Introduction
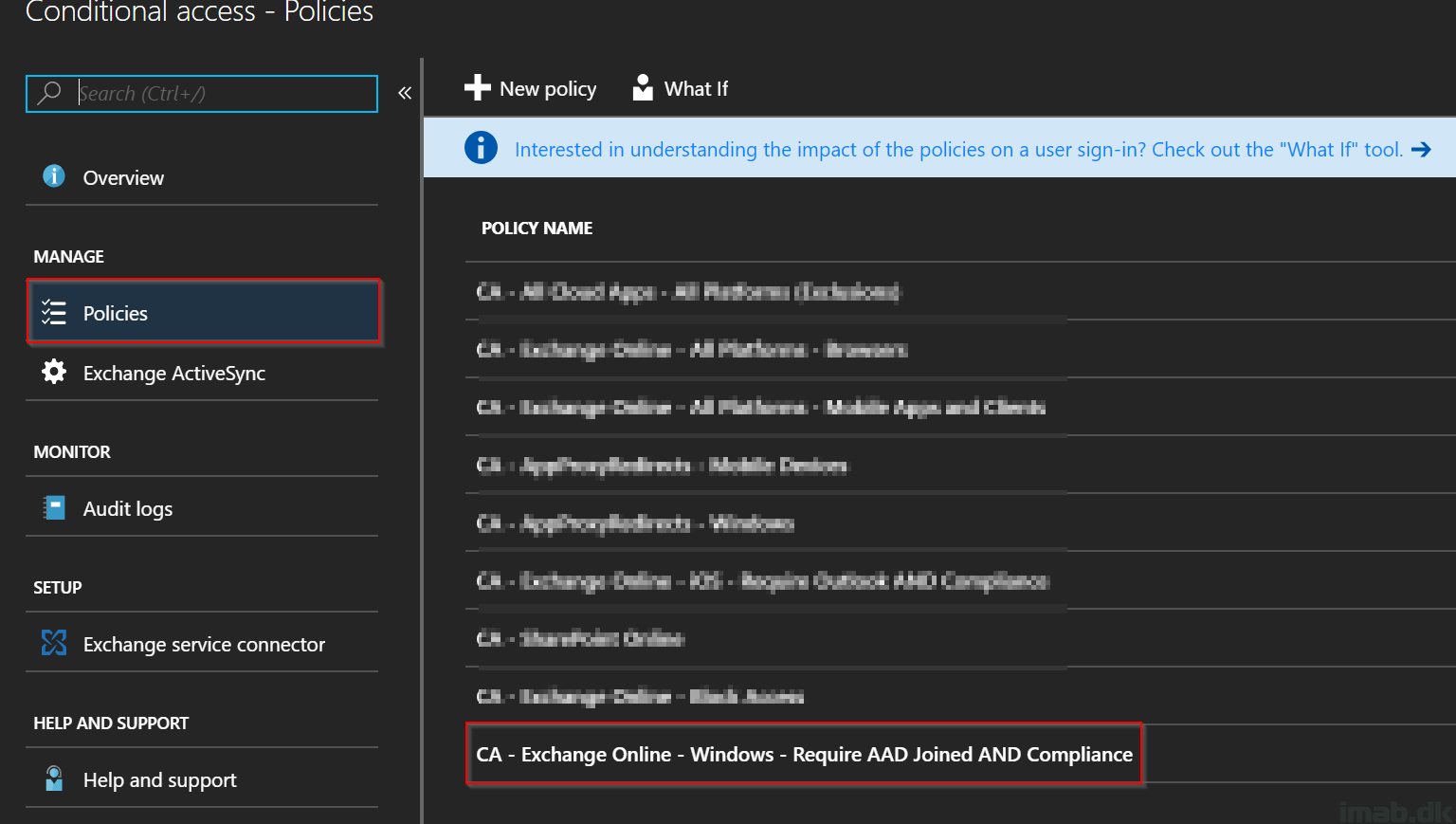
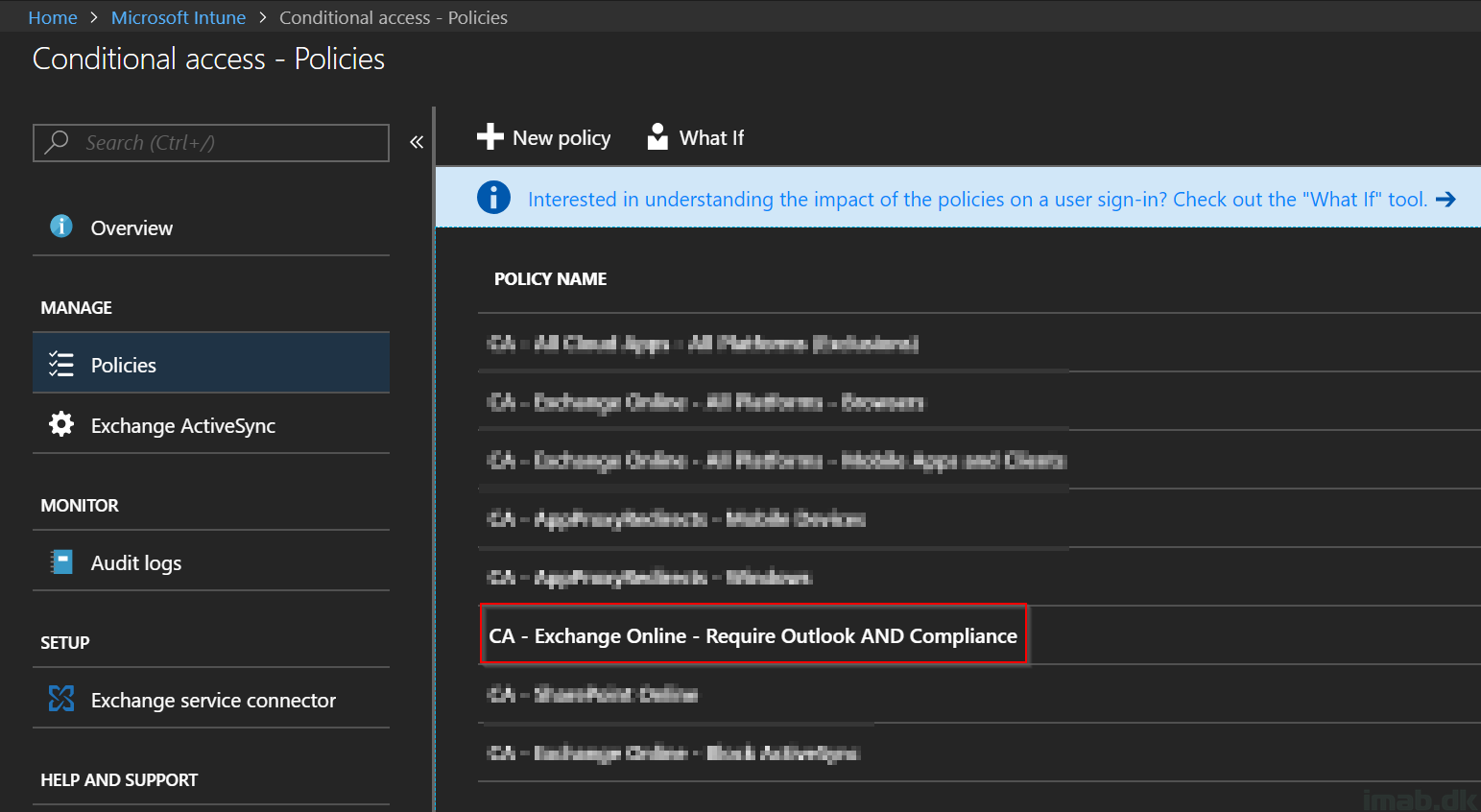
Last week I gave an example on how to leverage Microsoft Intune and Conditional Access to restrict access to Exchange Online for iOS devices. This week, I’m continuing the use of Microsoft Intune and Conditional Access, and will give an example on how to restrict access to company e-mail if not using a Windows 10 1803 device. All of this based on a computer co-managed with both Microsoft Intune and Configuration Manager.
So basically; no e-mails if not running on the latest and greatest version of Windows 10 on my co-managed device.