Introduction
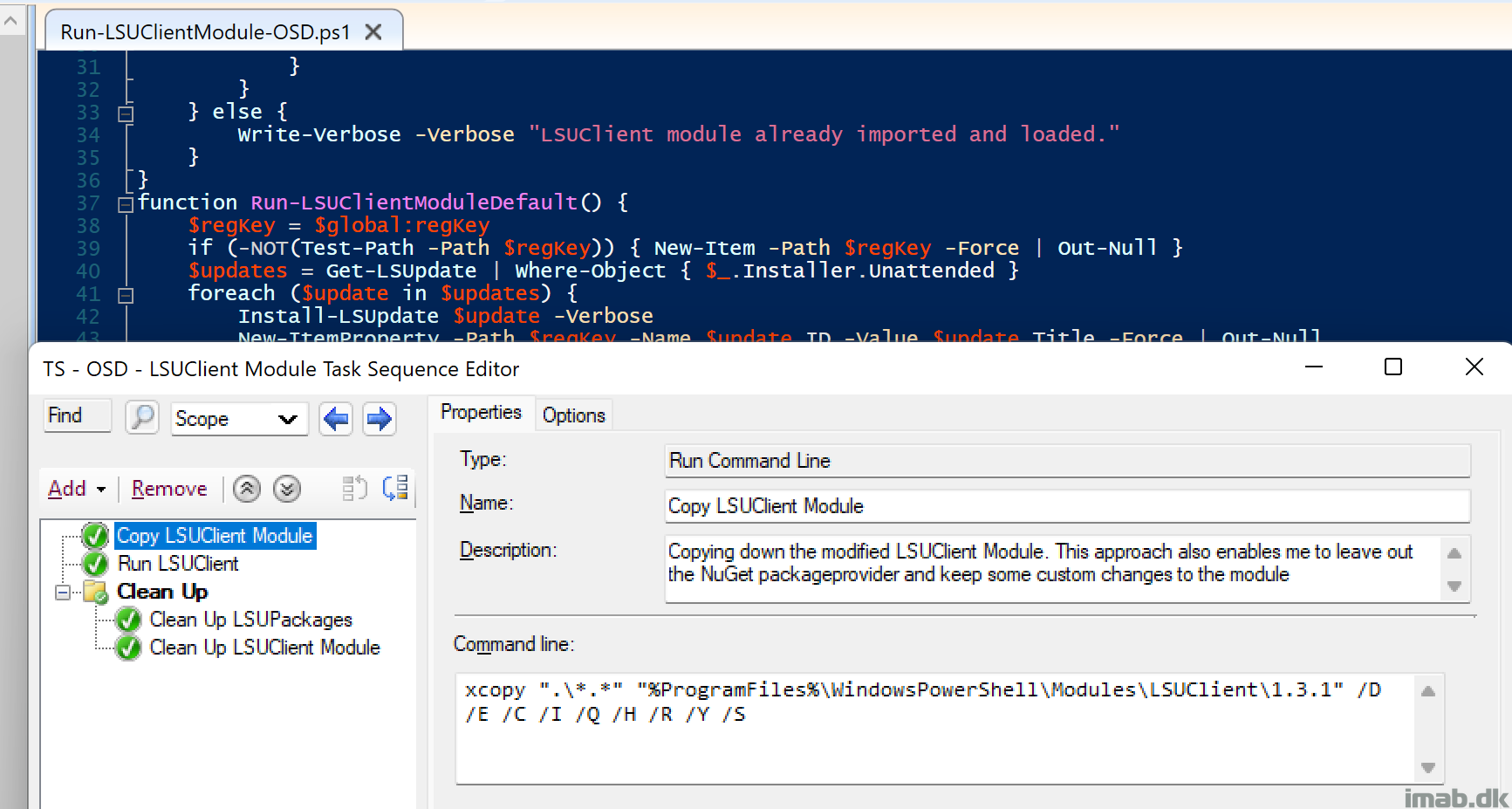
This is something that I’ve wanted to do for a while; to always install the latest BIOS and drivers automatically during OSD.
Keeping BIOS and driver versions up to date, can be a tedious and time consuming task, and I wanted to take on a more cloud-like approach.
For that reason, I’ve spent some time on Lenovo Thin Installer as well as Lenovo System Update, but they didn’t quite live up to my expectations and need for flexibility.
Instead – and by coincident – I stumbled upon this awesome PowerShell module: jantari/LSUClient
It does exactly what Thin Installer and System Update offers, as well as giving you the flexibility of PowerShell. What’s not to like?