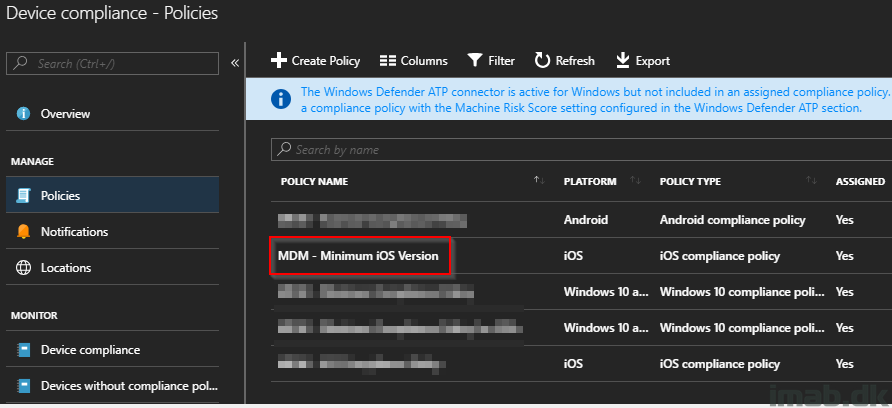
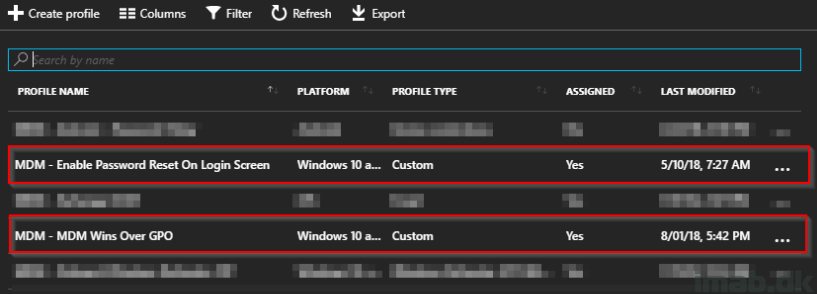
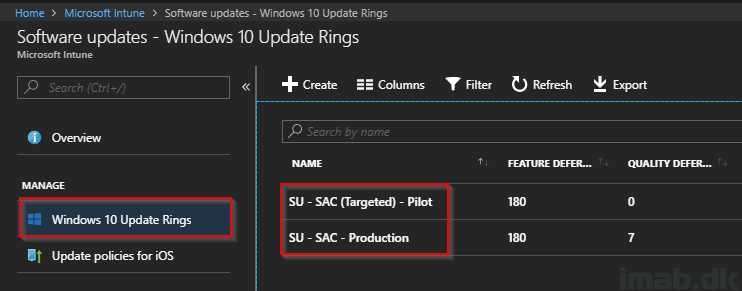
I have previously blogged a lot about Co-management. Focus here has been enrolling devices already managed by SCCM into Intune MDM.
This post is the opposite. This time we are deploying a device through Windows AutoPilot, enrolling it into Microsoft Intune and then deploying the SCCM client through the Cloud Management Gateway. Sounds interesting? Read on 🙂
- Find all my Co-management posts here: https://www.imab.dk/category/co-mgmt/
- My post about setting up the Cloud Management Gateway without PKI certificates is especially of interest if pursuing Co-management