Introduction
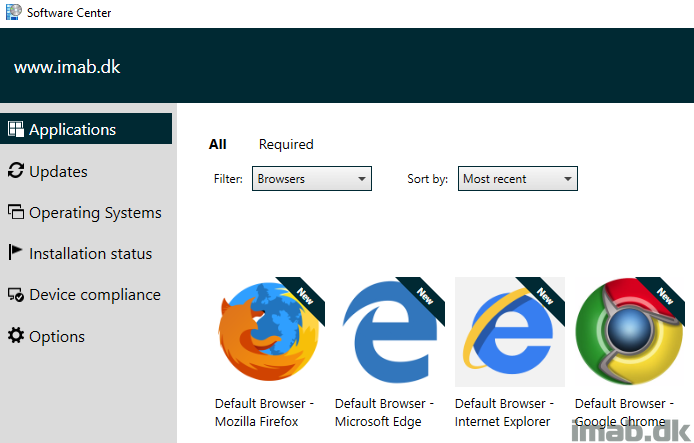
In this post I will talk about Windows 10, file associations and how you can let the user in an enterprise switch default browser through the Software Center in SCCM (System Center Configuration Manager). All of this is done in an environment where file associations are tightly managed and locked through group policies (as they should be in an enterprise) on computers running Windows 10. Curious on the topic? Read on