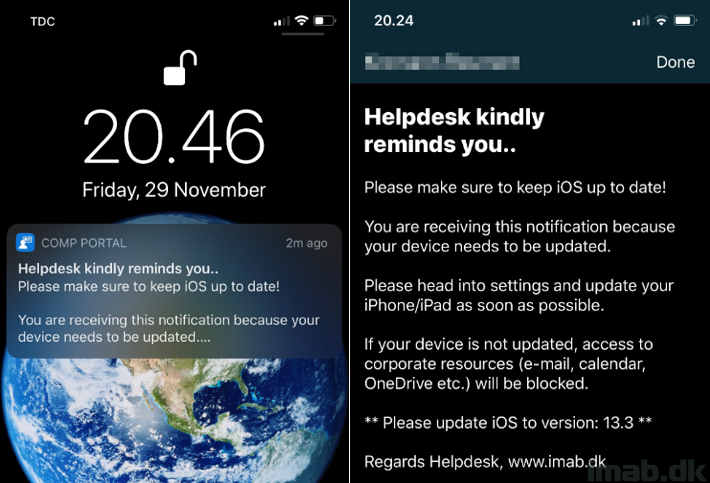
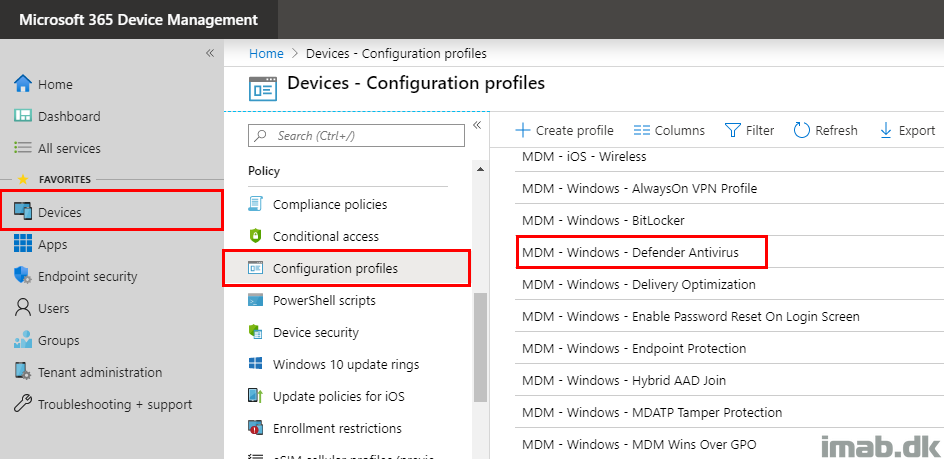
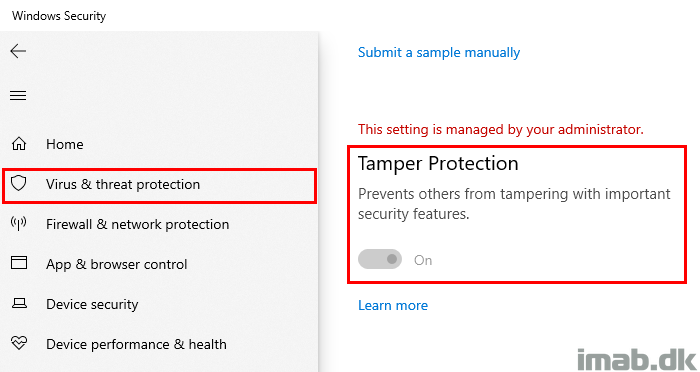
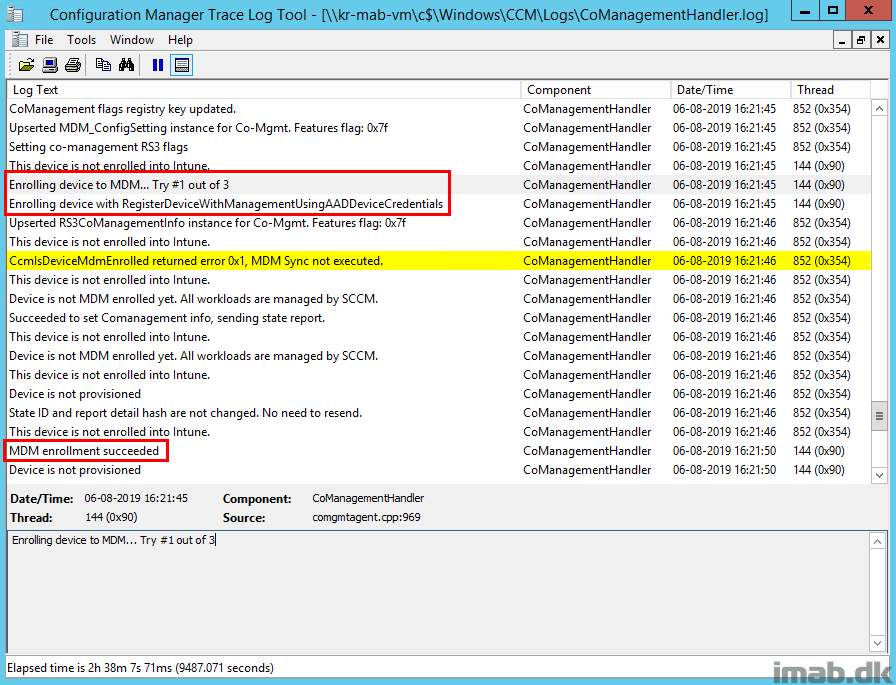
Introduction
This is the first and initial blog post of an upcoming series, all concerning how one can secure their endpoints using Microsoft Intune.
The posts are meant to serve as titbits, quickly giving the reader an understanding of a specific feature.
The posts are not released in any particular order, and the topics discussed are based on what I’m currently looking into, in my own environment.
Therefore and as usual, this is not a typical and standard walk through, but more a look into how I’m initially taking on the discussed topic. Curios? Read on! 🙂