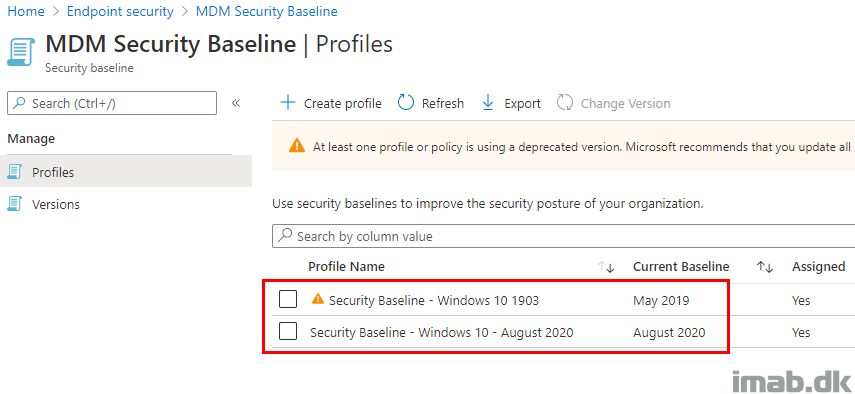
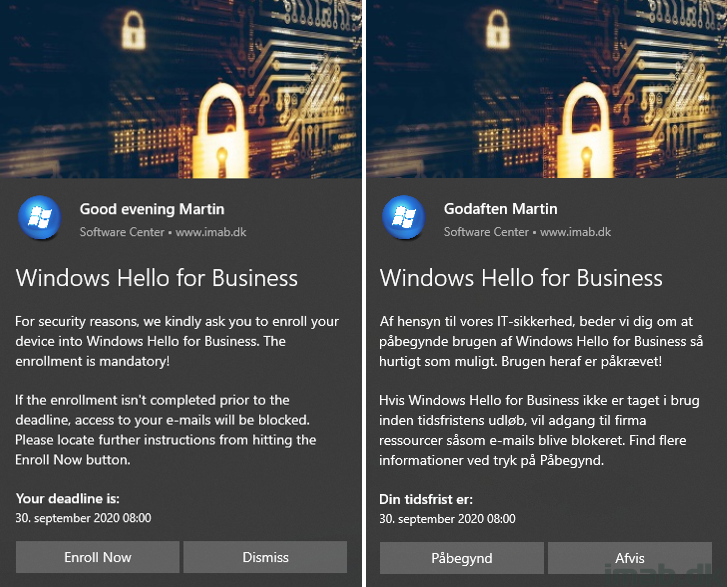
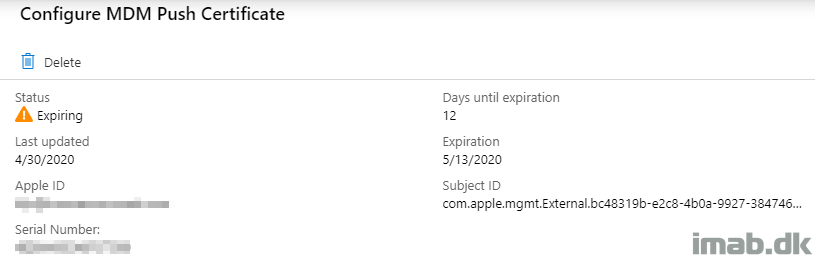
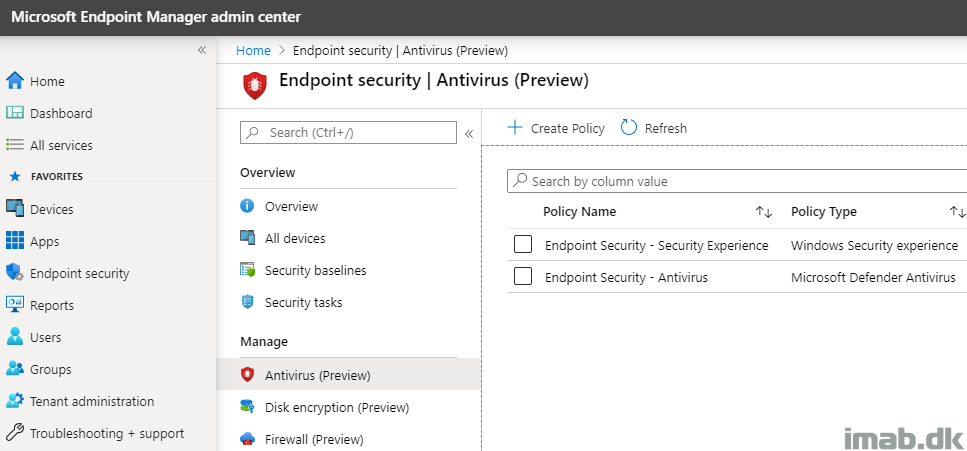
Introduction
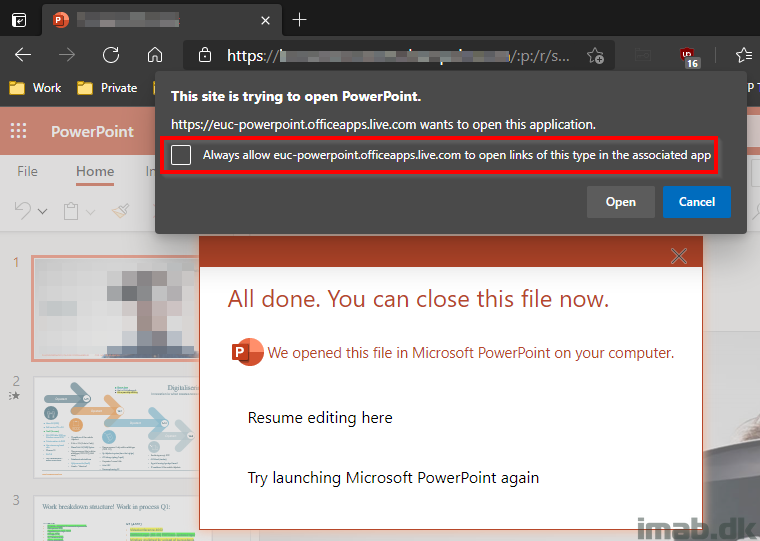
This is just a really quick post, describing how you configure Microsoft Edge to always – and without prompting the user – open certain links in their associated application.
This might seem like an odd and out of the ordinary post, but I needed this myself, and failed to find the relevant details described properly anywhere.
The mentioned prompt is something that’s generated when opening links to Teams meetings, or when trying to open Office documents in their respective desktop application.
Prompts which in most cases are irrelevant to the end-users, and by eliminating those, the user-experience is improved by a little. TL:DR down below.